Hybrid cloud pairs the control and proximity of on-prem infrastructure with the elasticity and services of public cloud, so you can run each workload in the environment where it performs, protects, and pays off best. Done correctly, it becomes a single operating model—not a tug-of-war between data centers and the cloud—where identity, security, and governance span both.
In this deep dive, you’ll see how to balance agility, security, and cost for real-world workloads, design an architecture that aligns to your applications, data, and compliance requirements, and build a practical placement framework your operations, security, and finance teams can all support. You’ll also learn how to move from plan to production with confidence—establishing clear guardrails, implementing unified monitoring and backup patterns, and rolling out a 90-day roadmap that reduces risk while unlocking quick wins.
balancing on-prem & cloud workloads maximizes agility & security
Most growing companies face a tension: some workloads are tightly coupled to the office or plant floor, require deterministic latency, or are bound by data residency and compliance controls. Think about OT systems on the manufacturing line, electronic health records in a clinic, or financial systems that must keep data within a specific jurisdiction—these often can’t tolerate jitter, long round-trips to the cloud, or ambiguous sovereignty. They need reliable, predictable performance and clear audit trails close to where the work actually happens.
Other workloads benefit from the elasticity and services of the public cloud. Analytics, AI/ML, digital customer experiences, and bursty front-end applications often run better when they can scale out on demand, tap into specialized managed services, and reach users globally without you owning all the infrastructure. In many organizations, this mix of requirements grows more complex over time as new applications are added, acquisitions are integrated, and legacy systems are modernized in stages.
Hybrid cloud resolves the tension by joining on-premises control with cloud scalability—not as two separate strategies, but as a cohesive operating model. Identity, policy, and security serve as the connective tissue between environments, so you can decide, per workload, where it should run based on performance, risk, and cost, then manage everything through a unified set of guardrails. The result is a single control plane for your business: critical, place-sensitive systems stay close to your operations, while elastic, innovation-focused workloads take full advantage of the public cloud.
Business drivers
- Place-sensitive data remains on-prem to satisfy regulatory, sovereignty, or contractual obligations while still integrating with cloud analytics or AI services.
- Burst capacity in the cloud handles seasonal spikes, product launches, or M&A migrations without over-buying hardware.
- Latency and user experience improve when edge and branch services stay close to where work happens, while global services leverage cloud POPs.
- Governance and cost control remain transparent via policy-based placement and showback/chargeback.
Technical realities
- Not every app is cloud-ready today; refactoring takes time. Hybrid accommodates lift-and-optimize alongside cloud-native.
- Data gravity is real; datasets can be petabyte-scale. Moving them frequently is expensive and risky.
- Identity, networking, and security need to be consistent across environments to reduce operational risk.
Bottom line: hybrid cloud is not a compromise—it’s a control plane decision. You choose the best execution venue for each workload based on policy, performance, and risk, then manage everything as one fabric.
Designing a hybrid architecture that aligns to apps, data, & governance
Start with outcomes, not platforms. Growing businesses care about revenue, margins, risk, and customer experience—not which logo is on the portal. Your cloud strategy should map technology choices directly to those outcomes, so every decision about where a workload runs can be tied back to measurable business impact: faster time-to-market, fewer incidents, tighter SLAs, and more predictable costs.
That means defining success criteria up front with your operations, security, and finance leaders, then working backwards to the architecture. Instead of asking “Should this be on-prem or in the cloud?” ask “What does this workload need to deliver for the business, and which execution venue best supports that objective within our risk and compliance tolerances?”
Use the following three lenses to guide design and keep that outcome-first mindset front and center, from initial planning through ongoing optimization.
1) Business lens
- Objectives: speed to market, resiliency targets (RPO/RTO), customer SLAs, compliance scope (HIPAA, CJIS, PCI, SOX, GDPR), and geography.
- Constraints: licensing, vendor lock-in risk, skills, data residency, contractual obligations, and physical sites.
- KPIs: feature lead time, change fail rate, cost per transaction, uptime, mean time to recovery, and security event rate.
2) Workload lens
Classify each app by modernization level, data gravity, latency, integration coupling, and regulatory sensitivity. This drives placement and migration sequencing.
3) Platform lens
Choose a small number of standard building blocks—e.g., Azure + Azure Stack HCI, or AWS + Outposts, or GCP + Anthos—and design for identity parity, network reachability, observability, and policy-as-code across all sites.
