What Is Nuclei?
Nuclei is a powerful open-source vulnerability scanner written in Golang. Aside from its excellent performance, it is a highly customizable tool due to its integration with YAML template files. Its templating system allows for anyone to create vulnerability templates and contribute their findings to the community!
Nuclei & Burp Suite
We have lots of blogs regarding Burp Suite you can always check out here.
For web application testing, there is a Burp Suite community plugin in the BApp store called the Nuclei “Template Generator Plugin” that is even available for users who use the free community edition. The purpose of this plugin is to assist with repetitive data associated with nuclei template creation. When the plugin is installed, a tab is added to the app layout like the Repeater, Intruder, etc. It also features integration with Repeater and Intruder for simplified template generation.
Metasploitable2
To demonstrate how the plugin works, I set up a virtual environment with Metasploitable2 as my vulnerable target. For those not familiar with Metasploitable, it is an intentionally vulnerable machine for educational and testing purposes. Below shows the home page of the VM with options to various locally hosted vulnerable applications.

I will also be using the phpMyAdmin page to demonstrate how multiple requests can be added to the resulting template. I choose both of these pages because they both mention phpMyAdmin, but one would actually be a false positive if indicated.
Nuclei Demonstration
I started out running the default Nuclei scan including all the templates available. In addition, I added rate limiting parameters which limit to three requests per second, allowing parallel execution of two templates simultaneously. By default, Nuclei has almost 6,300 templates available and actively continues to grow!
Default Nuclei scan command:
nuclei –u <target_url> -rl 3 -c 2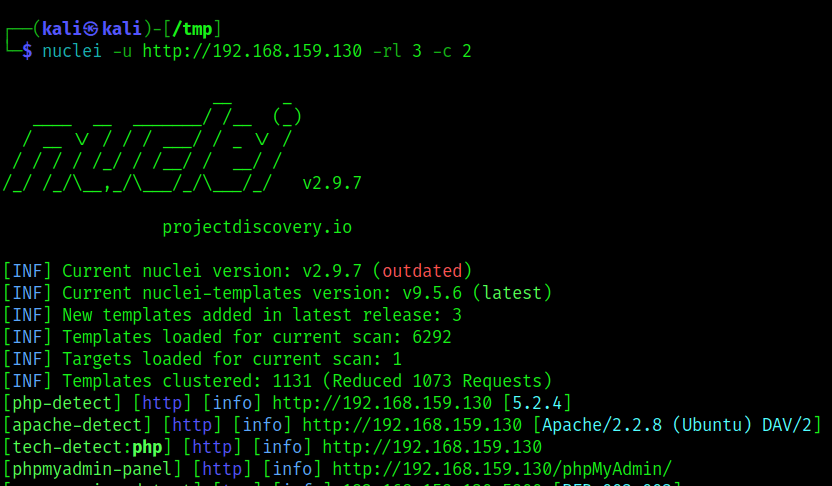
Due to how vulnerable Metasploitable is, the tool indicated many alerts of indicators of vulnerabilities. However, for the objective of explaining how the plugin works, lets focus on the last indicator in the screenshot named “[phpmyadmin-panel]”.
After running the initial Nuclei scan, I switched to my Burp Suite web proxy for template generation. Before generating templates on the target request, it is always a good practice to add the target URL to the scope, which allows to filter requests by the in-scope URL. To do this, go to the “Target” tab, right click on the target, and add the target to scope.
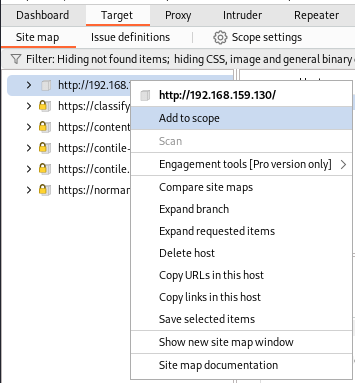
Once the target is added to scope, all entities out of scope can be easily filtered out by clicking on the grey filter bar toward the top of the application and selecting “Show only in-scope items”.
