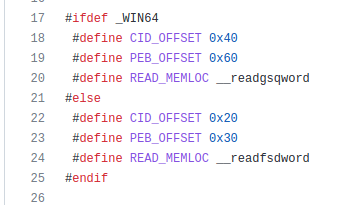
Today we’re going to talk a bit about CSV injection. First of all, what is CSV Injection? “CSV Injection, also known as Formula Injection, occurs when websites embed untrusted input inside CSV files” (OWASP). If an exported data field (or a cell in an opened CSV file) begins with certain characters that field is treated as a formula and may be executed automatically.
Characters in question:
- =
- +
- –
- @
An attacker may embed Dynamic Data Exchange (DDE) formulas within the CSV that will execute malicious code or exfiltrate data from the spreadsheet when a user opens the file through applications like Microsoft Excel or LibreOffice Calc.
Now you have a high-level understanding of CSV Injection, let’s see what companies and bug bounty programs have to say about this issue.
BugCrowd:
CSV Injection is classified as an “External Behavior” – Informational Finding
https://bugcrowd.com/vulnerability-rating-taxonomy
Google:
“This issue should be mitigated by the application which would be importing/interpreting data from an external source, as Microsoft Excel does (for example) by showing a warning. In other words, the proper fix should be applied when opening the CSV files, rather than when creating them.”
https://sites.google.com/site/bughunteruniversity/nonvuln/csv-excel-formula-injection
Synack:
“CSV Injection – Out of scope due to low impact”
https://synack.responsibledisclosure.com/hc/en-us/articles/115003611454-Scope-and-ROE
How widespread is this issue?
Is this issue easily discoverable in large companies? The following screenshots are of a large mobile payment retailer that allows for CSV Injection.
Once logged into the application, a user is able to view previous transactions. For this specific test I was able to change a customer’s name to a malicious DDE formula command “=cmd|’/c calc.exe’!A1”, that would open the calc.exe (calculator) program when the customer’s first name was opened within a spreadsheet. Below are the steps that I followed to perform this attack.
Selected the “Edit Customer” option:

Inserted payload into customer’s “First Name” field:

Saved customer modifications:

Exported the “Transactions CSV”:

Opened the DDE formula injected CSV file. Notice: Microsoft Excel did prompt the user about potential issues with the CSV file.

Calculator executed on the system! (This could have been PowerShell or another application that could be malicious):

What to do about it?
Determine “does your application produce or import CSV files?”. If so, the following guidelines can be implemented to prevent CSV Injection:
- Allow List Input Validation
- Restrict the following values: “+, -, =, and @”
- Encode File Output
- Prepend the cells with a specific character
- Adding a space or single tick to the beginning of the cell
- Remove any tab characters (0x09) in the cell
- Prepend the cells with a specific character