“Put each workload in its ideal place, then make everywhere feel the same to administrators and auditors.”
A practical workload placement framework
Use this simple scoring model to determine the best execution venue per workload. Score each factor 1–5 (1 = low importance; 5 = high). Sum the columns. If On-Prem Total > Cloud Total, keep it local or at the edge; if the reverse, go cloud-first; if they’re close, consider hybrid active/active or cloud burst.
| Factor | On-Prem Weight | Cloud Weight | Guidance |
|---|---|---|---|
| Data residency/sovereignty | 5 | 1 | Keep primary copy local; replicate to cloud analytics in anonymized or masked form. |
| Latency sensitivity | 4 | 2 | Manufacturing/OT, trading, or real-time CX often require edge/branch execution. |
| Elasticity/burstiness | 1 | 5 | Seasonal or campaign-driven workloads benefit from scale-out in the public cloud. |
| Modernization level | 2 | 4 | Cloud-native microservices favor managed PaaS; monoliths may remain on-prem until refactor. |
| Integration coupling | 3 | 3 | Heavy dependencies on plant/office systems may argue for local compute, with cloud-connected APIs. |
| Compliance scope | 4 | 3 | Both can comply; the question is where evidence collection and guardrails are strongest today. |
| Total (per workload) | Σ On-Prem | Σ Cloud | Choose placement, then document the rationale for auditors and renewal reviews. |
Tip: Use this worksheet during an Architecture Review with stakeholders from security, networking, app teams, and finance. Document assumptions and revisit quarterly.
Reference architecture: identity, network, data, management, & security
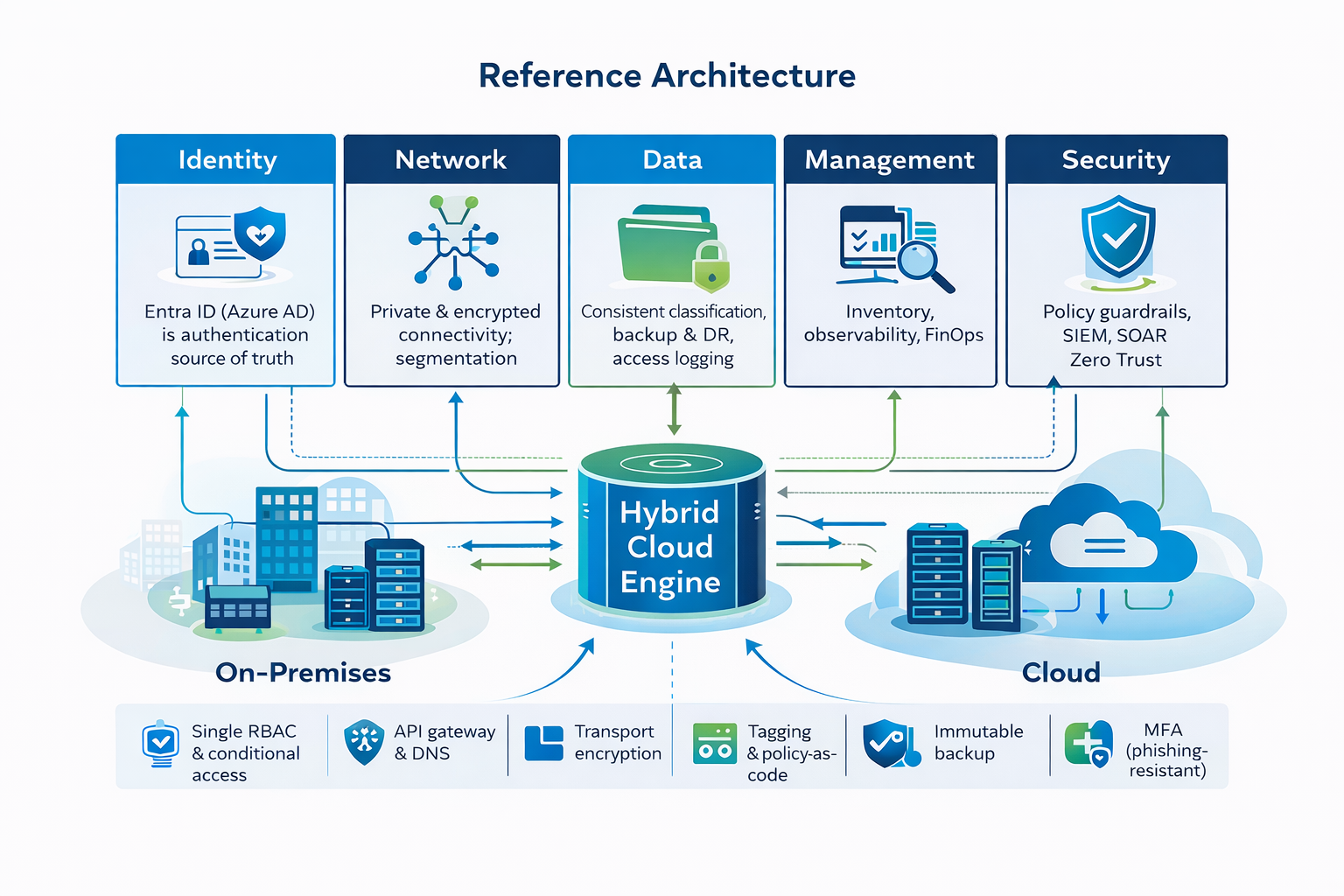
Regardless of vendor stack, successful hybrid architectures share five pillars.
