How to Protect Your Network from Zombies with ZTNA
Halloween may be over this year, but Zombies are everywhere. They are in movies, TV shows, video games, and even in your network. Yes, you heard me right. Your network is infested with zombies. Not the flesh-eating kind, but the cyber kind. These are devices or users that have been compromised by hackers and are now part of a botnet, a network of zombies that can be controlled remotely to launch attacks on other targets.
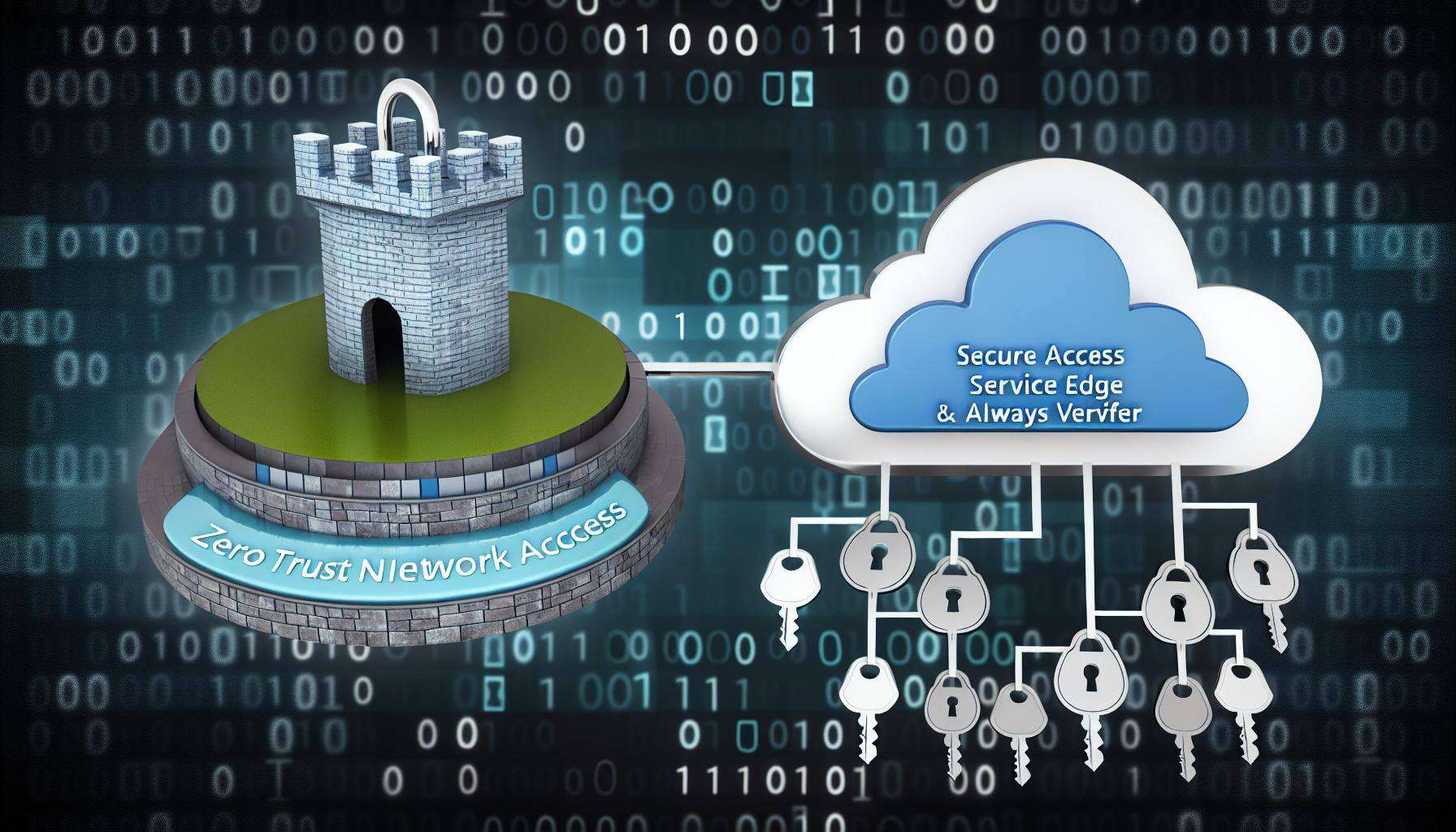
You may think that your network is safe because you have a VPN, a virtual private network that creates a secure tunnel between your remote users and your corporate resources. But VPNs are not enough to stop the zombies. VPNs grant access to the entire network, not just the applications that users need. This means that once a zombie gets in, it can roam freely and infect other devices or applications. VPNs also expose your network to the public internet, making it easier for hackers to find and exploit vulnerabilities.
So how do you protect your network from zombies?
So how do you protect your network from zombies? The answer is ZTNA, zero trust network access. ZTNA is a security framework that provides secure remote access to applications and services based on defined access control policies. Unlike VPNs, ZTNA solutions default to deny, providing only the access to services the user has been explicitly granted.
ZTNA powered by Fortinet is a category leader in providing secure and simple access to applications, regardless of where they are located, for users working from anywhere. Fortinet Universal ZTNA leverages the concept of a dark cloud, preventing users from seeing any applications and services that they don’t have permission to access. This introduces protection against lateral attacker movement, where a compromised endpoint or credentials would otherwise permit scanning and pivoting to other services.
Fortinet ZTNA also offers continuous checks on users as they connect to their apps, instead of the “once verified you are in” approach that VPNs take. Thus, Fortinet ZTNA provides a “never trust, always verify” least-privilege approach, constantly vetting user, device, and app behavior throughout a user’s session.
Some of the benefits of deploying Fortinet ZTNA to protect your network from zombies are:
- Flexible deployment: Enables ZTNA policies to be enforced for both remote workers and on-site workers.
- Granular access control: Grants access to a specific application only for that session.
- Ongoing verification: Verifies the user identity, the device identity and posture, before granting access to an application.
- Unified FortiClient agent: Provides VPN, ZTNA, vulnerability scanning, URL filtering and endpoint protection with a single agent.
- Automatic encrypted tunnels: Establishes TLS encryption automatically between endpoint and access proxy, hiding traffic.
So don’t let your network become a zombie apocalypse. Switch to Fortinet ZTNA today and enjoy the peace of mind that comes with knowing that your network is secure, and your users are productive. Contact us today to learn more about Fortinet ZTNA. You won’t regret it.
I hope you enjoyed reading my blog. If you have any questions or feedback, please let me know. 😊
We hope this blog post has been informative and helpful. At Cyber Advisors, we pride ourselves on being experts in IT Security and Managed Services. Our team of professionals has the certifications, capabilities, and experience to provide you with the best possible security posture. We understand that your business is unique, and we will work with you to develop a customized solution that meets your specific needs. With our help, you can rest assured that your company is protected and that your IT infrastructure is in good hands.
Reach out for more info!