Improving Quality-Of-Life With Simple Burp Suite Extensions (Part Two)
![from https://theiambic.com/marie-kondo-folding-method/ https://theiambic.com/wp-content/uploads/2020/07/Marie-Kondo-folding-method-600x600.jpg. [Kondo is what the "Sparks Joy" is referring to.]](https://blog.cyberadvisors.com/hubfs/Imported_Blog_Media/ANdWl1pEQJoi_yNQin6imI-dDzU-WFQxELYvG7qiZzncsG6ApRyVXX3IzMGOrrtcVDNjf95iVDY2qrM4W6lTrF8ie5dIxEQkf9dg9xM2812lwj9HtANjhD4elLCwlminYSl8wGM2vFccEldqDkVfV9E.png)
The “right tool for the job” isn’t always the perfect tool for the job, and if you have been using Burp Suite for a while, you probably have some ideas for small features to bring our favorite Web Pentesting tool just a little closer to perfect. Thankfully, we can develop extensions to avoid frequent annoyances and improve our pentesting. In this continuation of our series focusing on Quality-of-Life extensions, we’ll show off our new extension for “Subtractive Scoping”.
Subtractive Scoping Burp Suite Extension
Subtractive Scoping can help you declutter your Proxy History and enable more effective manual testing.
Burp’s typical “Additive Allowlist” scoping workflow is pretty straightforward:
- Browse to the target application using the proxy,
- Interact with the application,
- Add all relevant hosts to the Scope,
- Enable “Don’t send items to Proxy history if out of scope”.
The major downside with that final option is that you might miss out on important requests (like if your application calls a completely new API anytime after you enable the option). It’s a bit like horse blinders – you have a keen focus in one direction, but you’re clueless to anything else going on around you.
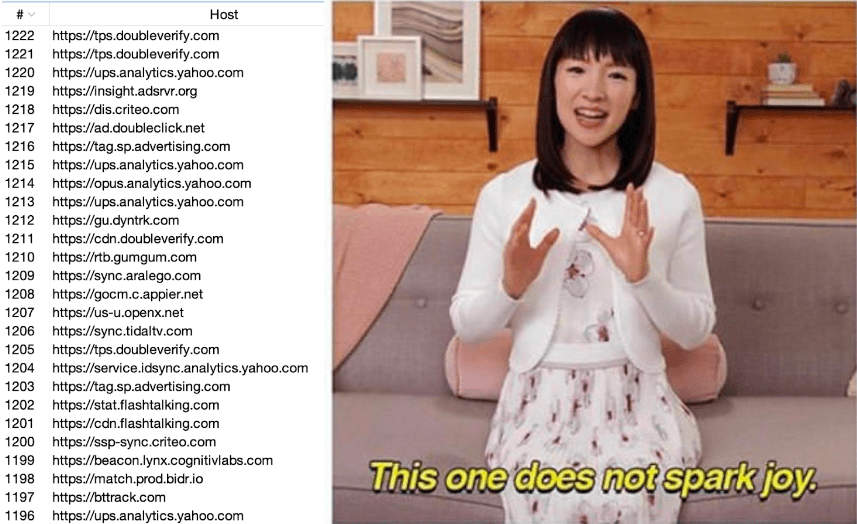
Unfortunately, modern applications often require judicious filtering when user tracking/marketing libraries are used; these libraries create numerous requests that can flood the Proxy History with garbage and make manual Interception extremely tedious. It’s vexing to work with the Proxy History when the important requests you are trying to click start running away from your cursor, flooding off the screen. The Proxy History only gives us one Filter to work with, which isn’t enough to both remove annoying hosts and effectively search for security concerns.
We need other scoping settings to work with.
Typical Tracking Hot Garbage from a Single Website (yahoo.com)
Subtractive Scoping Settings
We are going to use Burp’s Subtractive Scoping settings in addition to the existing Additive Allowlist workflow to take out the trash.
Instead of hunting through the Proxy History for our desired target hosts to add to the Scope, and then denying all non-Scoped traffic to the Proxy History, we’re going to use Burp’s TLS Pass Through settings to subtract away the unwanted hosts. “No details about requests or responses made via these connections will be available in the Proxy intercept view or history” – so this setting is perfect for ignoring these garbage-producing hosts during manual analysis.
