Comparing Automated HTTP Screenshot Tools
At last, the finale! For our last Screenshot Tool blog post, we will be putting the top 5 HTTP screenshot tools that are currently available for penetration testers or bug bounty hunters to the test! We compared the effectiveness of each tool (as well as their features, ease of use, and any issues we ran into) against a set of metrics to find the most useful tool.
Check out those previous posts first if you’d like, here’s all 5 previous parts: part 1 – EyeWitness, part 2 – WitnessMe, part 3 – Snapback, part 4 – Gowitness, part 5 – Aquatone.
So, Which Tool Is Best?
In order to compare the efficacy of screenshot tools discussed in the previous blog posts above, I needed to establish a baseline. To accomplish this, I gathered a list of 1000 domains for popular websites, sourcing from the fortune 500, as well as other lists I found on GitHub [1]. To ensure that all the sites were live, I used curl to request each website on the list to ensure that some sort of content was returned from the companies’ websites (indicating a live response) and swapped out any failed websites with other large companies. Repeating this process several times helped ensure that all baseline URLs were truly accessible from an internet perspective, and in theory, would allow for a valid screenshot.
The baseline validated list of 1000 domains spanned a variety of industries, mainly consisting of .com Top Level Domains (TLDs) of U.S. corporations. At the time of analysis (early 2022), all 1000 domains were accessible and served content without any issue in standard Firefox and Chromium browser sessions.
It is also important to note that within the 1000 domains, not every website handles the same. Some of these websites prompted modals via JavaScript (cookie acceptance dialogs), a couple of websites took more than sixty seconds to finish loading content from a slow CDN, a couple of websites are protected by CloudFlare which has decent automation prevention, and in one instance a website would actually crash Chromium headless under certain conditions. With all these various conditions, these websites end up acting as a pretty good test case for real-world external and internal reconnaissance, where it is crucial the screenshot tool is able to handle unexpected scenarios and push through error cases.
Historically, on multiple occasions during an external or internal assessment, I’ve had my screenshot tools pause or hang during execution which is extremely aggravating. One of my original reasons for even creating this blog post series was to make sure that we, at Cyber Advisors, are using the best screenshot tool available during our assessments. Something I also wanted to relay to my fellow pentesters.
Execution Scenarios
Using the baseline target list, each tool was given a fresh and unique AWS EC2 T3.Medium instance [2] to act as the exit node for the traffic without any potential home network ISP or WAF/CDN reputation limitations. Each tool had its network traffic proxied through a SOCKS5 SSH tunnel. The host Virtual Machine during this test was Linux 5.10.0-11-amd64 Debian 5.10.92-1, with 16gb of RAM, and 6 virtual processor cores.
Scenario #1 – AWS Socks Proxy – Ten (10) Threads: Out-Of-The-Box
The first scenario is simply the current build of the tool “out-of-the-box” from GitHub. This means using the tool without any sort of custom tweaks or adjustments (as indicated in each previous blog post series). I used a timeout of 20 seconds and, where possible, a navigation delay of 8 seconds to provide ample time for viewport navigation to complete and a successful screenshot to be captured.
Scenario #2 – AWS Socks Proxy – Ten (10) Threads: Best Configuration
The second scenario is the best possible configuration for each tool. Refer to each blog post in this series for additional details on how I determined the “best” configuration for each tool.
- Part 1 – EyeWitness
- Part 2 – WitnessMe
- Part 3 – Snapback
- Part 4 – Gowitness
- Part 5 – Aquatone
Potential Screenshot Tool Limitations
Occasionally, a host would not successfully render its screenshot due to automation/bot detection. I did not mark these as errors within each tool’s results below, as the hosts appeared to perform similarly. Bypassing Cloudflare’s bot detection is an additional capability for future experimentation [3].
Overall Screenshot Tool Performance Results
Now that we’ve established how I tested these tools, let’s jump right into the final results and my overall conclusions.
Chart Terminology
- Capture Attempts – The total number of attempted screenshot captures out of 1000 total potential URLs. This is how many images are saved on a disk.
- Blank/Errors – Analyzing the capture attempts, any screenshots which are corrupted, show a blank page, or otherwise indicate an error (excluding Proxy/CDN blocking AWS errors) are listed here.
- Missing – Capture attempts subtracted from 1000 reveals how many screenshots were skipped from capturing for some internal error/navigation delay timeout.
- Elapsed Time (seconds) – The total execution time for each tool in seconds
- Overall Accuracy – Formula: Capture attempts – Errors / 1000
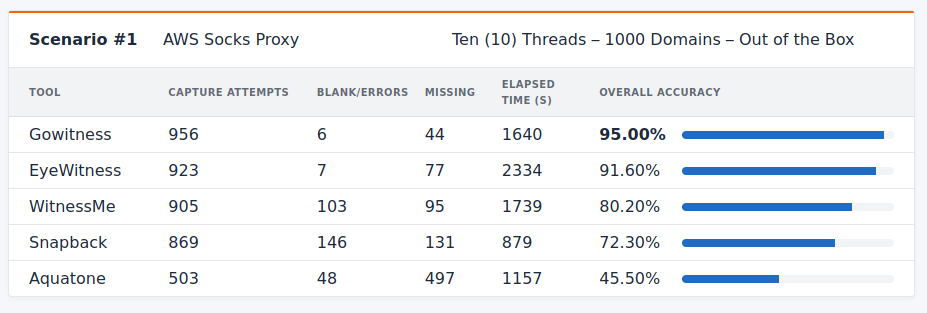
Scenario #1: Out-Of-The-Box
The “out-of-the-box” default configuration scenario: 10 threads, and where possible, a navigation timeout of 20 seconds and a navigation delay of 8 seconds.
