As remote work becomes increasingly prevalent, the importance of robust cybersecurity is more critical than ever. With businesses adapting to a dispersed workforce, the security landscape has grown, presenting new challenges and vulnerabilities. To navigate this changing environment securely, organizations must embrace best practices in remote work security and utilize cutting-edge tools from trusted providers like Fortinet, Sentinel One, Sophos, Veeam, and Microsoft. By incorporating these advanced solutions into their security framework, businesses can effectively protect their remote workforce and defend against a variety of cyber threats.
Implement Advanced Endpoint Protection
Sentinel One offers cutting-edge endpoint protection that uses AI to detect and respond to threats in real-time. Its autonomous platform is designed to identify and block malware, ransomware, and other advanced threats before they can cause harm. For remote workers, having such dynamic endpoint protection ensures that devices are continuously monitored and secured against the latest cyber threats.
Sophos provides comprehensive endpoint security with its Intercept X tool, which includes features like ransomware file protection and deep learning algorithms. This protects remote devices from new and evolving threats, which is essential for teams accessing company resources from various locations.
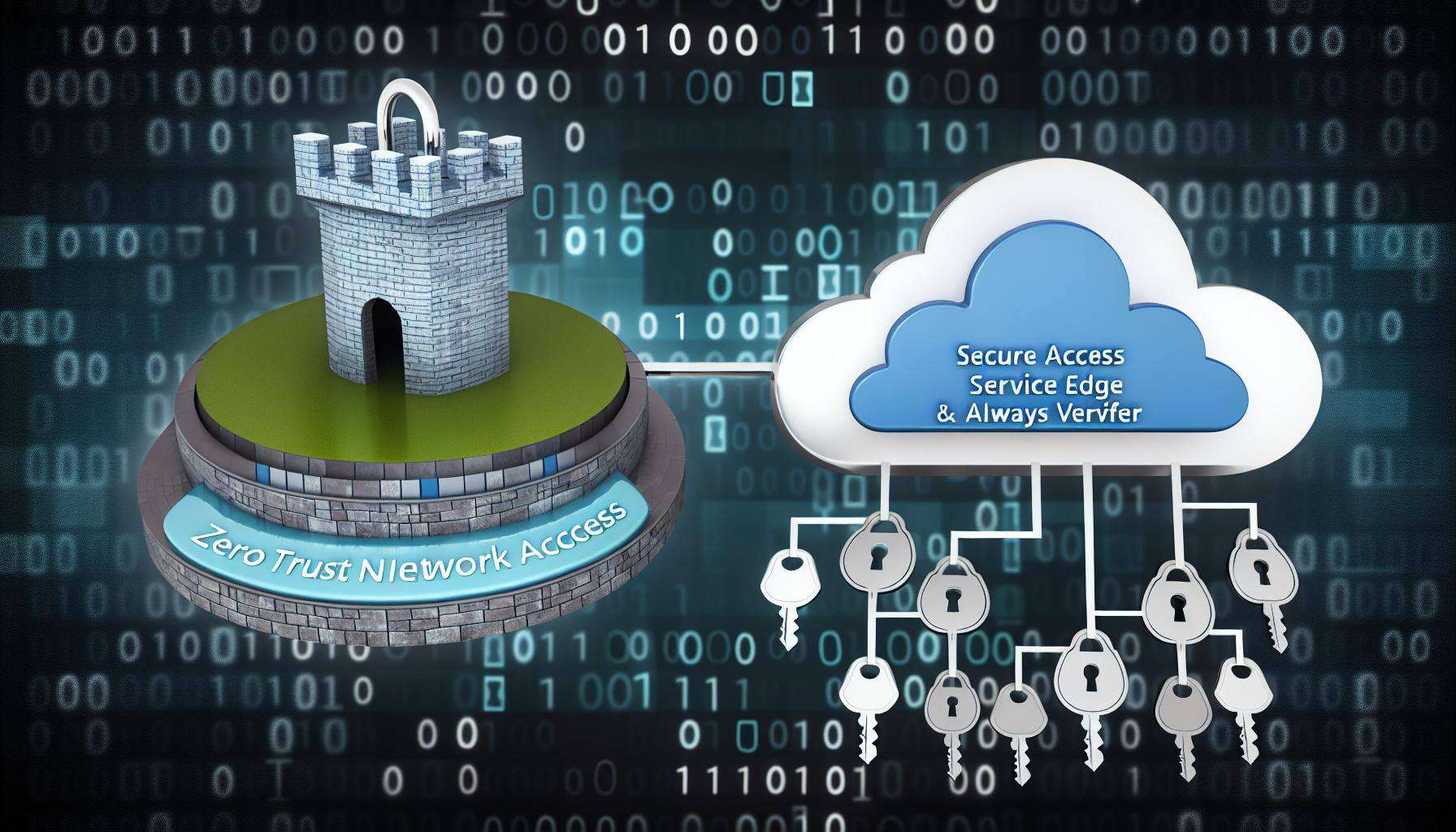
Secure Network Access with SASE and ZTNA
Fortinet offers innovative solutions tailored for the dynamic needs of remote work environments through its Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA) capabilities. These technologies are central to creating a secure and efficient network access environment for dispersed teams.

