
LoRa Frequency
The Internet of Things (IoT) has revolutionized the way we live and work, connecting an ever-growing number of devices and systems to the internet. One key technology that has enabled this connectivity is LoRa (or Long Range) which uses sub-gigahertz frequency bands to transmit wireless data over long distances with low power consumption.
LoRa Frequencies
LoRa (Long Range) is a Low Power Wide Area Network (LPWAN) technology that operates in the sub-gigahertz frequency band. It typically uses frequencies in the range of 868 MHz in Europe, 915 MHz in the Americas and Asia, and 779 MHz in China. The exact frequency band depends on the country and region.
In LoRa, communication takes place through the use of spread-spectrum modulation, which enables data to be transmitted over long distances (up to 15 km in rural areas and 2-5 km in urban environments) with low power consumption. LoRa also supports bi-directional communication – allowing for both data transmission as well as reception, and it uses an adaptive data rate that adjusts the transmission speed based on the quality of the communication channel. The technology supports multiple device-to-device communication and can also be connected to the internet through a gateway, enabling access to cloud-based services.
LoRa Security
Despite the many benefits of LoRa, the security of IoT networks remains a critical concern. By connecting devices to the internet, LoRa networks open the door to a range of security threats, from hacking and data theft to malware attacks and network disruptions.
In this blog post, we will explore the security of the LoRa frequency, including common threats and the approaches and tools that ethical hackers (penetration testers) can use to test the security of these networks.

Threats to LoRa Frequency
The security of LoRa networks is threatened by a range of malicious actors, from hackers and cybercriminals to nation-states and rogue organizations. Some of the most common security threats to LoRa networks include:
Interception of communications
LoRa communications can be intercepted and monitored by unauthorized parties, potentially exposing sensitive data or intellectual property.
Manipulation of communications
LoRa communications can be manipulated by attackers to inject false data or disrupt the network.
Access to devices & systems
LoRa devices can be accessed by attackers to steal data, install malware, or launch further attacks.
Interference with the network
LoRa networks can be jammed or disrupted by attackers to cause widespread outages or denial of service.
Past security incidents and vulnerabilities have highlighted the need for robust security in LoRa networks. For example, in 2019, researchers discovered a vulnerability in LoRa devices that allowed attackers to execute malicious code and take control of the devices.
Pentesting LoRa Frequency
For ethical hackers, or pentesters, testing the security of LoRa networks is an important way to help organizations identify and mitigate potential threats. Here are the steps involved in planning and preparing for a LoRa pentest:
- Obtain Permission:
- Before beginning any testing, it is essential to obtain permission from the network owner or operator. This helps to ensure that the testing is conducted legally and ethically.
- Plan The Test:
- The next step is to plan the test, including the scope, goals, and methodology. This helps to ensure that the test is focused, efficient, and effective.
- Prepare The Tools:
- The final step is to prepare the tools and resources needed for the test, including wireless sniffers, protocol analyzers, penetration testing tools, and IoT-specific security tools.
Exploiting LoRa Frequency
For the purposes of this blog, we will focus on jamming techniques. The jammer will use a Software Defined Radio (SDR) module. These devices are programmable signal processing devices that allow modulation and demodulation of a signal according to our needs.
The jammer attack consists of two phases:
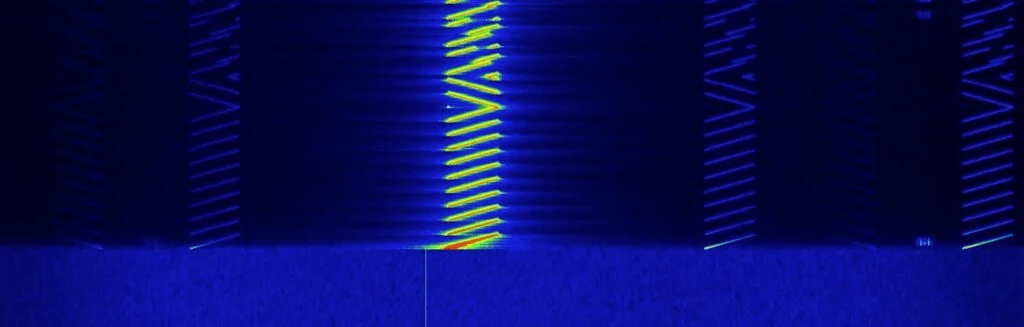
The LoRa signal can be detected using a series of band-pass filters that screened all the available channels in the LoRa range. This would allow us to monitor multiple channels, enabling the capture of any potential packet transmission.
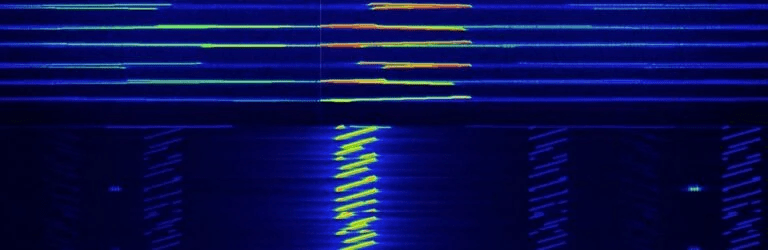
The LoRa signal can be disrupted by jamming, which involves transmitting a high-energy burst to the target frequency, causing the destruction of the LoRa signal. This leads the legitimate gateway to discard the packet, resulting in the loss of valuable information.
To apply our approach in the real world, we could use drones as an example. A drone can move across any terrain and gain adequate altitude to receive the signal. The RSSI can be quite accurate after a few measurements in the same location by averaging the values.
The approach here is to select a random location close to the facility, within a 5 to 10 km radius area. Within the receiving area of the LoRa signal, we can take multiple measurements to establish a good averaging RSSI value. We need to repeat the process in at least two arbitrarily selected locations if they are not at the same point. Using a trilateration algorithm, we can estimate the location of the sensor. The final stage is to approach the sensor and activate the selective jammer.
It’s important to note that these techniques should only be used by experienced pentesters and only with the proper permission and ethical considerations in mind.
LoRa Frequency Conclusion
The security of the LoRa frequency is of critical importance for the continued growth and success of the IoT. By conducting regular security assessments and penetration testing, organizations can identify and mitigate potential security threats – helping to ensure the privacy, confidentiality, and availability of their networks and data. Following ethical guidelines and using the right tools and techniques, pentesters play a vital role in keeping LoRa networks secure and reliable.
For pentesters, testing the security of LoRa networks provides an opportunity to help organizations protect their assets and systems, while also expanding their skills and knowledge in the field of IoT security.
If you’re curious about our penetration testing services, be sure to learn more about our IoT services here.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...