1) Identity as the control plane
- Adopt a single identity provider (e.g., Entra ID/Azure AD) as the authentication source of truth for both cloud and on-prem.
- Use conditional access and phishing-resistant MFA for admins and service accounts.
- Standardize role-based access control (RBAC) across clusters, subscriptions, and resource groups.
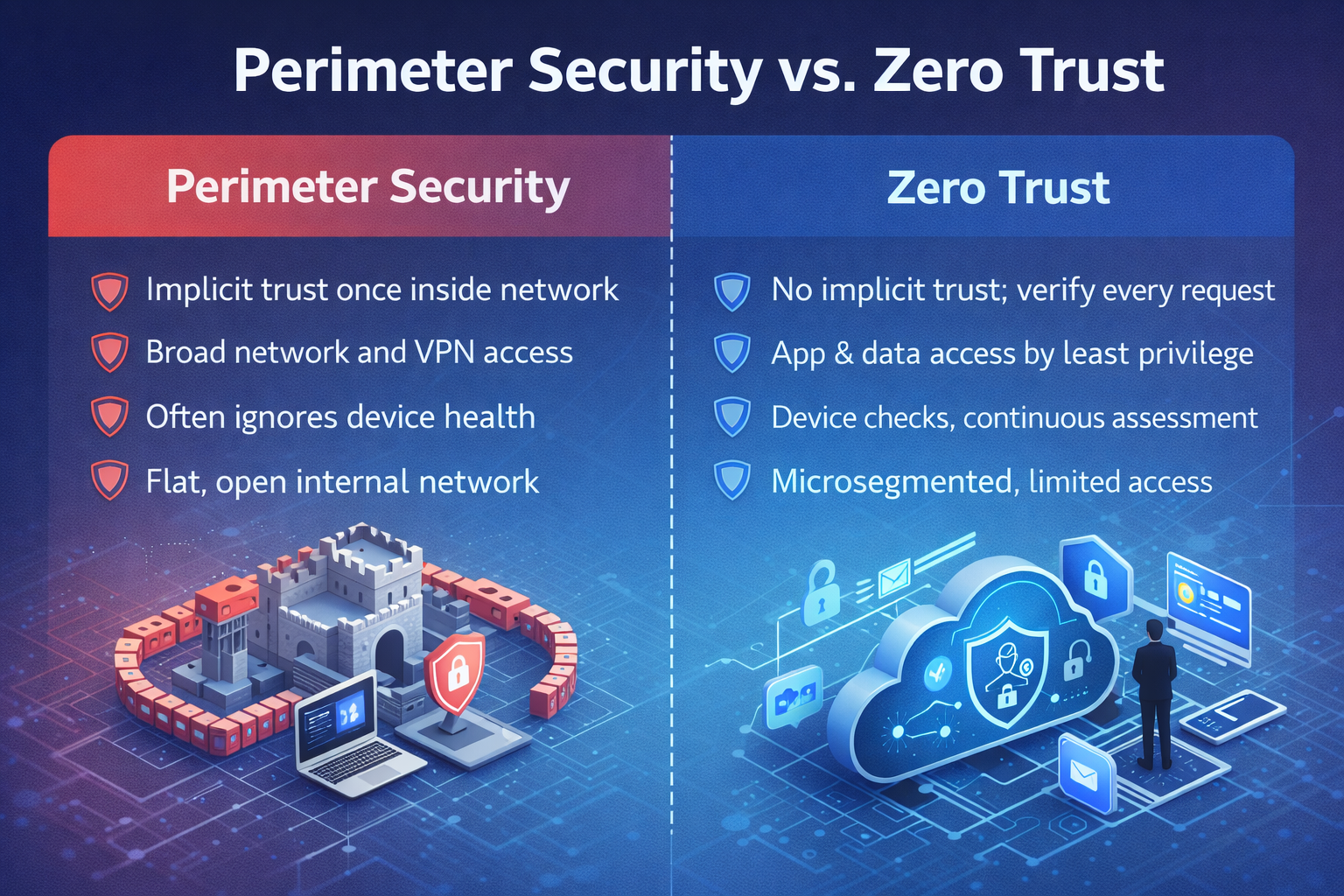
2) Network that assumes Zero Trust
- Prefer private connectivity (ExpressRoute/Direct Connect) for steady data flows; use encrypted internet overlays for burst and branch.
