What Is Credential Dumping?
In a Windows environment, users authenticate to their machines (either locally or remotely) with their username and password. Behind the scenes, Windows hands off all authentication related tasks to the Local Security Authority Subsystem Service (LSASS) process. This process, known as “lsass.exe”, stores all sensitive authentication data in its memory, including user credentials and password hashes.
Knowing this, attackers target the data in the LSASS process to steal users’ sensitive Windows credentials from a previous logged session. Once credentials have been compromised, attackers can further their malicious lateral movement on the network. This process is known as credential dumping and is a key phase during an attacker’s kill chain to compromise accounts, passwords, and hashes.

There are plenty of tools and techniques for adversaries to use, such as Mimikatz, to dump credentials. To learn more about other credential dumping techniques, please take a look at this blog post. This post will aim to cover the built-in security mechanisms organizations can implement and how these mechanisms may halt an adversary’s compromise of the Windows environment.
Introducing LSA Protection!
Since the release of Windows 8.1 and Windows Server 2012 R2, Microsoft introduced “LSA Protection”, as a measure to protect the LSASS process against credential dumping attacks. LSA Protection marks the LSASS process as a special process, specifically a Protected Process Light (PPL), within the Windows Operating System. Being marked as a PPL process prevents access or tampering by non-administrative or non-protected processes.
With LSA Protection, the LSASS process can effectively deny 3rd party processes, such as Mimikatz.exe, from accessing and its memory and therefore, prevent credential dumping.
In other words, imagine LSA Protection as the bouncers to the poppin’ LSASS party of the year, and attackers are NOT on the invite list.

There are only a select few of Windows processes marked as a protected process. For example, Windows Defender (MsMpEng.exe) is also a PPL and only other protected processes (with the proper permissions and signatures) can read or tamper its data.
But enough theory, let’s see it to believe it!
How To Implement LSA Protection
LSA Protection is available on Windows 8.1, Windows Server 2012 R2 (and later releases) and implementing it is as straightforward as can be. In fact, Windows 11 has LSA Protection enabled by default!
Since this is a built-in Windows feature, it can be enabled either directly in the Registry Editor or as a domain level Group Policy.
Registry Editor:
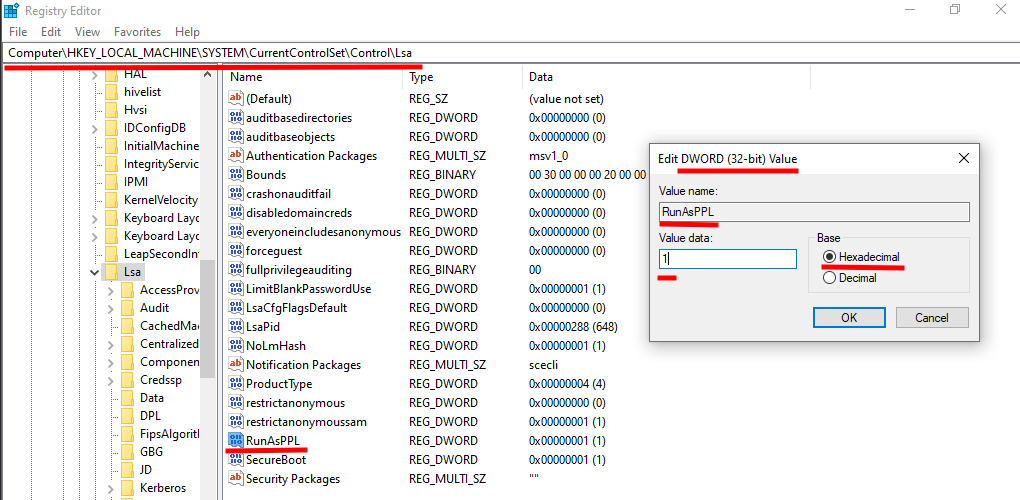
- Open the Registry Editor (RegEdit.exe), and navigate to the registry key that is located at “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa”
- Right click and create a new value of the registry key as a DWORD (32bit) Value
- Set the value name as “RunAsPPL” and set the value data as “1 (Hexadecimal)”
- Restart your computer.
