One of the many services that White Oak Security offers is Onsite Social Engineering. As a pentester, I have performed 50+ physical onsite social engineering engagements over my professional career and I always bring my social engineering toolkit. This post will discuss the items I have in my toolkit bag and potentially introduce you to some helpful, handy tools.
Social Engineering Testing Tools
Now the following items are what I have included (but not limited to) MY toolkit, these can vary from pentester to pentester.
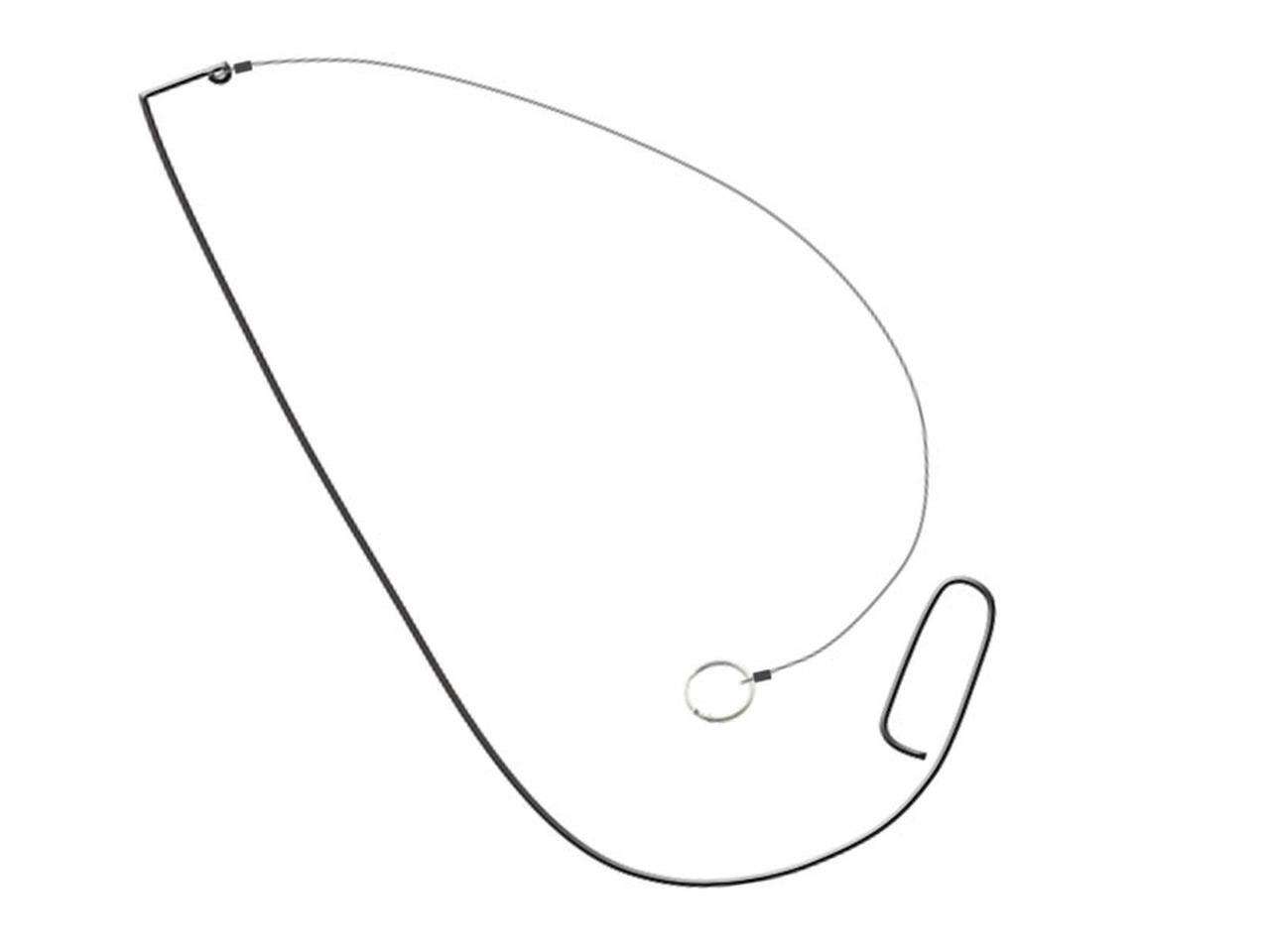
Under The Door Tool
The Under The Door Tool (UTDT) can be used to open level handle doors from the outside via reaching under the door. This tool is super easy to use, just slide it under the door and work it up over the latch. Once in place, pulling down on the cable will move the handle and open the door. The UTDT is very inexpensive – roughly $30, which makes it a no-brainer for anyone doing social engineering engagements. The one caveat is that it can be fairly big, however, I have gotten it to fit within a larger laptop bag!
