A practical continuity plan ties people, processes, and technology together—so recovery is predictable instead of hopeful. Far too often, organizations treat business continuity as a one-time documentation exercise or a compliance box to check once per year. They create a binder, save a PDF somewhere, distribute a few emails, and assume they’re prepared because the document exists.
But when an actual outage, cyberattack, or system failure hits, the reality becomes obvious: the binder doesn’t restore servers, reconnect users, fail over environments, or communicate with customers. Only a living, tested, business-aligned continuity plan can do that.
In this expanded guide, we’ll show you how to build a continuity plan that delivers real-world resilience—not theory. You’ll learn how to define RTO/RPO requirements that reflect your operational realities, understand the relationships between infrastructure and business processes, and create a repeatable testing cadence that proves your strategy works. Most importantly, you’ll learn how to make continuity a cultural capability—not a dusty document.
Why an Integrated Backup & Disaster Recovery Strategy Reduces Downtime & Risk
Today’s digital environments are intricately layered and vastly more dynamic than the traditional server rooms of decades past. Most organizations now operate within a hybrid architecture that combines on-premises infrastructure, a range of cloud platforms, SaaS applications, mobile endpoints, virtualized servers, and an expanding array of third-party integrations. This evolution renders the legacy mindset of “nightly server room backups” obsolete—modern technology ecosystems demand a fundamentally different approach.
Resilience, in today’s environment, requires unifying backup, disaster recovery, cloud failover, network continuity, and incident response into a single, orchestrated strategy. Treating these elements as isolated functions, managed by disparate teams, inevitably leads to fragmentation. Such fragmentation creates vulnerabilities—unaddressed gaps that can turn routine outages into operational crises, disrupting business processes and jeopardizing critical data. Only by integrating these disciplines can organizations assure rapid, coordinated recovery and maintain uninterrupted business operations amidst evolving threats.
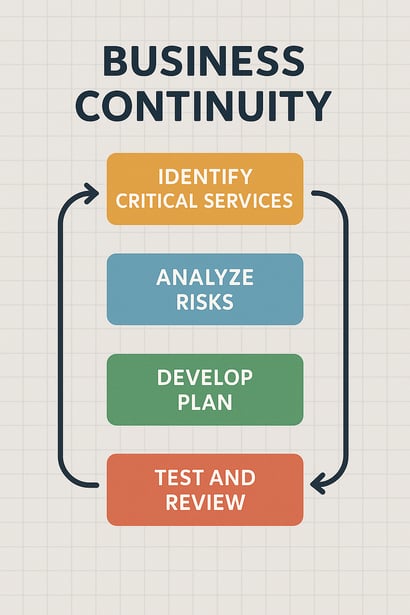
The Evolution of Continuity: From Backups to Business Readiness
For decades, backups were the safety net. If something broke, you restored a file, a disk, or a server. That worked when systems were smaller, downtime was tolerated, and threats were limited to hardware failures or human error.
Today, continuity expectations are dramatically different:
- Ransomware can encrypt every system in minutes, requiring complete environment recovery—not just file restoration.
- Cloud platforms shift responsibility—providers secure infrastructure, but customers must protect their own data and configurations.
- Remote workforces depend entirely on system uptime to communicate, collaborate, and deliver services.
- Online service expectations have tightened—customers expect availability anytime, anywhere, without disruption.
The modern business continuity model is no longer about restoring data. It’s about restoring operations. And the two aren’t always the same.
Why Backup Alone Isn’t Enough
Backups are essential, but they do not guarantee rapid or full business restoration. Having a copy of your data is not the same as being able to resume normal operations seamlessly after a disruption.
Here are the key limitations of relying solely on backups:
- Backups lack Recovery Time Objective (RTO) assurances. While your information may be intact, the actual process of restoring environments can take hours or even days—far longer than most organizations can afford.
- They often omit system state, application dependencies, and configuration data. This means you may successfully restore files, but critical systems could remain nonfunctional without the underlying environment or required integrations.
- Backups are not equipped to coordinate recovery across interconnected systems. Modern businesses depend on complex ecosystems of applications, servers, and cloud services—recovering a single element in isolation does not restore operational continuity.
- Traditional backups are not engineered for cyber resilience by default. Without proper immutability or segmentation, ransomware and other threats can easily compromise or encrypt backup data, undermining the very purpose of having backups.
