Reaching cyber maturity in financial services requires the right mix of tools, services, and governance. Financial institutions operate in one of the most heavily targeted sectors for cybercrime—and one of the most regulated. Banks, credit unions, wealth management firms, insurance organizations, and fintech companies face constant pressure to prove resilience, ensure compliance, and defend sensitive customer data around the clock.
Unfortunately, most firms are still operating with fragmented security stacks, underfunded IT teams, or outdated assumptions about where cyber risk originates. True cyber maturity requires more than buying tools—it demands a strategic alignment of technology, governance, monitoring, response, and vendor stewardship. This article breaks down the essential components financial firms need to move from reactive security to a proactive, measurable, audit-ready state.
The Path to Cyber Maturity in Financial Services
Cyber maturity is not a single tool, a certification, or a milestone—it's the ongoing ability to identify, manage, and mitigate threats effectively. For financial organizations, it means:
- Continuous visibility into assets, risks, and threats
- Rapid detection and response to malicious activity
- Strong governance and compliance alignment
- Documented controls and repeatable processes
- Protected customer data and reduced operational risk
To achieve this, institutions need an ecosystem of interlocking tools and services—not individual point solutions. Below, we break down the essential categories that define cyber-mature financial operations.
Essential Tools Financial Firms Need for Cyber Maturity
While the financial sector has historically invested more in cybersecurity than most industries, the pace and complexity of threats have outstripped traditional tools. Cyber maturity requires a modernized technology stack that delivers visibility, intelligence, automation, and scalability.

1. Security Information & Event Management (SIEM)
SIEM platforms remain the backbone of financial security monitoring. A robust SIEM centralizes logs from across your environment and identifies suspicious patterns in real time. For banks and financial institutions—where every network event, login, or transaction could signal fraud—SIEM is indispensable.
Financial firms need SIEM for:
- Centralized log management across on-prem, cloud, and hybrid systems
- Threat detection using correlation rules, behavioral analytics, and threat intelligence
- Audit readiness with long-term log retention and searchable event trails
- Regulatory requirements such as GLBA, SOX, FFIEC, and PCI DSS
However, SIEM alone does not guarantee cyber maturity—it requires tuning, 24/7 monitoring, and skilled analysts. That's where MDR and SOC services become essential.
2. Managed Detection & Response (MDR/XDR)
Modern threats don’t operate within business hours—and internal teams rarely have the bandwidth or expertise to provide continuous monitoring. MDR and XDR deliver the always-on protection financial institutions need.
Key benefits for the financial sector:
- 24/7 SOC-as-a-Service without the cost of building an in-house team
- Proactive threat hunting using machine learning and behavioral analytics
- Rapid incident response to contain threats before they escalate
- Endpoint, server, and cloud coverage in a unified platform
XDR extends these capabilities across email, network, cloud workloads, and identity—helping financial firms respond to threats holistically rather than in silos.
3. Cloud Security & Zero Trust Controls
As banks and financial firms shift critical workloads to the cloud, cyber maturity requires strong cloud-native controls. Legacy security models cannot protect distributed teams, mobile banking platforms, or hybrid architectures.
Critical cloud security components include:
- CASB (Cloud Access Security Brokers): to monitor and control cloud app usage
- CSPM (Cloud Security Posture Management): to reduce misconfigurations
- Zero Trust identity controls with MFA, SSO, and privileged access management
- Email and collaboration security for Microsoft 365 and Google Workspace
- Micro-segmentation to limit lateral movement inside networks
Cloud adoption can accelerate innovation—when paired with the right guardrails.
4. Compliance Monitoring & Automation
Financial institutions operate under rigorous oversight from federal and state regulators and internal governance bodies. Whether navigating mandates such as GLBA, SOX, NYDFS 500, PCI DSS, or FFIEC CAT, or facing the scrutiny of in-house risk committees, firms face relentless expectations for demonstrable, real-time compliance at every layer of operations. Achieving true cyber maturity demands more than simply checking boxes—it requires a holistic, evidence-driven approach where compliance is woven into daily processes. Modern financial organizations are moving beyond manually updated spreadsheets and ad hoc reporting, adopting automated solutions that continuously track, document, and validate controls across their environments. This shift ensures not only ongoing regulatory alignment but also streamlines audits, accelerates issue remediation, and underpins operational trust with both clients and examiners.
Compliance automation tools provide:
- Continuous control monitoring instead of point-in-time audits
- Automated evidence collection for auditors and regulators
- Gap analysis with remediation guidance
- Cross-framework mapping to avoid redundant work
Compliance shouldn’t be a fire drill—mature firms build systems that prove alignment every day.
Critical Cybersecurity Services Financial Firms Need
Technology alone cannot create cyber maturity. Financial institutions must leverage specialized cybersecurity services—delivered by experienced professionals—to ensure security technologies are precisely configured, continuously monitored, effectively optimized, and thoroughly validated. Expert partners provide the in-depth oversight and operational rigor required to align security controls with regulatory standards, detect and respond to advanced threats, and proactively close gaps before they can be exploited. By augmenting internal teams with dedicated expertise, financial organizations transform standalone tools into an integrated, resilient security posture that can withstand today’s sophisticated attack environment and ever-evolving compliance expectations.
