GoAWSConsoleSpray – A Simple AWS Console Password Spraying Tool
As part of our Cloud Security Penetration Test service, White Oak Security has observed quite a few different AWS deployments over the years; ranging from extremely secure and locked down following the principles of least-privilege-access, to more open and inadequately permissioned AWS configurations. As part of those standard misconfigurations, we’ve noticed a frequent amount of IAM accounts deployed without any Multi-Factor Authentication (MFA) policy in place.
AWS Password Policy
These accounts lacking MFA, if deployed with a poor password, are susceptible to brute-force attacks as AWS does not enforce any account lockout policy by default [1]. According to Amazon’s documentation, “you can’t create a “lockout policy” to lock a user out of the account after a specified number of failed sign-in attempts. Amazon does perform some network throttling and bruteforce rate-limiting, however, these can easily be avoided with a bit of a time delay.
Additionally, we were unable to identify any tool that already exists that simply attempts to spray AWS account console credentials.
Password Spraying Tool
Today we’re releasing a simple AWS Console Password Spraying tool that provides a couple of benefits:
- Can spray AWS IAM accounts configured with console password authentication without locking accounts out (in a default deployment)
- Can identify valid usernames of accounts that have been deployed with MFA
Password Spraying Technique
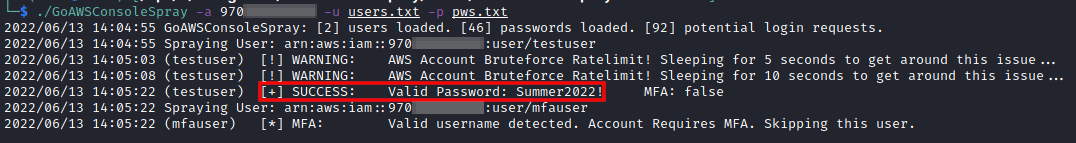
Simply provide an AWS Account ID, a list of usernames, and a list of passwords, and the tool will begin performing the password spray.
The likelihood of a successful password spraying attack depends on several attributes:
- IAM Accounts configured without Multi-Factor Authentication (MFA)
- Poor password policy
- By default, AWS will create a random password for an account that is typically strong. However, White Oak Security has observed both six (6) and eight (8) character password policies in use
- Poor user passwords
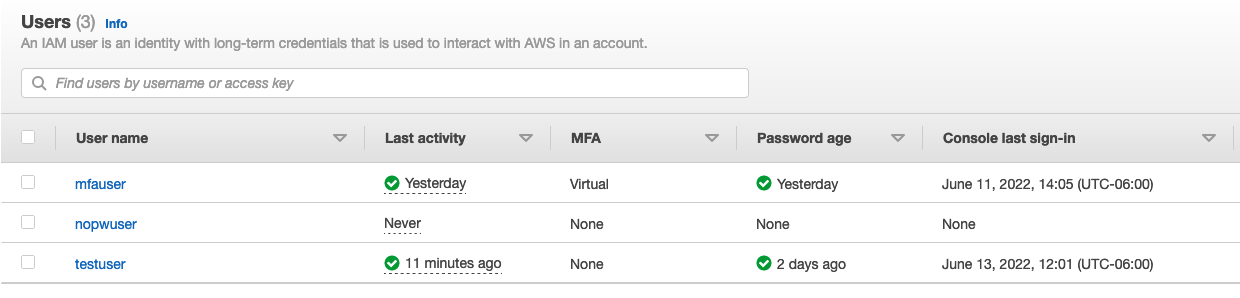
From an AWS Auditing perspective, if you have console access and you want to attempt to gain access to a list of users as part of your penetration test, you would be looking for IAM users that have a valid password age but are not configured with MFA.
Password Spraying Detection
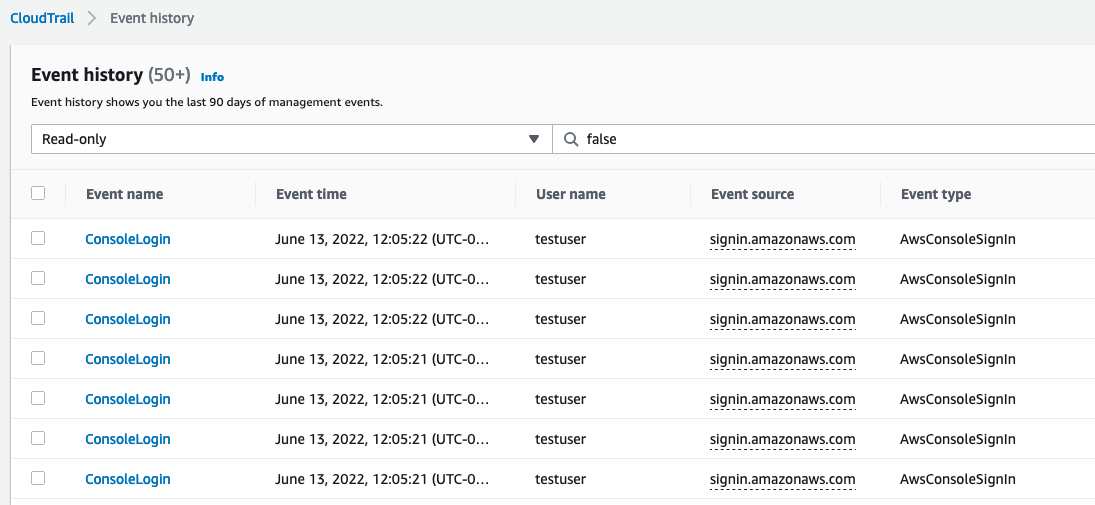
This tool is very loud and was not created to be stealthy. By default, AWS logs all console authentication attempts [2], both failures and successes, in CloudTrail. This includes the source IP, user-agent, time, and accounts targeted. Therefore, if you want this to be a bit more opsec safe, White Oak Security recommends modifying the user-agent as well as using some method to distribute your traffic across a variety of nodes (such as the AWS API Gateway [3]).
To counter some of the AWS network defenses, we have built-in a delay argument to throttle the amount of traffic, as well as some built-in error handling to increase the delay when AWS detects a brute-force attack. By waiting several seconds after this detection occurs, it appears to reset the timer and allows for an additional ~30 password spray requests before triggering the detection again.
GoAWSConsoleSpray Tool
GoAWSConsoleSpray can be found on our WhiteOakSecurity GitHub.
Sources
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_account-policy.html – Lack of IAM lockout policy
- https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-event-reference-aws-console-sign-in-events.html#cloudtrail-aws-console-sign-in-events-iam-user-failure – AWS CloudTrail events
- https://aws.amazon.com/api-gateway/ – AWS API Gateway