With a high degree of accuracy, Gowitness was the clear winner of this round. Additionally, Gowitness finished its execution 30% faster than the second next most accurate tool, EyeWitness.
However, during this scenario, every tool failed to successfully terminate its processes once the last domain was processed. Additionally, EyeWitness and WitnessMe failed to clean up their Firefox/Chromium processes once the program was manually terminated. Lastly, EyeWitness failed to even properly generate a viewable HTML report.
One surprising thing I noticed, during this initial run, was how quick Snapback was. It completed its processing in half the time as Gowitness, however as I suspected in my initial analysis, the tradeoff was a lack of accuracy. Snapback contained the highest amount of blank or error screenshots since it has been deployed on GitHub with a very barebones configuration.
Scenario #2: Best Possible Configuration
As previously stated in each blog post, I could not come up with a way to significantly improve EyeWitness or Aquatone, so each result from Scenario #1 has been used for Scenario #2.
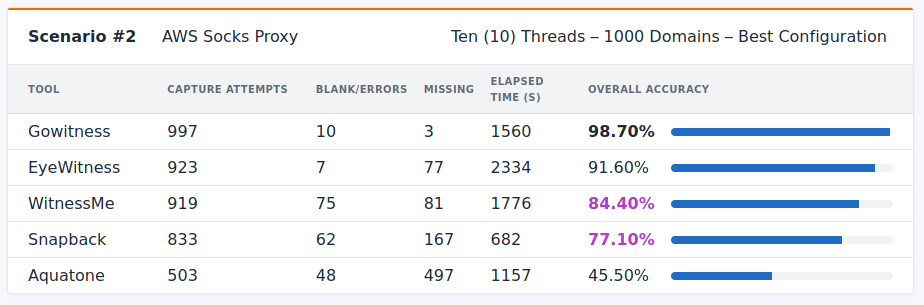
With these improvements, I was able to improve the overall accuracy of Gowitness up to a success rate of 98.7% against the list of 1000 screenshots. Additionally, the improvements to WitnessMe and Snapback helped improve their results as well. Snapback actually captured fewer screenshots than the previous execution, but was overall more accurate in scenario #2 compared to scenario #1 – as the number of errors was reduced. WitnessMe is still not at the level of accuracy as Gowitness or EyeWitness. Still, I hope that support for WitnessMe continues to grow as it shows promise as a potential python replacement for EyeWitness.
Comparing Screenshot Tool Features
An overall comparison for each of the tools is shown below. The features listed are based on my personal criteria requirements that I listed at the beginning of each of the previous blog posts. In my opinion, Gowitness provides the most features and scan capabilities compared to the other tools.
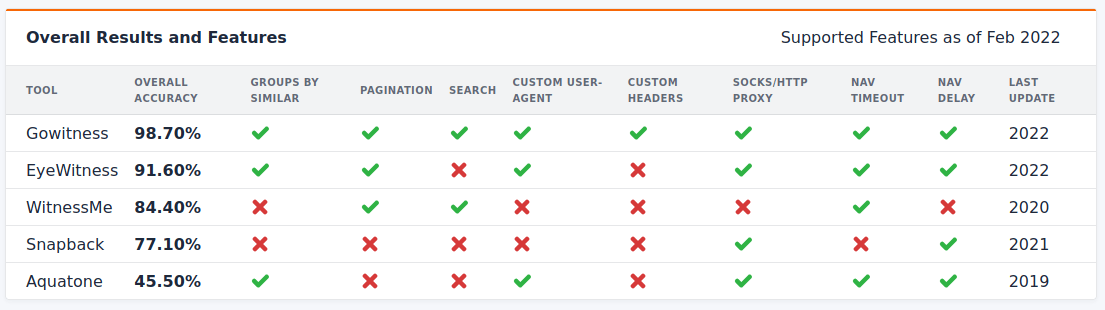
As far as user experience is concerned, both Gowitness and WitnessMe provided the easiest and most user-friendly experience for getting up and running quickly. WitnessMe provided the best CLI user experience of any of the tools, and I would highly recommend WitnessMe over EyeWitness if you had to pick a python-based tool. The only downside to WitnessMe is a lack of similarity grouping, which EyeWitness supports. While EyeWitness has a high degree of accuracy, the overall user experience is not enjoyable and for the life of me, I still cannot generate a report with thousands of assets without it breaking.
Which Screenshot Tool Is Best?
If you are looking for the best all-around tool, I would highly recommend you check out the Gowitness project as it works quickly, efficiently, and can probably be integrated into your recon pipeline with relative ease. Combined with its high degree of accuracy, Gowitness is the clear winner (in my opinion) and I would highly recommend this tool to anyone who performs screenshot captures as part of their reconnaissance, penetration testing, or bug bounty hunting process.
I had the most issues operating EyeWitness, Snapback, and Aquatone. I would not recommend these tools when better experiences exist with the Gowitness and WitnessMe tools.
Like I’ve noted, if you use any of these tools, please support and contribute to all of these Open-Source projects for each tool (linked below).
Authors Note: This blog series is my personal take on the state of screenshot tools. My network environment and physical setup may differ from yours when using these tools and you may notice your tool is more or less successful. I’ve done my best to be platform agnostic to provide the best environment for success. If you run into any errors, remember to check the individual project’s issues page for support.
Our Screenshot Tool Series
Again, in case you missed them, here are the previous posts to this Screenshot Tool series: part 1 – EyeWitness, part 2 – WitnessMe, part 3 – Snapback, part 4 – Gowitness, part 5 – Aquatone.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...
Sources
- Original Company List – https://raw.githubusercontent.com/9b/boxcar/master/app/data/clean-list.txt
- AWS Instance Types – https://aws.amazon.com/ec2/instance-types/
- Cloudflare Bypass Research – https://github.com/FlareSolverr/FlareSolverr