Every device in your organization—from laptops and mobile phones to servers and SaaS licenses—has a lifecycle. Each asset carries not just a price tag, but a potential return on investment (ROI), a security risk, and a measurable impact on your workforce productivity.
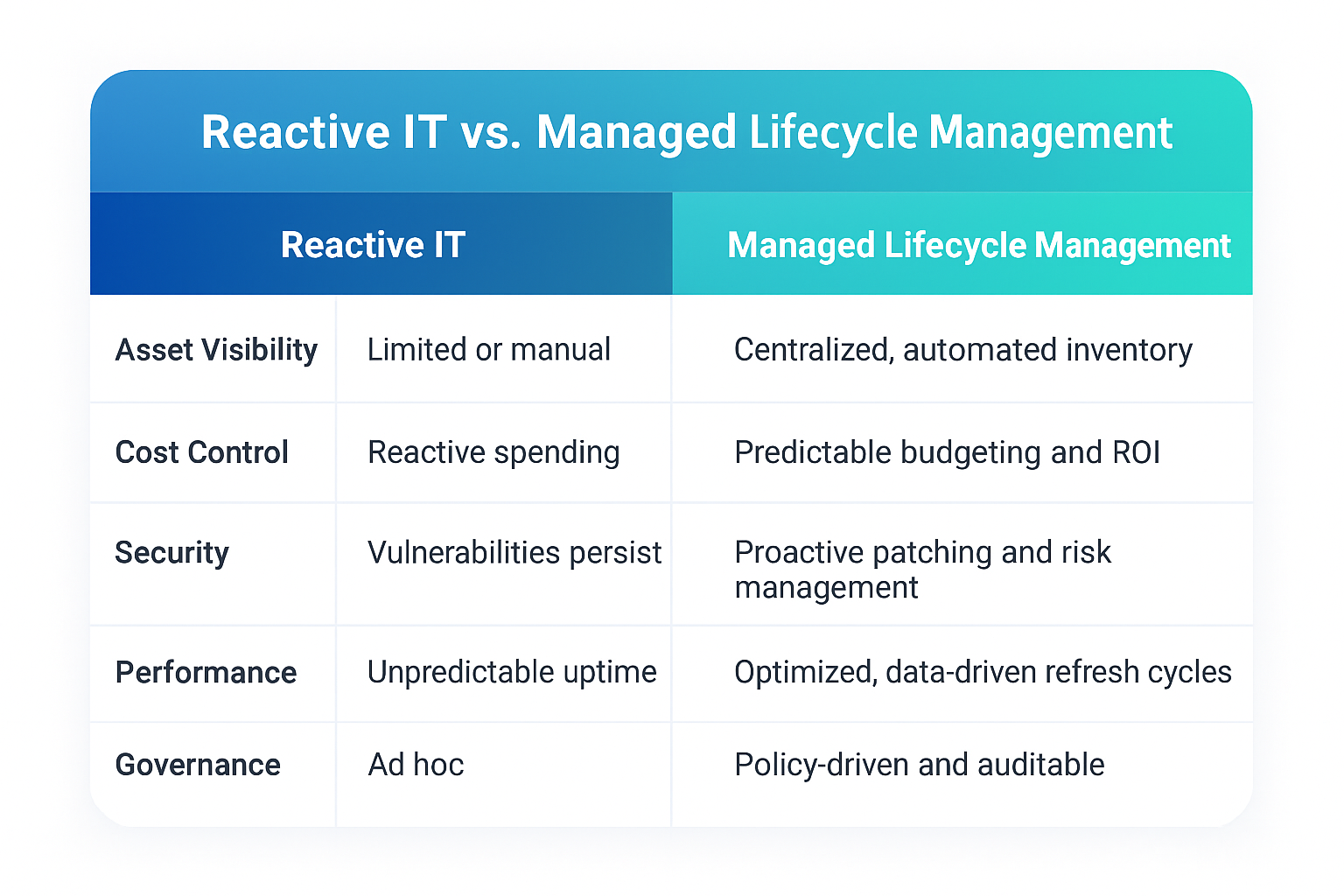
A disciplined IT asset management (ITAM) program forms the connective tissue between budgeting, security, and the ongoing supportability of every piece of technology in your environment. Executed effectively, ITAM ensures that each technology investment is purpose-driven, continuously monitored, and consistently delivers measurable value throughout its entire lifespan—from deployment on day one through secure retirement.