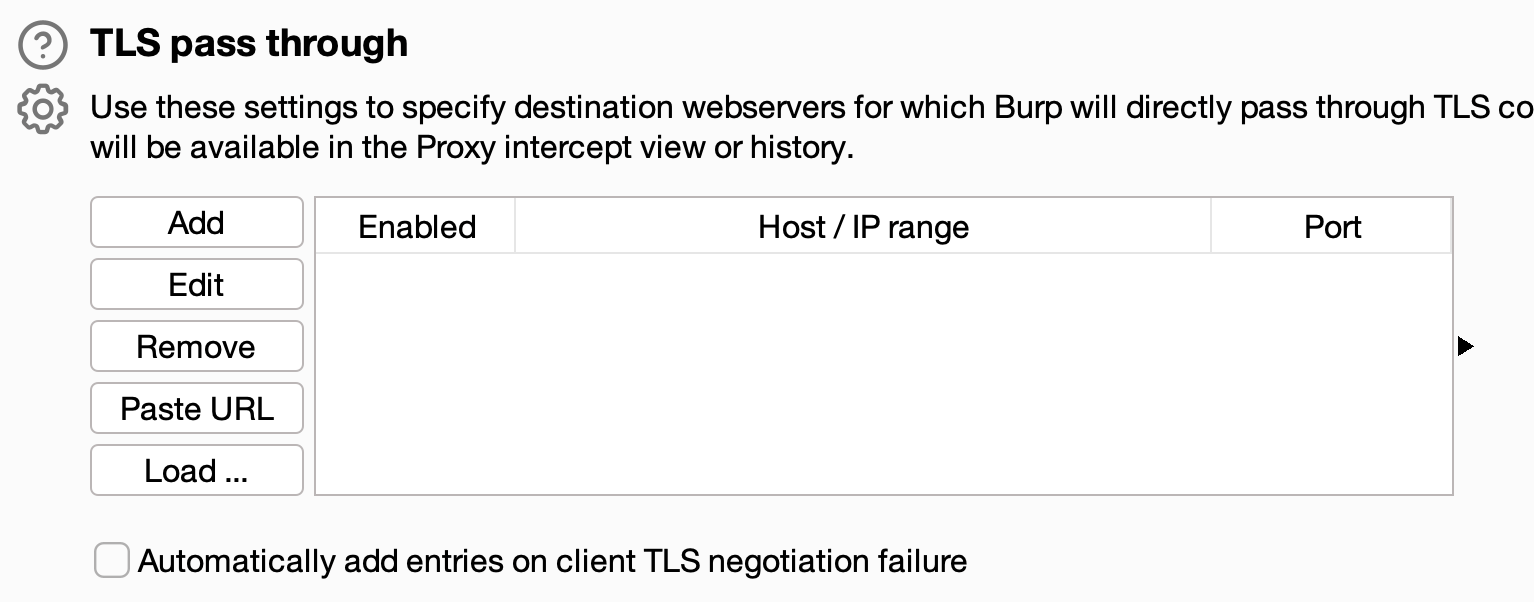
Unfortunately, this form is buried under three-clicks-and-a-scroll (Settings > Tools > Proxy > TLS Pass Through) and requires yet another window to interact with. The point of these settings is to speed up our testing and make our life easier, but having to juggle another window and input form becomes a copy-paste slog.
To make TLS Pass Through settings easily accessible within the manual testing process, we’ve developed a new Burp Extension, the “Add to TLS Pass Through” – this extension adds a new context menu to your Proxy History, Logger, and Target tools, allowing you to directly add the currently viewed host to the TLS Pass Through settings without leaving your place. Omit multiple hosts simultaneously by drag-selecting requests in the Proxy History, or work with a single host in the Proxy Intercept tab. Regular expressions to filter out multiple levels of subdomains are provided, and you can also simply hit “ALL” to TLS Pass Through every option at once.