True disaster recovery is about more than restoring files—it’s about bringing your entire business back online, quickly and in the correct sequence. Effective continuity depends on restoring the right systems, in the right order, at the right speed, to an agreed recovery point, ensuring every critical function is operational. This requires integrated disaster recovery solutions that go beyond basic backup, delivering orchestrated recovery for the complexity of today’s business environments.
The Cost of Downtime
Downtime’s true toll goes well beyond the direct cost per hour. In every sector, the operational and business consequences can be swift and severe.
When manufacturing organizations experience system outages, production lines halt—causing immediate revenue loss and costly delays across supply chains. Healthcare providers may be unable to access patient records or deliver timely care, exposing them to both regulatory actions and real risks to patient safety.
For financial institutions, any outage disrupts critical transactions, creates the potential for data integrity issues, and undermines customer trust. Meanwhile, professional services firms lose billable time with every minute systems are down, causing missed deadlines, dissatisfied clients, and potential reputational damage.
These are only the visible impacts. There are substantial hidden and downstream costs associated with downtime:
- Employees are left idle or forced to use manual workarounds, resulting in sharp drops in productivity and efficiency.
- IT teams are rapidly pulled off strategic projects to perform emergency repairs, often at overtime rates, driving up labor costs.
- Outages that affect customer-facing systems can irreparably harm reputation, erode client loyalty, and intensify scrutiny from partners and regulators.
- Missed contractual obligations and Service Level Agreement (SLA) violations can trigger financial penalties, lost revenue, or even termination of key business relationships.
- Regulatory fines or enforcement actions become a real risk if compliance data is impacted, inaccessible, or compromised during an incident.
For small and midsize businesses, a single significant downtime event can threaten the organization’s survival—jeopardizing cash flow, customer relationships, and stakeholder confidence. In the mid-market, the aftermath of major outages often means months spent restoring full operational capability, while the financial and reputational repercussions may be felt for years. In all cases, the message is clear: downtime is more than an IT inconvenience—it’s a critical business risk that demands deliberate, integrated continuity planning.
How to Build a Continuity Plan That Aligns to Real Business Impact
A continuity plan only delivers real value when it accurately reflects the organization’s critical operational priorities and the realities of day-to-day business functions. This goes well beyond adopting generic system-level targets or treating continuity as an IT checklist. Instead, it requires a granular evaluation of each core business process—determining precisely how much downtime can be tolerated and how much data loss can be accepted before causing meaningful disruption to your operations, revenue, compliance, or reputation.
Too often, continuity metrics like RTO (Recovery Time Objective) and RPO (Recovery Point Objective) are set exclusively at the server or application level, overlooking the interconnected nature of business workflows. The true risk is not to isolated IT components, but to the integrated processes that drive your business—processes supported by a tightly woven fabric of systems, applications, cloud services, and people.
To build a continuity strategy that protects what’s truly vital, organizations must take an inside-out approach—analyzing their environment through the lens of daily workflows, interdepartmental dependencies, and customer impact. Shift the continuity planning conversation away from system architecture alone, and refocus it on operational enablement: how technology, communication channels, and team capabilities come together to support your business outcomes.
By rooting continuity in operational realities, your recovery strategy becomes business-driven, not technology-driven. This ensures that, when a disruption occurs, response efforts are aimed at resurrecting the functions that keep your organization running—those essential activities that directly serve customers, maintain compliance, and drive value. The outcome is continuity that delivers measurable business resilience, protecting both your reputation and your bottom line.
Map Critical Processes & Dependencies
Every business has a set of “critical path” processes—those that must remain operational for revenue, safety, compliance, or customer experience. But many organizations have never formally documented these processes or the dependencies behind them. When an outage occurs, teams often scramble to determine which systems support which functions.
Dependency mapping shifts continuity planning from reactive to proactive. By understanding which systems support which processes, IT teams can prioritize recovery in an informed and strategic way.
