In this blog post, we’ll talk about our password cracking rig. Additionally, we will cover some simple changes that can be implemented into your Active Directory environment, that when paired with an employee awareness program, can help your employees choose more secure passwords.
Why Passwords Suck
It seems like often while performing internal assessments, we end up having discussions regarding passwords. The questions usually range from:
- Did you crack the passwords?
- Who set that weak password?
- Why did they choose that password?
- How can they even choose that password?
- What can we do to prevent this from happening again?
Because passwords are an issue for most companies, these questions appear universal – and with good reason. They are a point of oversight failure due to how most companies set their password policies/requirements and how users view them as a roadblock to getting their work done. The path of least resistance for employees is to pick easy-to-remember passwords that still meet the company requirements.
Password Cracking
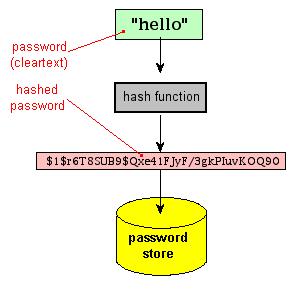
First off, we need to quickly talk about password hashes. In the diagram below, the cleartext password (“hello”) is hashed to get the value and then stored. There are different types of password hashing algorithms depending on the use case or application.
In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system (1). In this specific instance, we will be utilizing Hashcat to crack NT LAN Manager hashes (Windows passwords).
Hashcat Password Cracking
At a high level, Hashcat will take the dictionary list and hash every word within the file and do a comparison to the hash it is attempting to crack. If the two values match, you have successfully cracked the password!
Build A Password Cracking Rig
It’s not hard (just a little expensive) to use computing power to crack passwords. It’s what harmful attackers (who are targeting your company) do – they build a custom computer that is focused on malicious activities, such as cracking weak password hashes.
White Oak Security stays ahead of them by also having a (better) password cracking rig that we use in our penetration testing engagements. It’s a pretty standard set-up nowadays – the following parts list makes up the rig: (everything can be purchased here)
Password Cracking Tools:
- SAMSUNG 860 EVO Series – 1TB SSD – $147.99
- Phanteks Enthoo Pro Series computer case – $99.99
- ASUS X99-E motherboard – $459.99
- EVGA SuperNOVA 1600 power supply – $481.99
- G.SKILL TridentZ Series 32GB memory x 2 – $419.98
- New Cooler Master GeminII CPU fan/heatsink – $74.85
- Intel Core i7 CPU – $489.99
- Nvidia GEFORCE GTX 1080 Ti FE x 4 – $51.60
Below shows our little set up…


It cost roughly $7300 to put this system together. We opted to use Ubuntu 18.04 paired with the latest version of Hashcat (password cracking software). One thing to note, when setting up your password cracking rig is to use supported GPU drivers – this will make or break the GPU cracking speed drastically.
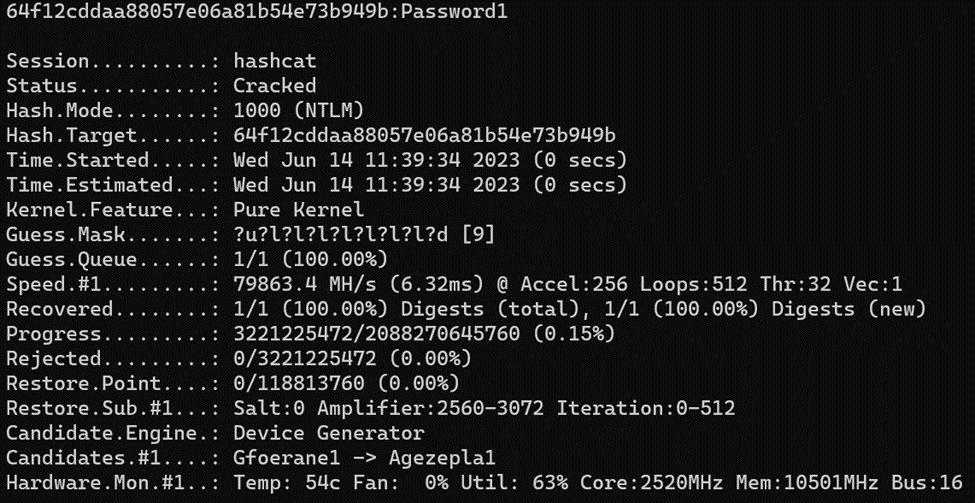
With Hashcat up and running, we can perform some benchmark testing to see how efficient the cracking rig is. Utilizing the “-b” flag we can get some quick benchmarking information from Hashcat. Our results are as follows:
Hashmode: 1000 - NTLMSpeed.Dev.#1.....: 61248.0 MH/s (59.71ms) @ Accel:128 Loops:1024 Thr:1024 Vec:2Speed.Dev.#2.....: 44127.7 MH/s (59.16ms) @ Accel:128 Loops:1024 Thr:1024 Vec:2Speed.Dev.#3.....: 44358.5 MH/s (58.88ms) @ Accel:128 Loops:1024 Thr:1024 Vec:2Speed.Dev.#4.....: 61368.9 MH/s (59.60ms) @ Accel:128 Loops:1024 Thr:1024 Vec:2Speed.Dev.#*.....: 211.1 GH/sThe benchmark most important to this post is the NTLM (Mode 1000) result. As we can see our total cracking speed is 211GH/s. That’s 211 billion guesses per second! This seems like a lot of guesses per second, but let’s put that into some real-world data.
Utilizing the following equation: ((95^(LENGTH))/211000000000)/60/60
This will calculate how long it would take to brute-force NTLM character set. If we replace the (LENGTH) variable with any number, we can calculate how long it would take to brute-force the entire character space utilizing the password cracking rig built from the parts list above.
The graph below represents character sets 1-9+.
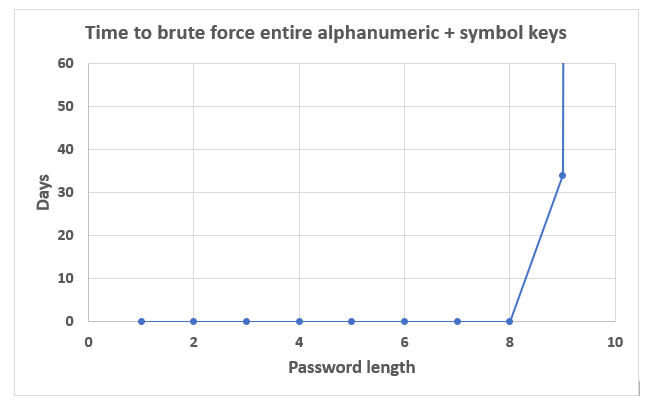
The graph demonstrates that the brute-force cracking time after 9 characters becomes exponentially greater.