Domain Level Group Policy:
- Open the Group Policy Management Console (GPMC).
- Create a new Group Policy Object (GPO) that is linked at the domain level or that is linked to the organizational unit that contains your computer accounts. Or you can select a GPO that is already deployed.
- Right-click the GPO, and then select Edit to open the Group Policy Management Editor.
- Expand Computer Configuration, expand Preferences, and then expand Windows Settings.
- Right-click Registry, point to New, and then select Registry Item.
- Set the following values:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Control\Lsa
- Value name: RunAsPPL
- Value type: REG_DWORD
- Value data: 00000001 (Hexadecimal)
- Select OK.
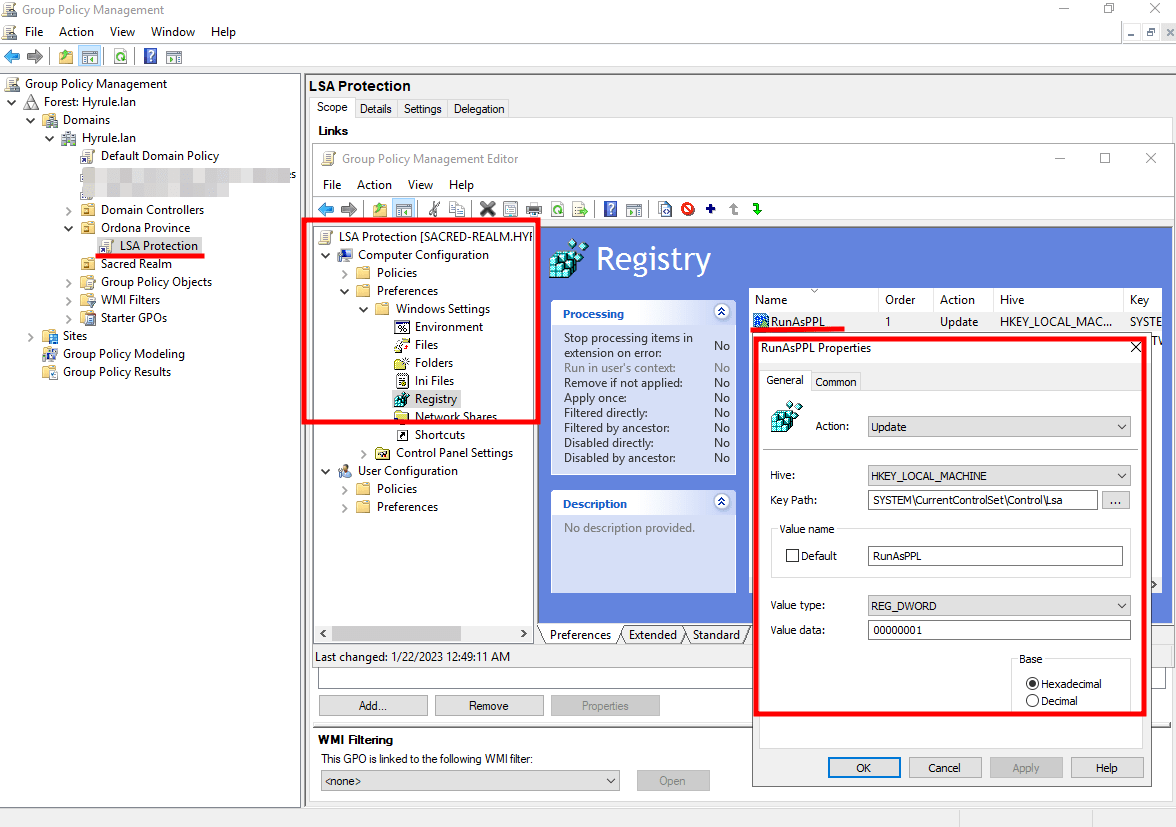
Note: Be sure to reboot the machine to ensure the policy is applied.