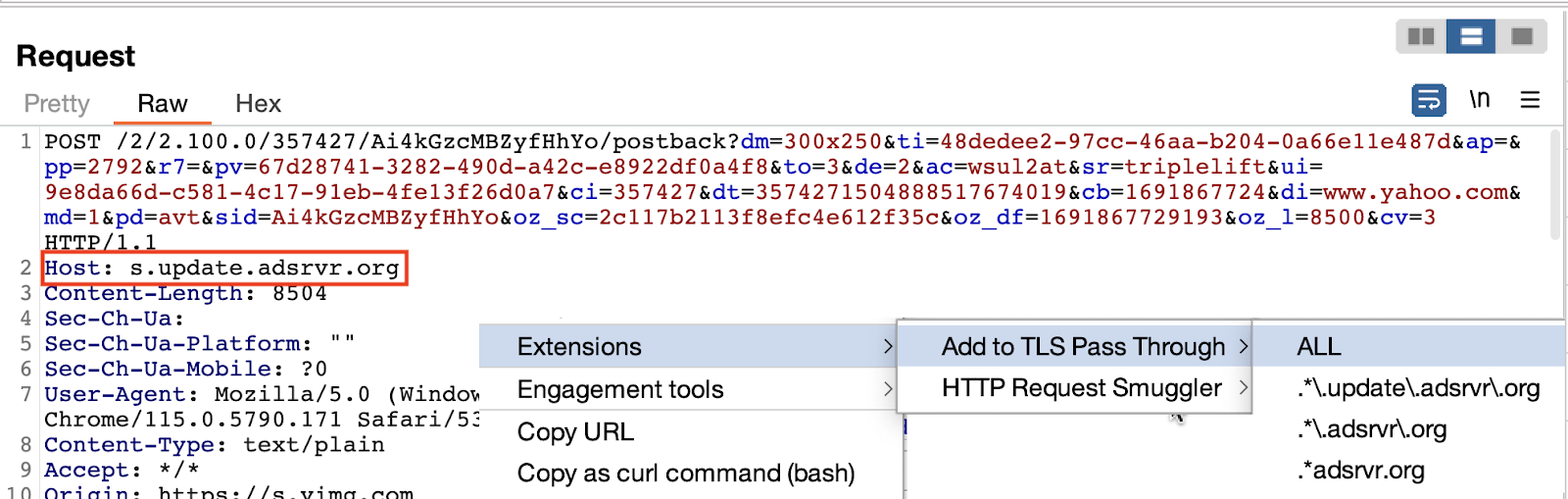
Subtractive Scoping Workflow
Our new Additive Allowlist with Subtractive Scoping workflow now looks like this:
- Browse to the target application using the proxy,
- Use the Proxy History Filter to view only out-of-scope traffic (select Show All, Show Only In-Scope Items, Negative Search to invert the selection, and Apply). Because we have a Negative Search for In-Scope Items, that means we can now use Add to Scope to do subtraction from the Proxy History too.
- [Subtractive Scoping] Remove uninteresting / garbage-producing hosts using “Add to TLS Pass Through”,
- [Additive Allowlist] Add relevant target hosts to the Scope. Do not select the option to omit out-of-scope items from the Proxy History if prompted,
- Continue Subtractive Scoping and Additive Allowlist actions iteratively until the Proxy History has stopped populating with both junk requests and interesting requests. Open new tabs for different target application pages to stimulate novel traffic, and you’ll be able to fairly quickly whittle the annoying hosts down, and add most of the important hosts to your Scope.
- Disable the Proxy History Filter (Show All) to view traffic as normal and free up the Filter to search for interesting requests.
Probably some junk API calls will still bubble up as you get to work with the application, but so will some important calls with vulnerabilities that you would have otherwise missed. Don’t forget to copy your TLS Pass Through regular expressions out of your project too – you can save them to your default project settings so you don’t need to spend time blocking common garbage-y hosts again.
Subtractive Scoping Tool
Hopefully, by now you’ve got an idea about how White Oak Security’s new extension can enhance your manual testing, and might even feel inspired to implement some improvements to Burp Suite yourself. Extension development takes a little bit of practice, but once you have interacted with the API a few times it gets a lot easier. If you’d like to learn more about Extension development, check out my first article in the series, (New Burp Suite Extension Will Knock Your SOCKS Off) which gets more into the code-level nitty gritty.
MORE FROM WHITE OAK SECURITY
White Oak Security provides deep-dive offensive security testing. We are a highly skilled and knowledgeable cyber security and penetration testing company that works hard to help organizations strengthen their security posture by getting into the minds of opponents to try to protect those we serve from malicious threats through expertise, integrity, and passion.
Our unique industry experience allows us to offer a wide range of services to help analyze and test information security controls and provide guidance to prioritize and remediate vulnerabilities.