Brute-force statistics can be deceiving. A common assumption is “setting a password to 10 characters will protect it from being cracked”. It does increase the time to potentially crack the password hash, but most hackers don’t take a pure brute-force approach. They know that people have a hard time remembering random words and number combinations. This results in people using common, easy-to-remember words coupled with just a few (and often meaningful) numbers.
Combining brute-force with resources like wordlists and rulesets will greatly reduce the amount of time needed to crack a large number of passwords.
Examples Of Password Cracking
Let’s look at the following example, the password “Winter2019”. It’s 10 characters, includes both upper case letters, lower-case letters, and some numbers. This password would meet Windows Active Directory password complexity requirements.
Now, let’s look to see if we can crack this password with Hashcat using a wordlist and a ruleset. One of the commonly used dictionary files is the “rockyou” wordlist (as per this breach). Making a quick search through the wordlist for the base word of “Winter” – here are the results:

The very first result is our exact base word entry! Now, we can pair this wordlist with a ruleset within Hashcat. A rule defines some kind of preprocessing that each word in a given wordlist will undergo before being hashed. Some common rules we can utilize are the Kore Logic rules, available here.
One of the specific rulesets that’s included is “KoreLogicRulesAppendYears”, which appends years to the end of every word in the wordlist. In the example, above we would crack the “Winter2019” password very quickly, even though the password is 10 characters.
Hacking Passwords, Easy
Now that we have established that cracking passwords is a relatively easy process, how do we get employees to set stronger passwords? We can easily search the internet and find articles, and articles, and articles on passwords …however, these articles come with numerous debates.
Common Password “Solutions”:
- Utilize password managers only
- Biometrics (fingerprint or retina (eye) scanners)
- Proper multifactor eliminates weak passwords
Using years’ experience performing internal and external penetration tests, I personally would defer to training the employees to select a “passphrase”. Let’s refer to an interesting comic, made by Randall Munroe a while back, about the differences between passwords and passphrases:

Password Security
It seems like the more employers stress to employees to set “secure” passwords, the more they end up with employees writing the passwords down or griping that the required password length is XYZ. This generally leads to passwords like “Winter2019” – where it fulfills the requirements set by management, but does little to protect the company.
In true raw brute-forcing form, it would take a very long time to crack a properly set passphrase that implements Windows complexity, even with the password cracking rig purchased in this post, it would be unrealistic to crack the password.
That means even highly rememberable passphrases are going to be significantly more secure than shorter ‘traditional’ passwords. It’s why we typically recommend that our clients suggest (or mandate) their users to utilize passphrases, rather than passwords.
Some recommendations for passphrases:
- Don’t use quotes/sayings (these can still be found in common dictionary lists)
- Add spaces between words
- Utilize common substitutes for the letters throughout the passphrase
- Example: $ for S
- Use completely random words
- Could be items found around the office/desk space, like lamps.
Password Human Error
To summarize this post, the human element is always going to be the weakest link in this situation. Human error or lack of training shouldn’t get the best of us, yet we see it happening again and again, every single minute, someone’s password gets hacked. The better we train our employees about password security, the better the chance organizations stand strong against attackers utilizing brute-force tools and imminent techniques.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...
Reference URLs: