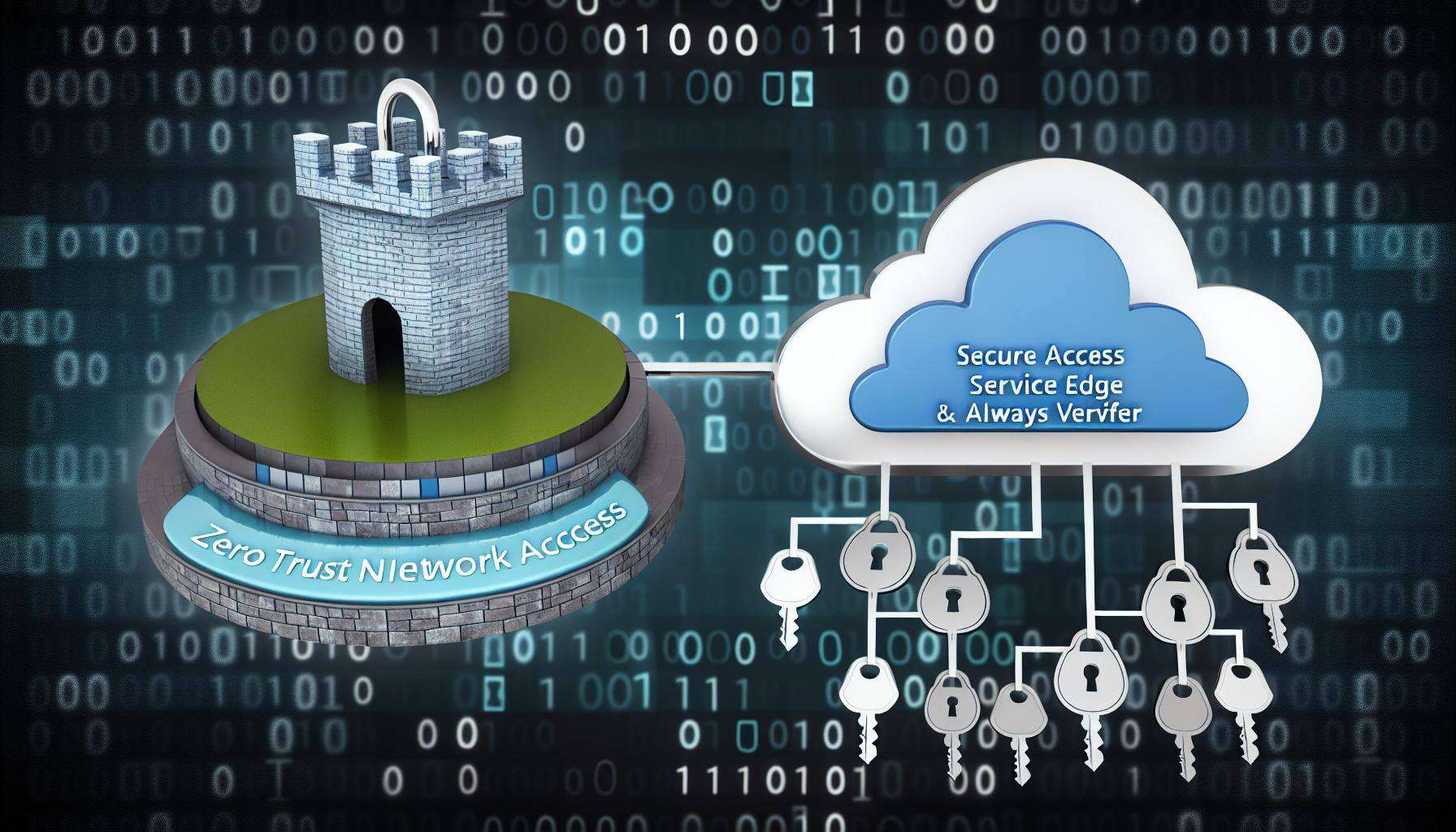
Businesses are increasingly relying on robust cybersecurity frameworks to protect their sensitive data and maintain seamless operations. Two of the most critical components in this endeavor are Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA). These technologies not only enhance security but also improve network performance, making them indispensable for modern businesses.