In a world defined by hybrid work, multi-cloud complexity, and a proliferation of endpoints, lifecycle management can no longer rely on static spreadsheets or basic inventory methods. Instead, true IT lifecycle management emphasizes structured governance, operational optimization, and an ongoing pursuit of improvement. This evolution allows organizations to not only track assets but also to intelligently manage them in alignment with business objectives and regulatory demands.
In this post, we will explore how building a comprehensive, end-to-end lifecycle strategy—from procurement and deployment through ongoing management and secure retirement—can mitigate operational and compliance risks, maximize your technology ROI, and lay the groundwork for resilient, future-ready IT operations.
Why End-to-End Lifecycle Management Increases ROI, Reduces Risk, and Improves User Experience
When IT investments are made haphazardly—without a unified, end-to-end lifecycle strategy—organizations frequently encounter unnecessary expense, redundant purchases, and heightened security risk. Unused hardware accumulates in storage closets, software licenses remain untracked and underutilized, and outdated devices become breeding grounds for unaddressed vulnerabilities.
A mature IT lifecycle management program eliminates these pitfalls by establishing a clear, governed structure that tracks and manages every technology asset—both physical and digital—from initial procurement through to secure retirement. This structured approach ensures that assets are strategically acquired, actively monitored throughout their lifespan, maintained in accordance with policy, and ultimately decommissioned in a compliant and secure manner.
By embedding lifecycle governance into your operations, you gain continuous visibility over your IT environment, reduce risk exposure, drive operational efficiency, and are better positioned to meet evolving regulatory requirements. Let’s break down the key business outcomes of this approach.
1. Maximizing ROI Through Strategic Planning and Optimization
Lifecycle management turns technology from a cost center into a performance engine. By defining clear standards for procurement, deployment, and refresh, organizations can extract full value from every asset while minimizing waste.
Consider the average device lifecycle: most organizations replace laptops every three to five years. Without proper tracking, many devices are replaced too early (wasting budget) or too late (reducing productivity and increasing maintenance costs).
A proactive ITAM program allows you to:
-
Forecast refresh cycles based on usage and performance data.
-
Align technology investments with actual business demand.
-
Reduce total cost of ownership (TCO) by extending useful life without compromising efficiency.
When you plan IT like a portfolio—balancing risk, return, and utilization—you gain measurable ROI from every dollar spent.
2. Reducing Risk Through Governance and Standardization
Every unmanaged asset is a potential vulnerability. Endpoints that fall outside patch cycles or untracked licenses can expose your network to unnecessary risk.
By establishing a governed lifecycle framework, you ensure that every device, application, and license is tracked, updated, and retired in accordance with policy. Governance also involves standardization—selecting approved models, configurations, and vendors to simplify management and enhance the security posture.
Governed IT lifecycle programs:
-
Centralize inventory and contracts for full visibility.
-
Enforce compliance with internal policies and external regulations.
-
Create a clear chain of custody for devices from purchase through disposal.
Standardization and governance together enable the operation of IT environments that are both scalable and secure—without hindering innovation.
3. Improving the User Experience Through Consistency and Predictability
While lifecycle management is often framed as a cost or risk discipline, it also has a powerful impact on user satisfaction.
When devices are provisioned consistently, updated regularly, and supported proactively, employees experience fewer disruptions and faster issue resolution. The result is a smoother digital workplace—one where technology empowers productivity instead of hindering it.
Key UX benefits of IT lifecycle management:
-
Predictable refresh cycles ensure employees always have performant, secure devices.
-
Standardized builds reduce support tickets and helpdesk burden.
-
Automated deployment processes enable faster onboarding and reduced downtime.
The user experience is ultimately the most visible outcome of effective IT management. A well-governed lifecycle program helps your workforce feel the difference—every day.
