Our Unique Security Testing Process
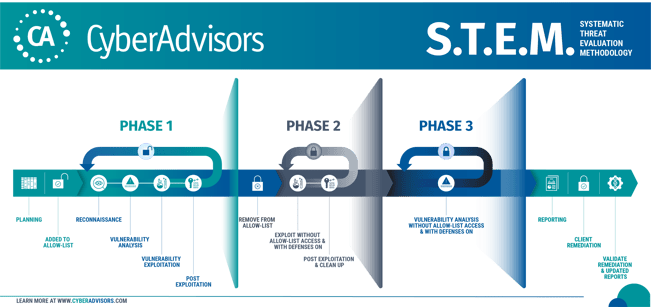
STEM Methodology
White Oak Security’s (now Cyber Advisors) unique, custom-crafted Systematic Threat Evaluation Methodology (S.T.E.M.) was built by our previous founder and CEO, Christopher Emerson. S.T.E.M. originated as an extension of strong industry-standard testing processes that, while effective, can be too narrowly focused and not incorporate other, contextually relevant factors in determining vulnerability priority.
We continue to use this pentesting methodology as Cyber Advisors because S.T.E.M. allows us to dig deeper and better understand how other security efforts, investments, and initiatives may impact the security of a particular application or network environment. This understanding allows our team to provide our clients with results that more effectively prioritize remediation efforts and more accurately reflect the actual security situation.
Security Testing Approaches
Why don’t other security professionals use this approach?
Penetration testing traditionally requires "allow" listing (or being added to an ALLOW LIST) for testing to be efficient and effective – giving the tester direct access and bypassing firewalls and other security-related investments in order to provide an accurate understanding of any security issues inherent to the testing target.
Clients sometimes feel that this “allow list” approach is unrealistic considering the investments that they’ve made in security tools and solutions that may protect the testing target. The argument we hear is often ‘this isn’t a realistic test.’
Both of these viewpoints are actually correct… Testers need to have direct access to a target in order to effectively test its security without spending far too long (i.e. being super expensive) bypassing ‘external’ security protections. However, those protections certainly do have an impact on overall security… Thus, the S.T.E.M. approach was built to address both of these concerns in the most efficient manner.
S.T.E.M. is not an approach that is always practical or applicable on every penetration test, but where it is, it provides the best of both worlds – an understanding of both the security vulnerabilities and issues with the testing target as well as the impact of a client’s broader security investments on those vulnerabilities.
The terrifying thing is how often those broader security investments have almost no impact on mitigating the vulnerabilities that our offensive security experts discover on the target itself, but that’s a post for a later time…
Systematic Threat Evaluation Methodology (STEM)
The Cyber Advisors offensive security team extends our penetration testing protocols beyond the traditional means to provide in-depth, practical, & actionable insights through our unique three-phased Systematic Threat Evaluation Methodology (STEM). The infographic below walks you through each phase.

MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.