Understanding SASE and ZTNA
SASE is a cybersecurity model that converges wide-area networking (WAN) and network security services into a single cloud-based service. This approach simplifies network management and enhances security by providing a unified solution that integrates various security functions such as secure web gateways (SWG), firewall as a service (FWaaS), and cloud access security brokers (CASB). Or in simpler terms, SASE is a cybersecurity approach that combines wide-area networking (WAN) and network security into one cloud-based service. It simplifies managing networks and boosts security by bringing together different security tools like secure web gateways, firewalls, and cloud access security.
ZTNA or Zero Trust, is a security framework that enforces strict access controls based on the principle of "never trust, always verify." Unlike traditional VPNs that provide blanket access to a network, ZTNA ensures that users and devices are continuously authenticated and authorized, allowing access only to specific applications and resources. In simpler terms, ZTNA is about making sure anyone who accesses your data is verified/authenticated/authorized each time they access.
-
Why SASE and ZTNA are Essential for Security
Why SASE and ZTNA Are Essential
Enhanced Security Posture
The primary benefit of implementing SASE and ZTNA lies in the substantial enhancement of a business's security posture. In today's dynamic cyber landscape, where threats are constantly evolving, traditional perimeter-based security measures fall short in providing adequate protection. SASE and ZTNA revolutionize security by offering a comprehensive framework that safeguards against a myriad of threats through meticulous verification and monitoring of every access request. This proactive approach ensures that only authorized users and devices gain entry, minimizing the risk of breaches and data compromise. With SASE and ZTNA in place, businesses can fortify their defenses and stay ahead of cyber adversaries, bolstering their resilience in the face of ever-changing security challenges.
Improved Network Performance
SASE not only bolsters security but also improves network performance by optimizing the delivery of applications and services. By converging networking and security into a single service, SASE reduces latency and ensures that resources are accessed quickly and efficiently. This is particularly beneficial for businesses with distributed workforces, as it provides a seamless and consistent user experience regardless of location.
Scalability and Flexibility
As businesses grow and evolve, their security needs change. SASE and ZTNA offer the scalability and flexibility required to adapt to these changes. Whether a business is expanding its workforce, incorporating new technologies, or extending its reach into new markets, SASE and ZTNA can easily scale to meet new demands. This adaptability ensures that security measures remain robust and effective, no matter how the business evolves.
Simplified Management
Managing multiple security solutions can be complex and time-consuming. SASE simplifies this by integrating various security functions into a single, unified platform. This not only streamlines management but also reduces the risk of configuration errors and security gaps. ZTNA further simplifies security management by providing a clear and straightforward approach to access control, reducing the administrative burden on IT teams.
Supporting Remote Work
The shift to remote work has made traditional network security models obsolete. SASE and ZTNA are designed with remote work in mind, providing secure access to applications and data from any location. This is crucial for maintaining productivity and ensuring that remote workers can operate securely without compromising the business's security posture.
Implementing SASE and ZTNA with Cyber Advisors
At Cyber Advisors, we understand the importance of robust cybersecurity solutions for modern businesses. Our team of experts can help you implement SASE and ZTNA frameworks tailored to your specific needs, ensuring that your business is protected against the latest threats while enjoying improved network performance and simplified management.
By partnering with Cyber Advisors, you can rest assured that your business is equipped with cutting-edge security technologies that provide comprehensive protection and support your growth and success.
SASE and ZTNA are critical components of a modern cybersecurity strategy. Their ability to enhance security, improve network performance, and support scalability makes them essential for businesses of all sizes. By integrating these technologies into your cybersecurity framework, you can ensure that your business is well-protected against evolving threats and is positioned for continued growth and success.
For more information on how SASE and ZTNA can benefit your business, contact Cyber Advisors today. Our team is here to help you navigate the complexities of modern cybersecurity and implement solutions that keep your business safe and secure.
Would you like to learn more about ZTNA or SASE?
If you'd like to learn more about SASE or ZTNA, we have experts on hand to talk about how we can offer small enhancements to dramatically increase your cyber security posture.
Shoot us a message and we'll get back to you ASAP!
Recent Blog
It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
Why is Cyber Maturity Important to Manufacturers?
Because it keeps lines running smoothly and margins intact. Cyber maturity reduces outage time,…
Why SMBs Are Moving Away From Break/Fix IT Support
Break/fix creates hidden costs and chaos; proactive managed IT prevents issues and stabilizes the…
The 5 Easiest Ways to Start Using AI in Your Business
If you’ve been curious about artificial intelligence (AI) but feel overwhelmed by the technical…