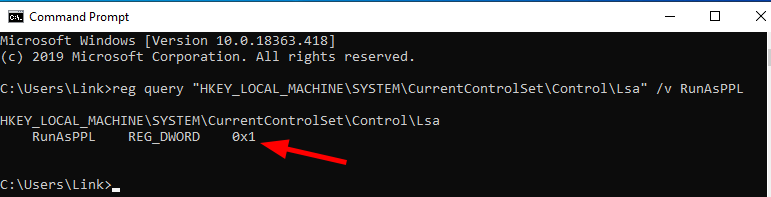
To check if LSA protection has been applied, run the following command within cmd.exe.
reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa" /v RunAsPPLThe `RunAsPPL` value should exist and be equal to `0x1`.
Finally, you can verify if LSA Protection is enabled within the Event Viewer.
- Open the Event Viewer (eventvwr.exe).
- Expand Windows Logs, then expand System.
- Sort by Event ID 12, Source Wininit

Protection In Action
The following is a demonstration of credential dumping with Mimikatz on a standard Windows 10 machine with and without LSA protection.
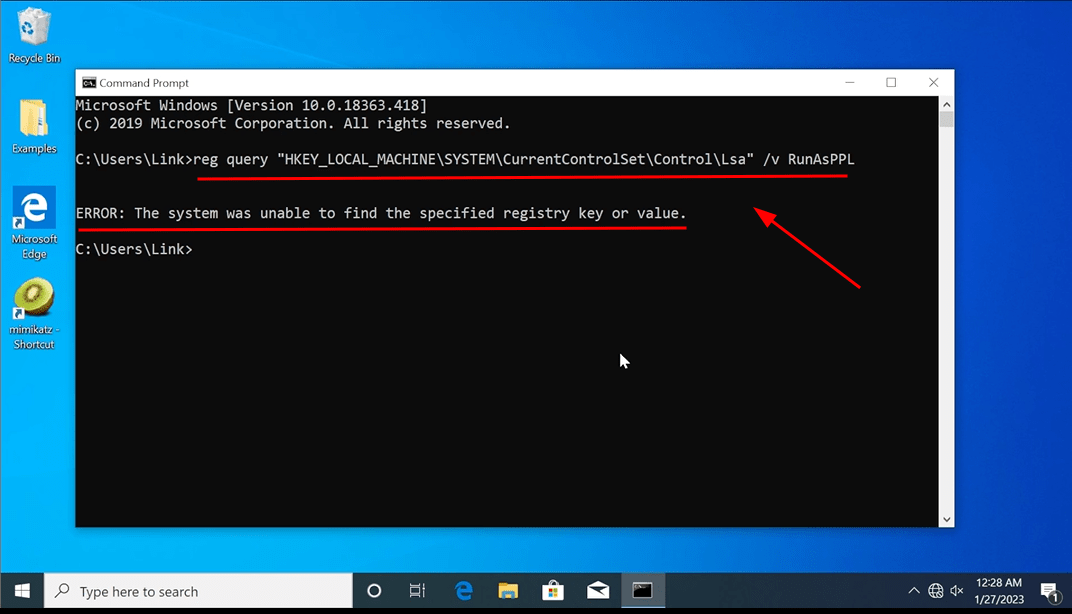
The following registry key check indicates that LSA protection is not configured.
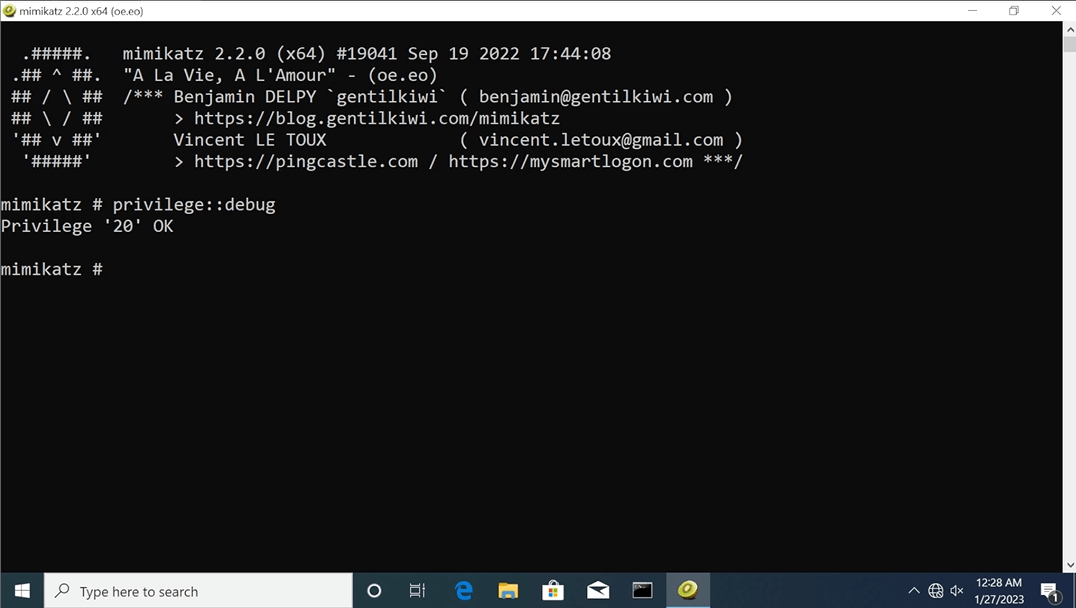
Now we load Mimikatz and prepare to dump credentials from the LSASS process.
Notice how Mimikatz is able to dump the user’s password hash, which can be used in Pass-The-Hash (PtH) attacks…
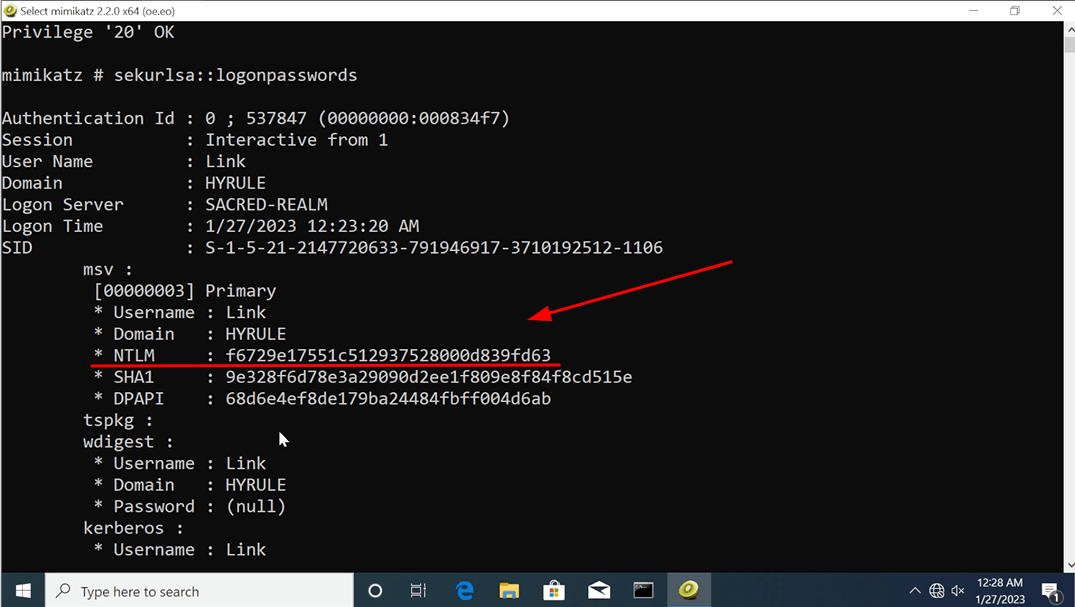
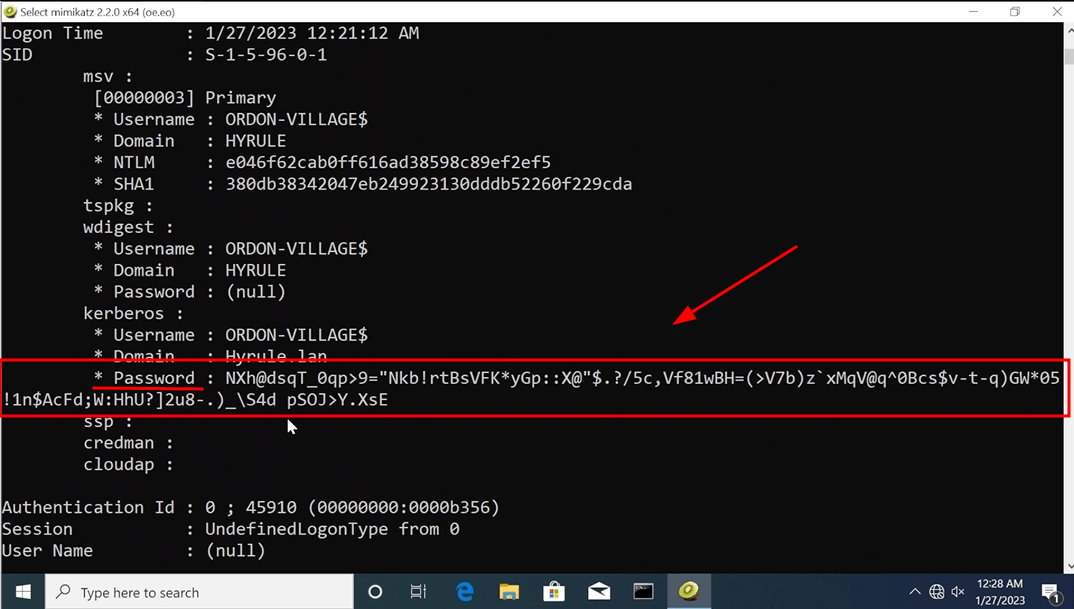
…As well as the machine account’s password.