SASE: Streamlining Security and Network Performance
Fortinet's SASE solution integrates networking and security functions directly into the cloud, making it an ideal framework for organizations with remote workforces. This approach allows for consistent enforcement of security policies and protection across all endpoints, regardless of the user’s location. It combines WAN capabilities with cloud-native security functions such as secure web gateways, cloud access security brokers, and firewalls as a service. This ensures that remote connections are not only fast but also secure, handling threats proactively at the network edge.
ZTNA: Ensuring Controlled Access Based on Strict Verification
Zero Trust Network Access, or ZTNA, provides a more secure alternative to traditional VPN technologies. Fortinet’s ZTNA establishes access controls and verification procedures that are not merely based on the assumption that everything behind the corporate firewall is safe. Instead, ZTNA principles ensure that only authenticated and authorized users and devices can access specific applications and data. This method minimizes the attack surface by providing access on a "need-to-know" basis, significantly enhancing security for remote operations.
By leveraging Fortinet’s comprehensive SASE and ZTNA offerings, businesses can ensure that their remote workforce accesses the corporate network securely and efficiently, aligning with the best practices for remote work security. This not only improves overall security posture but also supports optimal performance and user experience in a remote setting.
Enhance Data Protection and Backup Solutions
Veeam specializes in backup and disaster recovery solutions that are essential for safeguarding the data accessed by remote workers. With Veeam's advanced technology, businesses can rest assured that all critical remote work data is continuously backed up in real-time, creating a reliable safety net in the event of data loss or a cybersecurity breach. This proactive approach not only minimizes downtime but also ensures seamless business continuity, allowing organizations to quickly recover and resume operations without disruption. Veeam's robust backup and recovery solutions offer peace of mind and a solid foundation for maintaining the integrity and availability of remote work data, safeguarding against potential threats and unforeseen challenges.
Utilize Secure Collaboration Tools
Microsoft offers several secure communication and collaboration tools through its Microsoft 365 suite, including Teams and SharePoint. These platforms are built with security at their core, featuring data loss prevention, advanced threat protection, and compliance capabilities. By using these tools, remote teams can collaborate safely, knowing their communications are protected against unauthorized access and threats.
Regular Security Training and Awareness
Educating your workforce on cybersecurity goes beyond just providing tools and technologies. It's about empowering your employees to become the first line of defense against cyber threats. Regular security training sessions are crucial for instilling a culture of vigilance and awareness within your organization. By educating your team on the latest phishing techniques, the importance of strong password management, and the risks associated with using public Wi-Fi, you are equipping them with the knowledge and skills needed to protect themselves and the company from potential cyber attacks. This proactive approach not only strengthens your remote work security posture but also cultivates a security-conscious mindset among your employees, making them active participants in safeguarding the organization's digital assets.
Conclusion
Implementing these best practices and leveraging top-tier security tools from Fortinet, Sentinel One, Sophos, Veeam, and Microsoft can significantly enhance your organization’s security framework, especially in a remote work environment. Each tool brings a unique set of capabilities that, when combined, provide a comprehensive, layered security strategy that is robust enough to protect your business from the complexities of modern cyber threats. In today’s interconnected world, equipping your remote workforce with these tools and knowledge is not just an option—it’s a necessity.
For more detailed information on how these tools can be integrated into your specific IT environment, or to discuss a customized security solution that fits your business needs, reach out to our experts at Cyber Advisors. We are here to help you navigate the security challenges of remote work with ease and confidence.
Get in touch with us today!
Let’s Talk
Recent Blogs
Modern Collaboration Tools That Power Hybrid Work
Unified collaboration connects people, content, and processes in a single workspace, enabling…
2026 Cybersecurity Trends Every SMB Must Prepare For
2026 Cybersecurity Trends Every SMB Must Prepare For SMB attack surfaces expanded in 2026—more…
What Tools & Services Do Manufacturers Need to Achieve Cyber Maturity?
Reaching cyber maturity in manufacturing isn’t about buying a single platform. It’s about…