- Segment by application tier and sensitivity; enforce least-privilege with micro-segmentation and policy-based routing.
- Centralize egress, DNS, and certificate management for consistency and incident response.
3) Data fabric: protect, govern, & classify
- Apply consistent classification and retention. Sensitive data stays on-prem by default, replicates with masking or tokenization when needed.
- Use immutable backups and object lock; practice recoveries monthly.
- Log data movement and access centrally for audit; tie to DLP and insider-risk controls.
4) Management & observability
- Unified inventory with tags/labels identifying owner, environment, cost center, and sensitivity.
- Collect metrics, logs, and traces in one platform with alerting tied to SLOs.
- Automate patching and configuration drift detection across clouds and datacenters.
5) Security as code
- Guardrails via policy-as-code (e.g., Azure Policy, AWS SCPs) with auto-remediation.
- Centralized SIEM/SOAR with connectors for both on-prem and cloud telemetry.
- Regular tabletop exercises that include hybrid incident scenarios (ransomware, misconfigured storage, credential theft).
Governance, FinOps, & cost optimization in hybrid
Hybrid success isn’t just technical. Governance and financial operations (FinOps) ensure sustainability and trust by turning your hybrid model into an auditable, predictable operating system for the business. Clear policies define where workloads can run, how data is protected, and which teams own which decisions; disciplined FinOps practices translate usage into business metrics, prevent waste, and align spend with value. Together, they give executives confidence that hybrid growth won’t spiral into uncontrolled cost or unmanaged risk—and that every new workload, whether on-prem or in the cloud, is deployed within guardrails that your security, compliance, and finance teams can stand behind.
Policy guardrails
- Location policies: restrict resource regions and on-prem data zones; require approvals for exceptions.
- Security baselines: enforce encryption at rest/in transit, tagging, backup policies, and image hardening.
- Connectivity standards: define approved peering models, egress policies, and DNS; prohibit ad hoc tunnels.
FinOps disciplines
- Right-size by profile: steady workloads stay on reserved/committed capacity; spiky workloads use autoscale and spot where possible.
- Showback/chargeback: dashboards with business KPIs (cost per order, per inspection, per session)—not just VM hours.
- Decommission rigor: stop the “orphan tax” with lifecycle policies, TTL tags, and quarterly cleanups.
Key points: place-sensitive data on-prem and burst to the cloud; optimize costs by workload profile; improve latency and user experience; maintain governance and compliance.
monitoring, Disaster Recovery, & the 3-2-1-1-0 backup pattern
Operations unify your hybrid fabric day-to-day and during incidents.
Monitoring the full stack
- Collect metrics (CPU, memory, latency), logs (system, app, security), and traces (distributed) into one platform.
- Define SLOs/SLIs per service; alert on error-budget burn, not just on utilization peaks.
- Run weekly anomaly reviews to catch leakage, mis-tagging, and noisy alerts.
Resilience & disaster recovery
- Design RPO/RTO per app tier; tier-1 may require active/active across on-prem and cloud.
- Exercise failover regularly, including DNS, identity, and secrets rotation.
- Document runbooks in a shared, versioned repo with clear ownership.
The 3-2-1-1-0 pattern
Keep three copies of your data, on two different media, with one copy offsite, one copy immutable/air-gapped, and zero backup recovery errors in test. This pattern is achievable with a hybrid approach, using on-prem snapshots, cloud object storage with object lock, and a secondary location.