Now after enabling LSA Protection, the following demonstration shows Mimikatz failing to dump any data from the LSASS process!
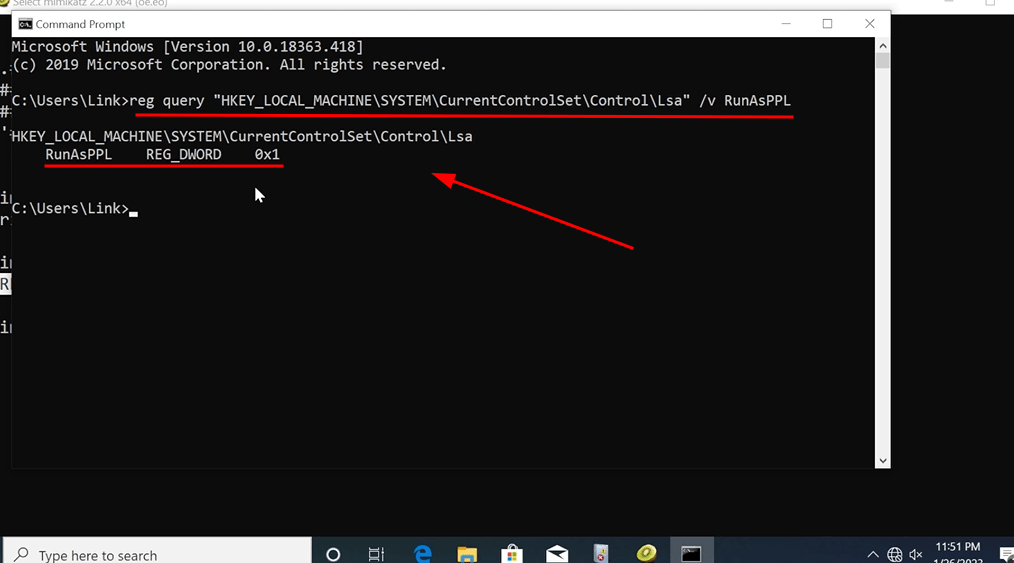
First, the following registry key check indicates that LSA protection is enabled.