Lock Pick Tools
I tend to keep a standard set of various lock picks on hand, but also like to include the following:
- Shove knife
- Bump hammer with bump keys
- 7 & 8 pin tubular picks
- Plug spinner
There are a ton of different companies that offer different setups – but one that comes with most of the items needed is this Tactical Entry Kit from Lock Pick Tools (shown below).

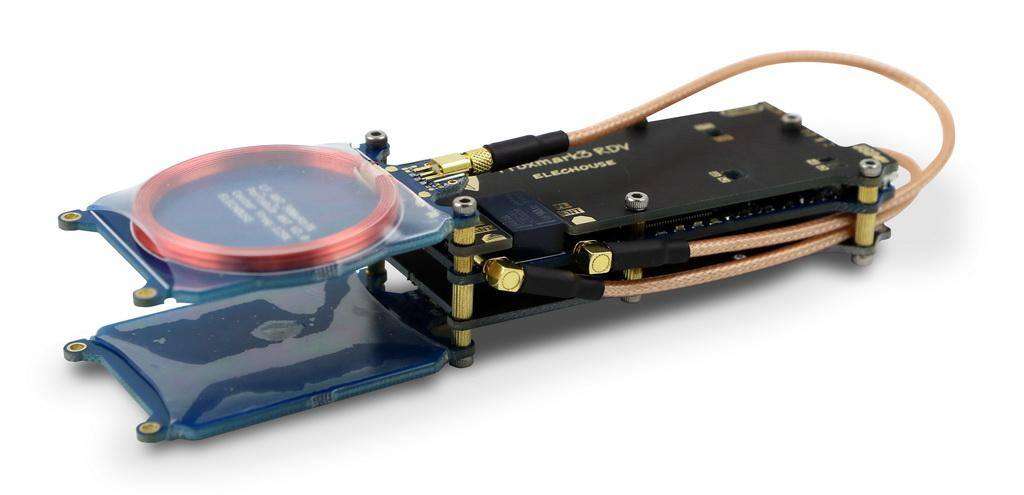
RFID
On the RFID side of the house, I like to keep a spare Proxmark3 RDv2 setup. It allows me to clone, emulate, and even brute force RFID cards. Taking it even further – I also include White Oak Security’s own Skim Job toolset if I am targeting low-frequency HID Prox style cards. I also have a couple of blog posts on utilizing this specific Proxmark3.
Network Access
Other items I tend to consider keeping on hand include (but again, are not limited to the following lists.
- Mini wireless access point
- Ethernet cables
- HAK5 toolkit
- Laptop
Identification
- Legitimate identification (driver’s license)
- Get out of jail letter (client authorization letter)
- Personal business card
- Fake business cards
- Fake employee badges w/lanyards
Miscellaneous
- Flashlight
- Scissors
- Pen
- Clipboard
- Canned air
- Tape
THE Bag
I try to keep all of these tools within a larger laptop carrying bag (shown below).

What’s In Your Bag?
Depending on the engagement and what the client considers to be in-scope the items contained within my social engineering toolkit bag can differ all the time. Typically, when attempting to gain access into a building – I try to keep my setup light, just for quick moving around. Once I establish consistent access, I tend to bring more items in to start testing different controls within the building.