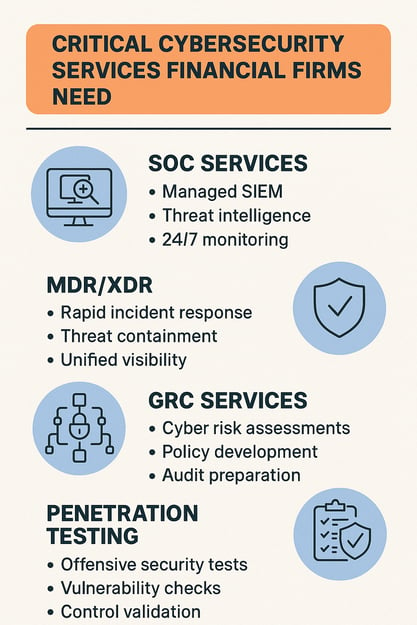
1. SOC Services & SIEM Management
A SIEM only delivers value when it’s tuned, monitored, and analyzed. Many financial firms either underutilize SIEM or are overwhelmed by alert fatigue.
Managed SIEM services deliver:
- Proper log ingestion & parsing
- Correlation rule development
- Root-cause investigation
- Threat intelligence integration
- Regulatory-aligned reporting
This ensures your SIEM becomes a strategic asset—not a noisy, underperforming tool.
2. Managed Detection & Response (MDR/XDR)
MDR/XDR services bring human expertise to the forefront, helping financial institutions detect and respond to threats that evade traditional controls.
Financial-specific MDR benefits:
- Real-time containment of compromised endpoints or accounts
- Fraud-related anomaly detection using behavioral analytics
- Integrated reporting for regulators and examiners
Most financial firms cannot build this capability internally—MDR becomes the operational foundation of cyber maturity.
3. Governance, Risk, & Compliance (GRC) Services
Cyber maturity is inseparable from governance. GRC services help financial institutions define security baselines, align controls with regulations, and ensure leadership understands risk exposure.
Core GRC services include:
- Risk assessments and control audits
- FFIEC CAT and NIST CSF alignment
- Policy development and review
- Regulatory reporting and examination preparation
Without governance, tools become disconnected, and decision-makers lack visibility into true risk levels.
4. Penetration Testing & Continuous Validation
Attackers evolve constantly—and financial institutions must ensure their defenses do too. Threat actors are innovating with new tactics and techniques, from sophisticated phishing campaigns and business email compromise to advanced ransomware and supply chain attacks that bypass traditional perimeter controls. In this climate, standing still is not an option. Financial organizations must continuously assess and adapt their security strategies, integrating the latest technologies, strengthening incident response protocols, and upskilling their teams to anticipate emerging threats. Ongoing investment in modernization—across tools, processes, and people—is essential for building resilience against the evolving methods adversaries use to target sensitive data, critical infrastructure, and customer trust.
Pen testing and validation services include:
- Network and application penetration testing
- Cloud security testing
- Red team engagements
- Phishing and social engineering campaigns
- Breach and attack simulation (BAS)
A mature cybersecurity program continuously tests controls, identifies blind spots, and verifies mitigation strategies.
Vendor Management: The Hidden Pillar of Cyber Maturity
Financial institutions depend on a complex network of third-party vendors to deliver essential services—ranging from core banking system providers and payment processors to cloud hosting platforms and software-as-a-service applications. Each vendor relationship extends a firm’s operational capabilities, but also introduces new channels of cyber risk into the organization. Recent industry incidents show that third-party vendor breaches can be among the most damaging and high-profile cyber events in the financial sector—resulting in regulatory scrutiny, economic losses, and reputational harm. This reality makes robust vendor oversight and proactive supply chain risk management a cornerstone of any comprehensive cybersecurity strategy for financial institutions.
A mature vendor management program includes:
- Formal risk tiering of all vendors
- Security questionnaire management
- Continuous monitoring of vendor cyber posture
- Periodic rights-to-audit, attestation reviews, and SOC 2 validation
- Contractual security obligations
No financial institution can reach cyber maturity without understanding its dependencies and enforcing strong security requirements across its vendor ecosystem.
Bringing It All Together: Building a Cyber-Mature Financial Institution
Cyber maturity results from integrated tools, continuous monitoring, structured governance, and expert guidance. The strongest financial security programs combine:
- Visibility through SIEM and cloud monitoring
- Protection through MDR/XDR and zero-trustCyber Advisors partners with financial institutions to build modern, compliant, and audit-ready cybersecurity programs tailored to the unique demands of the financial sector. Our team guides you through the selection, implementation, and ongoing management of advanced solutions, including SIEM and MDR/XDR, compliance automation, cloud security, vendor oversight, and governance frameworks. We align each component to empower your organization with persistent visibility, continuous protection, and actionable reporting. With a focus on regulatory compliance and operational resilience, we ensure your firm is prepared not just for today’s challenges, but for tomorrow’s evolving risks. controls
- Validation via pentesting and continuous assessment
- Governance through compliance automation and risk management
- Vendor oversight to reduce supply-chain exposure
The investment pays dividends: fewer incidents, reduced downtime, improved exam outcomes, and greater trust from customers and regulators alike.
Cyber Advisors Can Help Your Firm Achieve Cyber Maturity
Cyber Advisors partners with financial institutions to build modern, compliant, audit-ready cybersecurity programs. From SIEM and MDR/XDR to compliance automation and vendor oversight, we help you select, implement, and manage the tools and services required for long-term success.
Ready to strengthen your firm’s cybersecurity posture?