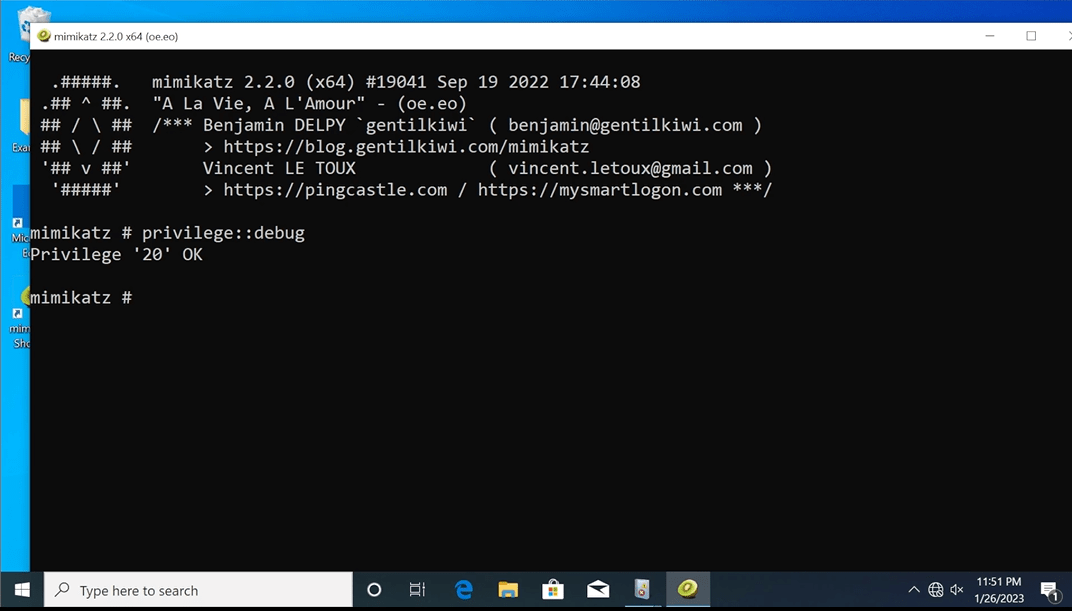
Now we load Mimikatz and prepare to dump credentials…
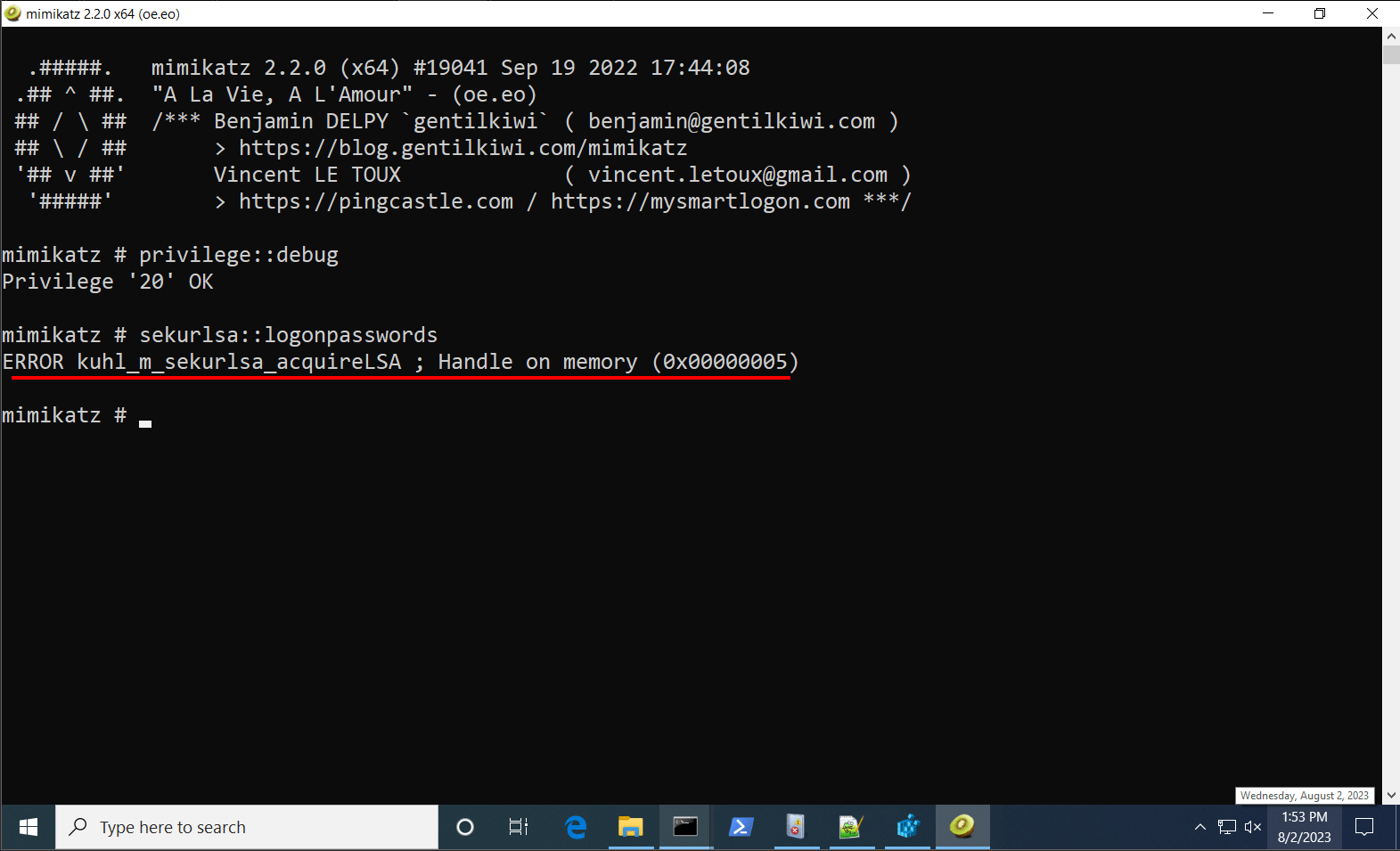
…And observe Mimikatz failing to do so.
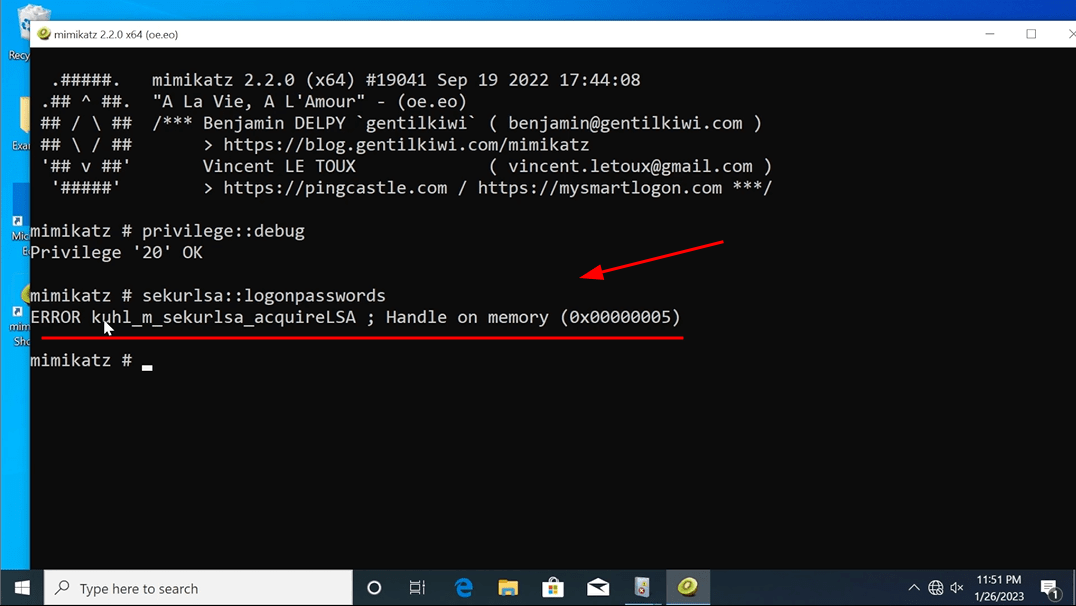
The error “0x5” is Windows talk for “Access denied”.
Credential Dumping Risk Eliminated! … Right? Well, as the saying goes, if there is a will…
What Is LSA Protection?
LSA Protection is a built-in security feature that protects against credential dumping attacks targeting a user’s credentials. While LSA Protection is simple to set up and a major obstacle against attackers, it is not completely hacker-proof. That said, this should not discourage you from implementing LSA Protection and adding a layer of defense. After all, attackers and defenders play a cat and mouse game, and the contest is never ending. Hackers will find a way to get what they want, no matter what.
In part 2, we’ll discuss methods and techniques to bypass LSA Protection and dump credentials.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...