Common pitfalls to avoid
- Two operating models. Treating on-prem and cloud as separate kingdoms doubles the toil and risk. Unify identity, network, policy, and observability.
- “Lift-and-strand.” Moving a VM without reconsidering dependencies leads to latency and cost surprises. Re-map data flows before migrating.
- No exit plan. Document how you will move or refactor workloads in 12–24 months; keep contract terms flexible.
- Shadow IT. Provide secure, well-documented landing zones so teams don’t bypass guardrails.
- Under-funded ops. Budget for platform engineering, not just projects: pipelines, templates, golden images, and automation.
A 90-day hybrid cloud rollout roadmap
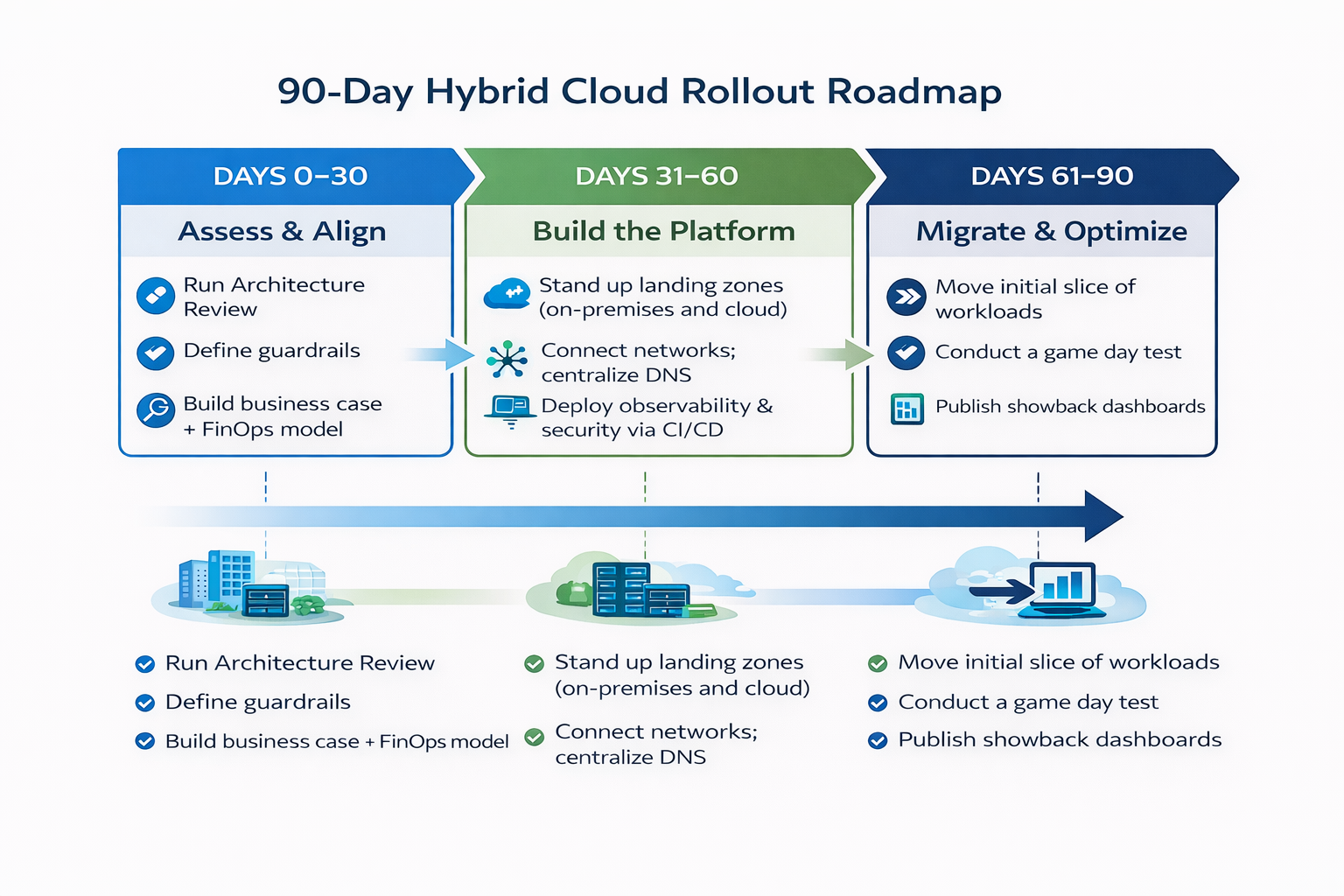
Use this phased plan to get value quickly while reducing risk.