How to Design a Governed Lifecycle Framework Across Procure, Deploy, Manage, Refresh, and Retire
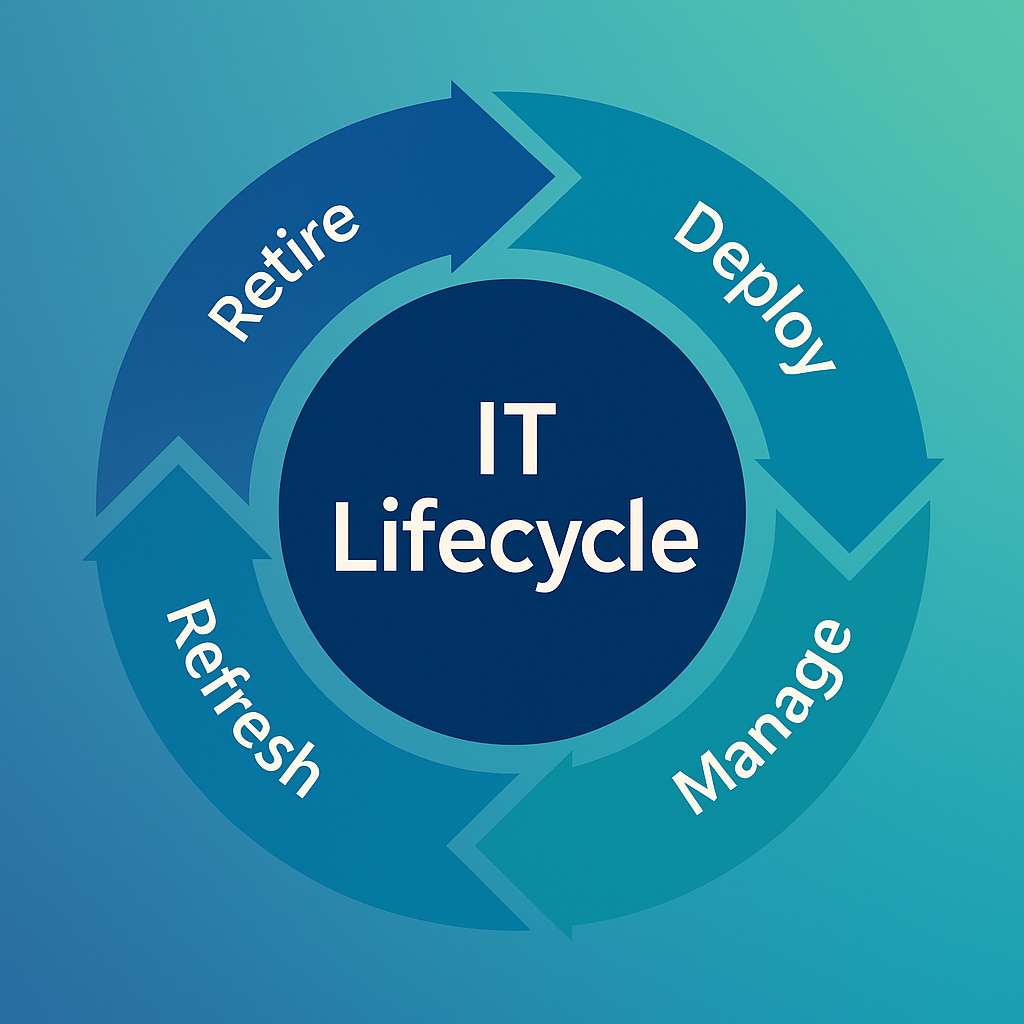
A comprehensive lifecycle management program is designed to orchestrate every phase of an asset’s journey with precision and intent. Its purpose is to ensure that each transition—from procurement and initial deployment, through ongoing management and timely refresh, to secure and compliant retirement—is handled seamlessly, optimizing both security and operational efficiency while controlling costs at every step. By tightly integrating these phases, organizations gain the ability to make informed decisions, quickly adapt to changing business needs, and maintain a robust defense against emerging threats. Each stage in the lifecycle represents an opportunity to maximize value, minimize risk, and improve the user experience.
Let’s examine how a well-governed approach at every point can transform your IT environment.
Procure: Align Purchases with Standards and Strategy
Procurement is where lifecycle efficiency begins—a stage that sets the tone for an asset’s entire journey within your organization. Selecting and approving devices, licenses, and software subscriptions should be an intentional and strategic process rooted firmly in actual business requirements, rather than being influenced by last-minute requests or opportunistic deals.
