Throughout World War I, trench warfare was used by each side to both gain ground and to hold off attacks. These trenches used multiple defenses to slow or stop advancement by troops: parapets, mortar shells, mustard gas, mines, barbed wire and other nasty tools were heavily deployed. This multi-layered approach was implemented to thwart the various attack vectors that the enemy might use. Barbed wire, for example, is effective against soldiers, but not so much against tanks. This is where mines and mortar shells were far more useful. In the famous Battle of the Somme, trench warfare was so difficult that only miles were gained by the end of the war.
Why the history lesson? Because understanding the past can help you prepare for the future.
Today’s attackers may not be soldiers with guns and bayonets, painfully struggling to increase their territory and positon. The attackers of our time are cybercriminals, hacktivists, state-sponsored hackers, internal disgruntled employees and others. These ‘threat actors’ use a multitude of tools in their arsenal to defeat our defenses for their nefarious purposes. In response, we must take the strategy of trench warfare and apply it to our business information systems. Like the multiple tools used by commanders to slow attackers, we must employ a multi-tiered approach as to slow or halt the different kinds of technical assaults. This approach is commonly referred to as “Defense in Depth”.
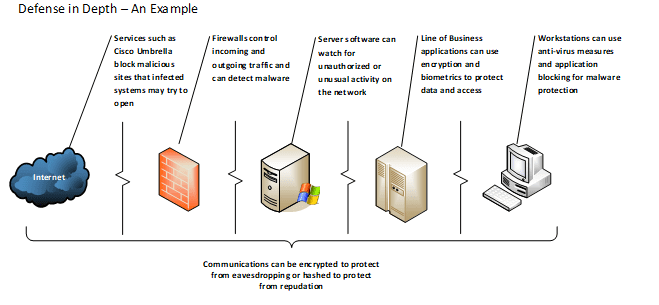
‘Defense in Depth’ is a strategy that requires the utilization of multiple tools or systems to match various points of attack:
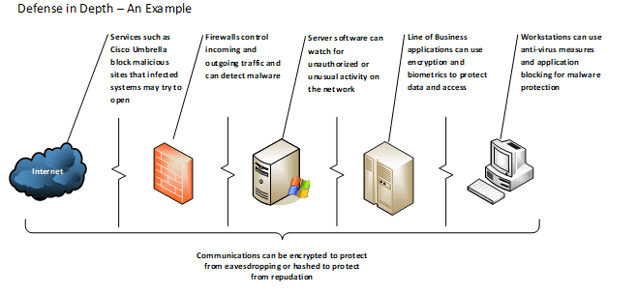
As you can see, each layer provides a level of protection for the end-user. If malware, hackers or insider threats break through one wall, there is another to slow or halt their continued progress. So long as every point is carefully maintained and monitored, this strategy can be useful in protecting your business systems and users. Like the trenches of old, the tools and systems we implement can mean the difference between safety from threats and complete overrun by them.