I was recently working with a customer on ADFS claims rules and thought to share the experience of how to make some simple customizations within ADFS to lockdown authentication to Office 365 services, in this case. The requirement was that if the authentication connection came from an External IP not listed (any of their many remote locations), then block the connection UNLESS you are part of a specific AD group.
For this to work, I had to create 3 rules. Go into Relaying Party Trusts, right click the Office 365 Party Trust and select Edit Claim Rules.
Select Send Claims Using a Custom Rule and click Next.
For the first one, we are going to map out the External IPs to be in the allowed list. To see how to format the IP addresses, go here - https://technet.microsoft.com/en-us/library/dn592182(v=ws.11).aspx. Click Finish.
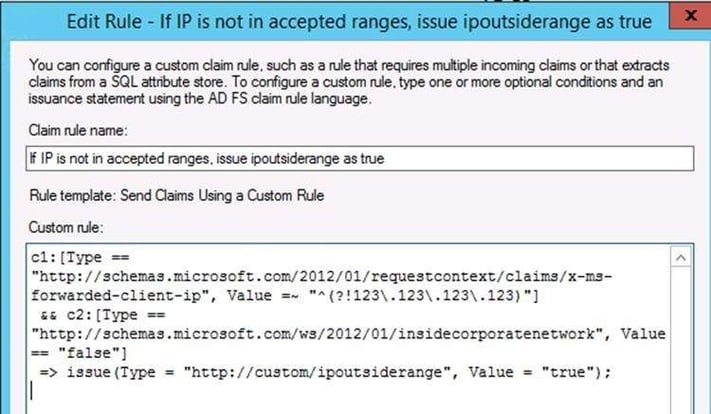
Here's the text to copy:
c1:[Type == "http://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-forwarded-client-ip", Value =~ "^(?!123\.123\.123\.123)"]
&& c2:[Type == "http://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork", Value == "false"]
=> issue(Type = "http://custom/ipoutsiderange", Value = "true");
The next two Claims Rules are Custom as well. This rule is to check the AD group for membership.
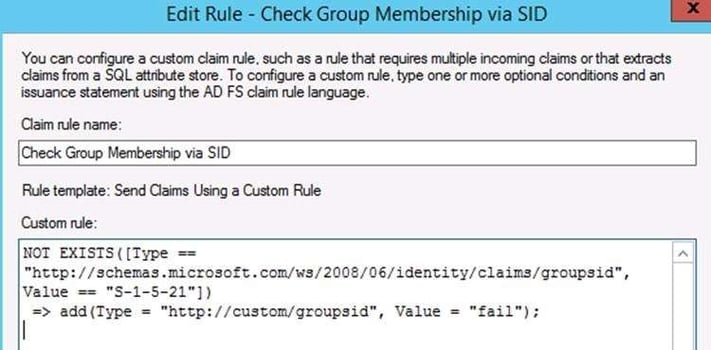
Here's the text to copy:
NOT EXISTS([Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value == "S-1-5-21"])
=> add(Type = "http://custom/groupsid", Value = "fail");
The final one is putting the two rules together to block based on External IP and the AD group membership.
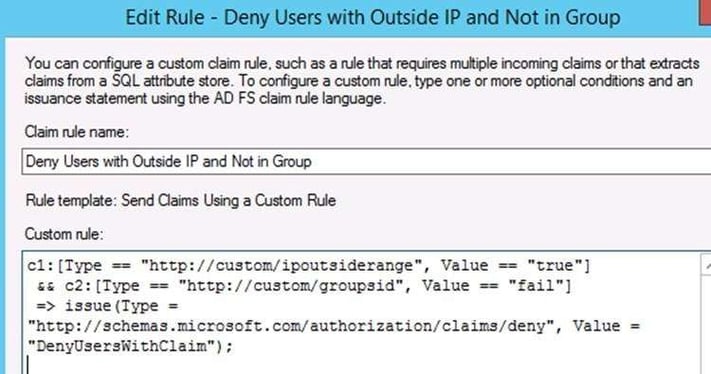
Here's the text to copy:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"]
&& c2:[Type == "http://custom/groupsid", Value == "fail"]
=> issue(Type = "http://schemas.microsoft.com/authorization/claims/deny", Value = "DenyUsersWithClaim");
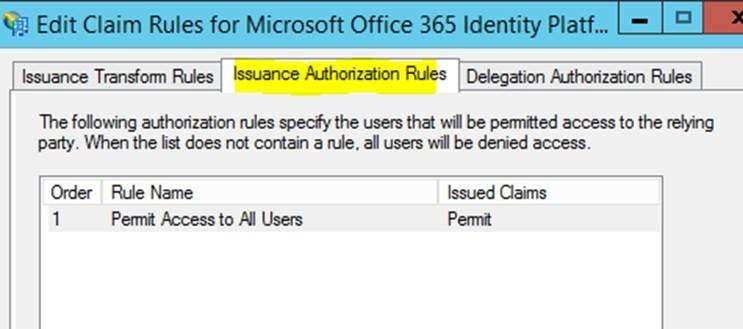
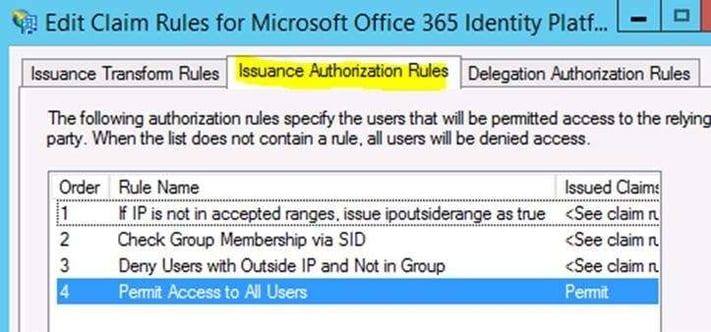
This is the final order of the claims rules.
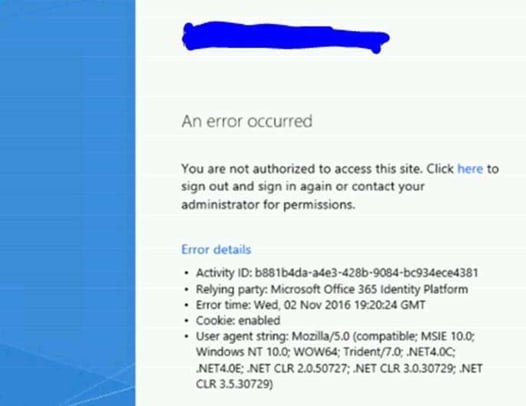
This is what the user gets if they go to it from another IP:
Here's the article that explains how to edit the Claims Rules in ADFS (Note: there is an error in the syntax of the one that I had to use, but it serves as a reference)
https://technet.microsoft.com/en-us/library/dn592182(v=ws.11).aspx
As you can see, this customization opens many doors to making your implementation flexible and custom to the needs for the business.