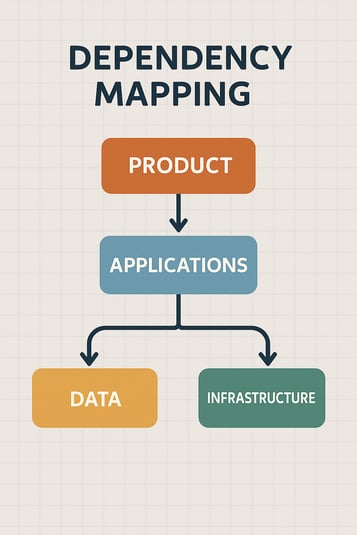
To fully map dependencies, consider:
- Primary applications (ERP, CRM, line-of-business systems)
- Secondary applications (analytics, reporting, billing)
- File systems and structured data repositories
- Authentication systems (Active Directory, MFA)
- Network dependencies (VPN, SD-WAN, ISPs)
- Cloud services (Azure AD, Microsoft 365, AWS services)
- People and teams who rely on the systems to perform revenue-generating tasks
The more precise your dependency map, the more predictable your recovery sequence becomes.
Define Business-Backed RTO/RPO Targets
RTO (Recovery Time Objective) and RPO (Recovery Point Objective) are the performance benchmarks of continuity—but only if they are defined by the business, not guessed by IT or assumed by leadership.
For each critical process, ask business owners:
- How long can this workflow be unavailable?
- How much data loss is tolerable?
- What are the operational consequences of downtime?
- What are the financial consequences?
- What are the regulatory or compliance risks?
From these answers, IT can reverse-engineer the technical requirements for a recovery solution. In practice, this might mean enabling:
- Real-time replication for mission-critical workloads
- Hourly backups for important systems
- Daily backups for archival or non-critical data
- Geo-redundant repositories for high-availability workloads
Business-backed RTO/RPO targets eliminate guesswork and ensure continuity budgets align with real business expectations.
Standardize Backup, DR, & Testing Cadence
Continuity success depends not only on your technology but also on your discipline. Testing is the difference between hope-based continuity and evidence-based continuity. Without testing, even the most advanced continuity architecture is simply theoretical.
A mature testing cadence includes:
- Automated nightly backup status validation with exception reporting.
- Monthly restore tests for individual systems.
- Quarterly failover tests for critical workloads.
- Semi-annual full environment recovery simulations for high-impact industries.
- Annual scenario-based tabletop exercises to validate communication and coordination.
Every test reveals something—whether it’s a misconfiguration, an undocumented dependency, or an opportunity to optimize recovery time. These insights become the engine of continuous improvement.
Document Roles, Communications, & Escalation
A continuity plan is as much about people as it is about technology. During a real incident, teams need clarity, coordination, and confidence. Confusion creates delays, delays increase downtime, and downtime costs money.
To eliminate chaos, your continuity plan should define:
- Exactly who is responsible for initiating recovery steps
- Who should be notified immediately and through which channel
- How communication flows between teams during an outage
- Escalation paths if primary contacts are unavailable
- Customer-facing messaging templates for downtime or disruption
- Vendor contacts who may assist with recovery
With roles and communication predefined, recovery becomes a coordinated process—not a scramble.
Make Your Continuity Plan Something You Can Count On
A continuity plan only works if it is treated as a living capability. Processes evolve. Applications change. Infrastructure shifts. Staff roles adjust. Business priorities move. Untested plans fall out of alignment quickly, which is why organizations must treat continuity like a core operational discipline.
CISA, NIST, and most major continuity frameworks emphasize ongoing refinement. Your continuity plan should be updated anytime:
- You adopt a major new system
- You migrate workloads to the cloud
- Your network architecture changes
- You experience a cybersecurity incident
- You add a new business unit or function
- You fail a recovery test—or even if a test exposes friction
Resilience is not a document. It is a cycle of planning, testing, learning, and improving. And it requires expertise, visibility, and consistency across both business and IT teams.
Certainly, this work can be done in-house. But for many organizations, having an experienced partner dramatically accelerates readiness. Cyber Advisors specializes in continuity assessments, recovery architecture, RTO/RPO validation, and ongoing testing programs for SMBs and mid-market organizations. Whether you're building continuity for the first time or maturing a legacy strategy, our assessment gives you clarity and a prioritized roadmap for improvement.
Request a Business Continuity Readiness Assessment
If your organization is unsure how well it could recover from a serious outage or cyber incident, now is the time to validate your strategy. A Business Continuity Readiness Assessment helps you understand where you are today, where gaps exist, and what changes will deliver the most impact.
Talk with Cyber Advisors about building a continuity plan you can count on. Our team helps organizations:
- Map critical processes and technical dependencies.
- Define business-backed RTO/RPO targets.
- Design and implement integrated backup and disaster recovery architectures.
- Establish repeatable testing cadences and improvement cycles.
The result is a business continuity plan that isn’t just documented—but proven in practice.