Key practices at the procurement stage:
- Establish a catalog of approved models and vendors. By standardizing asset selection, you ensure that all devices and technologies introduced are compatible with your environment, meet security baselines, and align with organizational policies.
- Integrate procurement workflows with asset tracking systems to streamline operations. This connection enables real-time visibility from day one, allowing IT and finance teams to monitor asset allocation, manage inventory accurately, and enforce compliance with purchasing policies.
- Require lifecycle cost justification, not just approval of the purchase price. Consider the total cost of ownership, including support, maintenance, licensing renewals, and eventual decommissioning. This holistic view ensures that every technology investment is evaluated based on its long-term value, not just its upfront savings.
By setting and enforcing procurement standards upfront, you minimize downstream complexity, reduce variations in support requirements, and increase overall manageability. This foundational discipline enables smarter use of budget, tighter control over compliance, and a more resilient IT environment as your operations evolve.
Deploy: Standardize and Automate for Speed and Accuracy
The deployment phase is where governance and operational excellence converge to set the tone for the asset’s lifespan. By embracing rigorous standards—such as uniform device images, well-defined configurations, and tightly managed security policies—organizations can streamline setup processes, minimize manual intervention, and reinforce compliance from the outset. This disciplined approach not only accelerates time to value but also ensures a secure and predictable user experience from day one.
Best practices for deployment include:
- Leveraging standardized operating system images and curated software bundles to ensure every device is provisioned identically and in line with company policies.
- Automating provisioning through advanced tools like Microsoft Intune or Windows Autopilot, which enable IT teams to configure devices remotely, apply security baselines, and deploy required applications at scale with minimal touch.
- Proactively validating security and compliance controls—including device encryption, multi-factor authentication (MFA), endpoint protection, and granular access policies—prior to placing systems into production.
Taking this automation-first approach to deployment yields more than just time savings for IT teams; it paves the way for greater business agility, allowing new users and devices to be onboarded rapidly without sacrificing oversight. Every endpoint that joins the organization’s ecosystem arrives in a known-good, compliant state—reducing risk, increasing operational velocity, and setting a foundation for ongoing lifecycle excellence.
Manage: Centralize Inventory, Performance, and Governance
Once devices and licenses are active, visibility becomes critical. Without centralized tracking, assets can quickly drift off-policy or out of inventory, creating blind spots that increase security and compliance risk while eroding operational efficiency.
To address these challenges, an optimized management layer should provide comprehensive capabilities for monitoring and controlling your entire technology ecosystem:
- Real-time asset discovery across all environments—including on-premises infrastructure, hybrid deployments, and cloud platforms—so you always know what is connected, where it resides, and which resources may require immediate attention.
- Centralized inventory management for hardware, software, and licensing to maintain an up-to-date, accurate view of asset ownership, allocation, and utilization. This ensures that nothing slips through the cracks during audits or refresh cycles, helping to eliminate waste from unused or underutilized resources.
- Seamless integration with IT service management (ITSM) tools to automate ticketing, patch deployment, and compliance reporting. This connected approach enables rapid response to incidents, keeps systems properly maintained, and supports regulatory obligations with consistent documentation.
Unifying these functions within a single pane of glass empowers IT and business leaders to make proactive, data-driven decisions about refresh cycles, performance tuning, and resource allocation. Centralized management not only streamlines day-to-day operations but also strengthens accountability and transparency across departments and technology domains.
This is also where governance frameworks—such as ITIL, NIST, or ISO 27001—can be directly mapped into operational practice, embedding policy controls into your management workflows. By aligning daily activities with recognized standards, you bring rigor to asset management processes, ensuring ongoing compliance, security, and operational excellence.
Refresh: Align Replacement Cadence to Performance and Risk
One of the most overlooked lifecycle phases is refresh—the critical point when assets are assessed to determine whether their ongoing value justifies continued use or if replacement is the wiser investment. Refreshing assets prematurely can drain valuable capital and result in underutilized technology, while postponing replacement until failures occur may expose your organization to security vulnerabilities, operational disruptions, and compliance gaps. Achieving the optimal refresh cadence requires a deliberate balance, aligning asset replacement with concrete indicators of performance, evolving security requirements, and vendor supportability.
Best-in-class refresh management leverages both operational data and risk insights to guide decisions:
Deploy robust data analytics platforms to monitor usage trends, flagging performance degradation, upticks in incident rates, and support interventions. This enables IT to identify at-risk assets before user productivity suffers.