Days 0–30: Assess & align
- Run an Architecture Review and create the **workload placement** register using the scoring framework above.
- Define guardrails: identity standards, network patterns, encryption policies, and tagging.
- Build a business case and FinOps model: capacity profile, reserved vs. burst, target KPIs.
Days 31–60: Build the platform
- Stand up landing zones (on-prem and cloud) with pipelines, RBAC, and policy-as-code.
- Connect networks with private or encrypted paths; centralize DNS and egress.
- Deploy observability, backup/DR, and security integrations into CI/CD.
Days 61–90: Migrate & optimize
- Move an initial slice of workloads (one steady, one spiky) to validate burst, right-sizing, and governance.
- Conduct a game day: simulate an outage and a security incident across both environments.
- Publish the first showback dashboard; adjust reservations and autoscale rules based on observed usage.
Mini case study: bursting for seasonal demand
A regional e-commerce brand experienced 6–8× traffic spikes during promotional events. Running year-round hardware for the peak was wasteful; running fully in public cloud was costly due to steady baseline and data gravity near a Midwest distribution center.
Hybrid solution: baseline order processing and inventory stayed on-prem with low-latency links to the warehouse systems. The web tier and recommendation service auto-scaled in the cloud during events. Data replicated asynchronously via private connectivity; analytics ran in cloud nightly.
- Infrastructure cost per order fell 28% year-over-year.
- Checkout latency improved by 23% at peak due to local caching and edge compute.
- Security events dropped thanks to centralized identity and WAF/CDN controls.
Results vary, but the pattern is repeatable: keep the steady, integration-heavy core close to your operations; burst what delights customers in the cloud.
Executive checklist
- Document workload placement with business rationale and revisit quarterly.
- Standardize on a single identity provider with phishing-resistant MFA.
- Enforce policy-as-code for regions, encryption, tagging, and backup.
- Implement unified logging/metrics/tracing and publish SLOs.
- Adopt 3-2-1-1-0 backups and test recovery monthly.
- Stand up FinOps dashboards with cost per business transaction.
- Run game days: failover, credential theft, misconfigured storage.
- Create an exit strategy and keep architecture modular.
Let Cyber Advisors Help!
Cyber Advisors brings hands-on experience in guiding organizations of every size—from fast-growing SMBs to multi-site mid-market enterprises—through the shift from a fully on-premises environment to a modern hybrid cloud. Our architects have delivered successful outcomes across manufacturing, healthcare, financial services, professional services, retail, and education, aligning each workload to its ideal execution venue with identity, networking, security, and FinOps guardrails baked in. Clients consistently report faster time-to-market, improved edge user experience, greater resilience with 3-2-1-1-0 backups, and measurable cost control through right-sizing and policy-driven governance. Whether you need a pilot to prove value or a full program that standardizes landing zones and operations, we’ll help you find the sweet spot between control and scalability—so your team can innovate with confidence.
Frequently Asked Questions
Is hybrid cloud more expensive than going all-in on public cloud?
It can be if you duplicate environments. When designed intentionally—steady workloads on reserved capacity, spiky components in cloud—the total cost often drops while performance and resilience improve. FinOps discipline is key.
What about security—does hybrid expand my attack surface?
Yes, you gain new edges, but you also gain better controls. A unified identity plane, Zero Trust networking, and policy-as-code reduce risk, and cloud services can strengthen detection and response for on-prem assets.
How do we avoid vendor lock-in?
Favor open runtimes (containers, Kubernetes), standard interfaces (OIDC/OAuth2, SAML, S3-compatible storage), and decoupled data layers. Keep portability in your contracts and architecture diagrams.
Which workloads should we move first?
Choose one steady workload that benefits from reserved capacity and one elastic workload that benefits from burst/autoscale. Use those two as learning pilots before scaling up migration.
Do we need dedicated network links?
Not always. Encrypted internet overlays are sufficient for many use cases. For heavy, predictable data flows or strict compliance, private links can be justified.
Request a Hybrid Cloud Architecture Review
Ready to find the sweet spot between control and scalability? Our architects will map your apps and data, build a right-sized hybrid design, and deliver a 90-day plan aligned to performance, security, and cost KPIs.
- Workload placement matrix and migration priorities
- Identity, network, and policy guardrails
- FinOps baseline with quick-win savings
- Resilience plan with 3-2-1-1-0 backup