Simple Security Fails
Directory Listing Overview
While performing security tests against web applications or network infrastructures, I often come across web servers with directory listing enabled.
What is directory listing you say?
“Web servers can be configured to automatically list the contents of directories that do not have an index page present.” (https://portswigger.net/kb/issues/00600100_directory-listing).
Most of the time this issue comes up in reference to image directories which, from an attacker point of view, don’t usually provide much sensitive information. However, occasionally we find this configuration enabled on some very sensitive directories indeed.
Discovery
As an example, the following screenshot shows what a directory listing might look like:
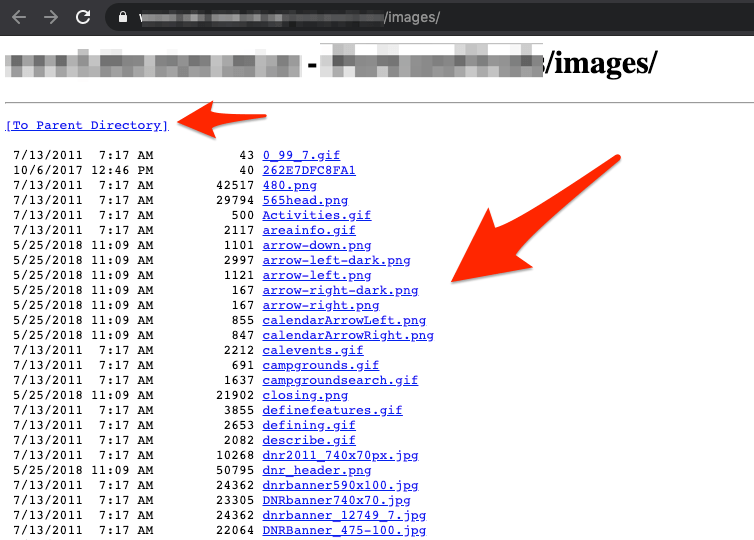
As we can see, the web server is listing out the contents of the directory on the screen. Now let’s see if we can turn this simple issue into something more severe. Using Google to search for directory listings is pretty easy.
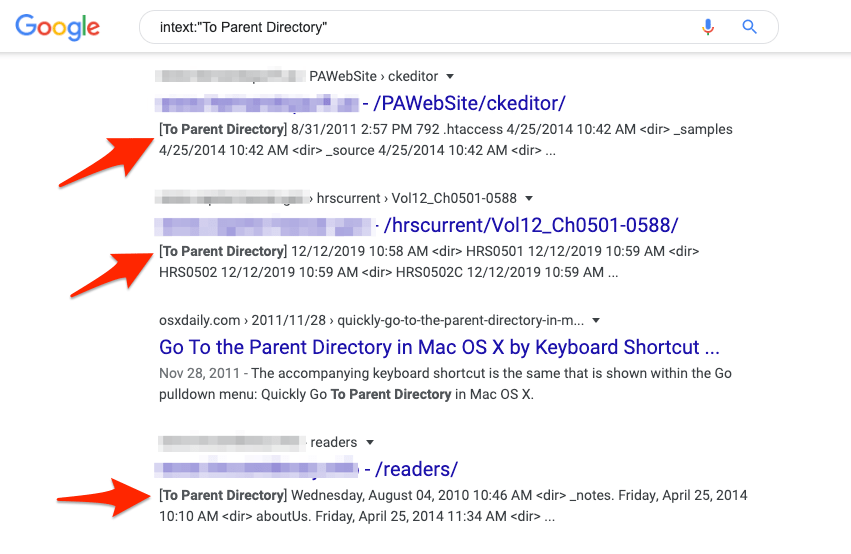
A basic search might look like:
Intext:”To Parent Directory”
Here are some example results of the search:
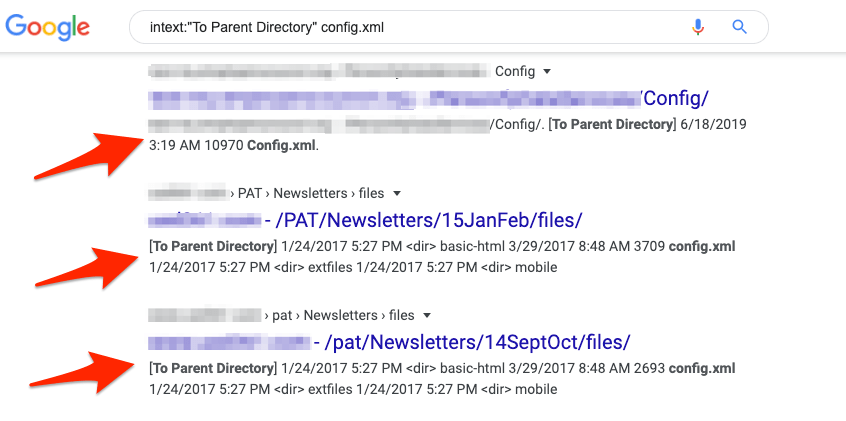
Now let’s turn it up a notch – adding “config.xml” to the search and running it again results in some potentially sensitive config.xml files. Here is a screenshot:
Viewing one of these config.xml files – we can see reveals cleartext credentials for the backend database. As shown in the screenshot below:

This technique can be used to discover specific files depending on the search made. A great reference for additional search options is the Google Hacking Database.
Remediation
The following steps can be performed to disable directory listing (browsing) on the web server:
Microsoft IIS
- Disable Directory Browsing from directory within the IIS manager console
Nginx
- Nginx (This is disabled by default)
Apache
- Create a .htaccess file within the application directory
- Add the following lines to the .htaccess file:
<Options -Indexes>
Implementing these changes to the web server can prevent a simple vulnerability from becoming a critical issue. Stay tuned for more Simple Security Fail blog posts.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...