- Establish tiered refresh schedules based on device classification, business function criticality, and warranty coverage to optimize maintenance and support. Mission-critical infrastructure and endpoints handling sensitive information should be prioritized for earlier refresh, while non-essential assets may follow an extended cycle.
- Integrate OEM support timelines and ongoing cybersecurity risk assessments into your planning. Replace assets ahead of end-of-support dates and in response to newly identified threat vectors, ensuring security posture never lags behind emerging risks.
A strategic, metrics-driven refresh plan protects productivity and resiliency—enabling users to operate on reliable, high-performing technology while safeguarding data and operations against potential threats. Every investment in asset replacement is intentional, directly reinforcing organizational reliability, performance, and the capacity for workforce innovation.
Retire: Securely Decommission and Dispose of Assets
The retirement phase is where governance pays its final dividend. Secure, compliant disposal safeguards sensitive information, demonstrates environmental responsibility, and protects your organization’s reputation from avoidable risk.
Critical steps for asset retirement include:
- Enforcing secure data wipe using certified and auditable destruction tools, ensuring that all organizational and regulated data is permanently eliminated prior to disposal.
- Obtaining verifiable proof of destruction and chain-of-custody documentation, supporting audit readiness and regulatory compliance.
- Reclaiming licenses, peripherals, and reusable components to maximize residual value, reduce unnecessary repurchasing, and promote sustainable IT practices.
Modern IT asset management (ITAM) programs take it a step further by integrating directly with certified recycling and e-waste management partners. This end-to-end approach ensures that every asset is retired in full alignment with state, federal, and industry-specific environmental regulations—all while maintaining data protection standards and supporting your organization’s ESG initiatives. By embedding these controls into the final stage of the lifecycle, you minimize liabilities, support compliance, and close the loop on responsible technology management.
Key Principles for a High-Performance Lifecycle Framework
Building a mature lifecycle program requires a disciplined process and visibility. Cyber Advisors helps clients implement proven ITAM practices that strike a balance between governance and agility.
Here are the key elements that drive success:
-
Standardize models and images for speed. Reducing the number of device models and software images shortens deployment time, simplifies patching, and improves support quality.
-
Centralize inventory and contracts for visibility. Real-time dashboards give IT leaders control over asset utilization, performance, and cost.
-
Align refresh cadence to performance and risk. This ensures hardware and software stay within optimal lifecycle windows—improving ROI and minimizing exposure.
-
Enforce secure wipe and certified disposal. Protect sensitive data and maintain compliance throughout the entire procurement and retirement process.
The Business Case for IT Lifecycle Management
Lifecycle management isn’t just a technical function—it’s a financial and strategic one.
According to Gartner, organizations that adopt mature ITAM practices can reduce total technology costs by up to 30% while improving asset utilization and compliance.
Financial Benefits:
-
Reduced capital expenditure through smarter procurement.
-
Lower operational costs via automation and standardization.
-
Predictable budgeting through lifecycle cost modeling.
Operational Benefits:
-
Improved uptime and productivity through consistent refresh cycles.
-
Enhanced security posture by retiring unsupported assets.
-
Streamlined vendor management and contract renewals.
Strategic Benefits:
-
Alignment of IT investments with organizational goals.
-
Better data for decision-making and forecasting.
-
Reduced risk across compliance, audit, and cybersecurity domains.
Lifecycle management, done right, becomes an enabler of digital transformation—not just a maintenance exercise.
How Cyber Advisors Helps Optimize the IT Lifecycle
At Cyber Advisors, we help organizations design and implement end-to-end lifecycle management frameworks that strike a balance between governance, agility, and innovation.
Our approach combines strategic IT asset management (ITAM) with hands-on managed services to give you full visibility and control over your technology investments.
Cyber Advisors IT Lifecycle Services Include:
-
Asset discovery, inventory, and tracking solutions.
-
Procurement standardization and vendor management.
-
Deployment automation and endpoint security integration.
-
Lifecycle reporting and KPI dashboards.
-
Secure decommissioning and data destruction.
We collaborate with IT and finance leaders to develop a unified lifecycle strategy that supports business growth while minimizing operational friction.