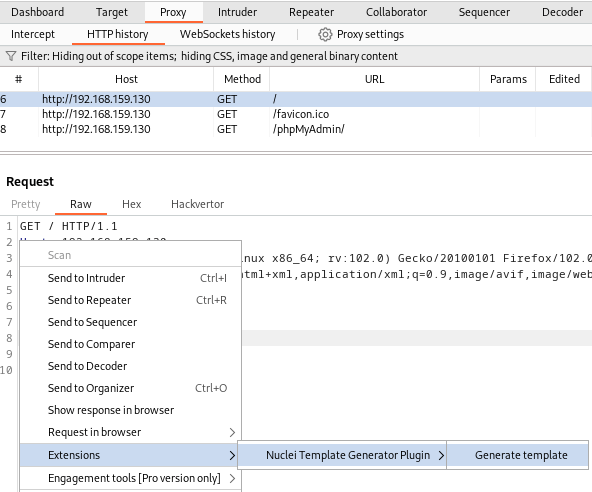
To add the home page request by simply right clicking on the request and following the extensions tabs to generate a template.
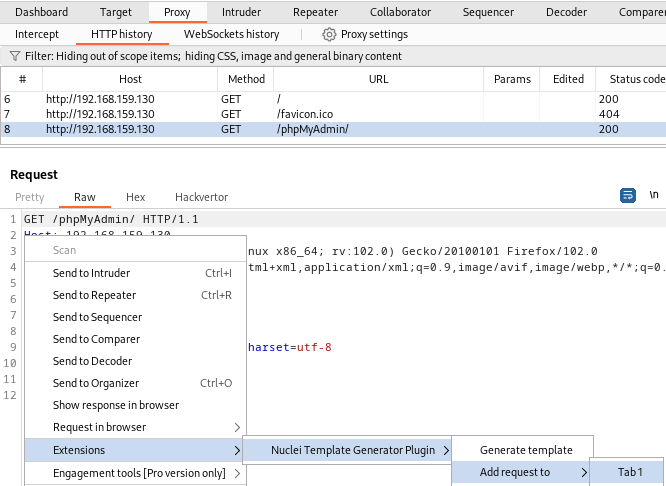
Next, I moved down to the phpMyAdmin request and did the same process with the exception of adding the request to “Tab 1” in the Nuclei tab in the proxy.
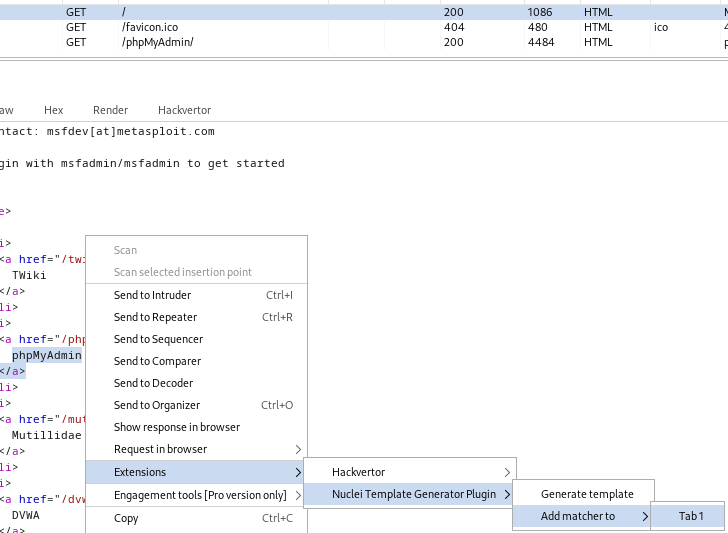
Now that multiple requests have been added to the template, it’s time to add template matchers that look for specific content in the request’s response. In the home page’s response data, I selected the anchor tag text and closing bracket of the link to the phpMyAdmin page. After the text is selected, simply right click and follow the tabs to add the matcher to “Tab 1” just like in the previous step.
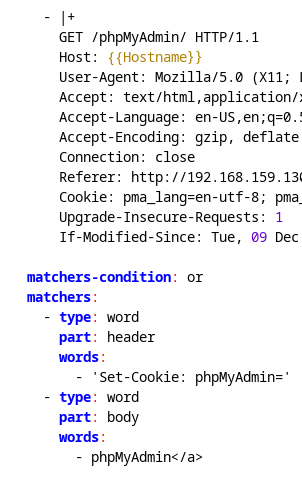
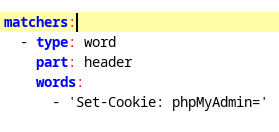
For the second phpMyAdmin request, it contains a unique signature “Set-Cookie: phpMyAdmin=” value in the cookie set in the response headers of the request. Using this response header will ensure the signature is matched even if there is a 304-response code, indicating the page is cached resulting in an empty body of data in the request.
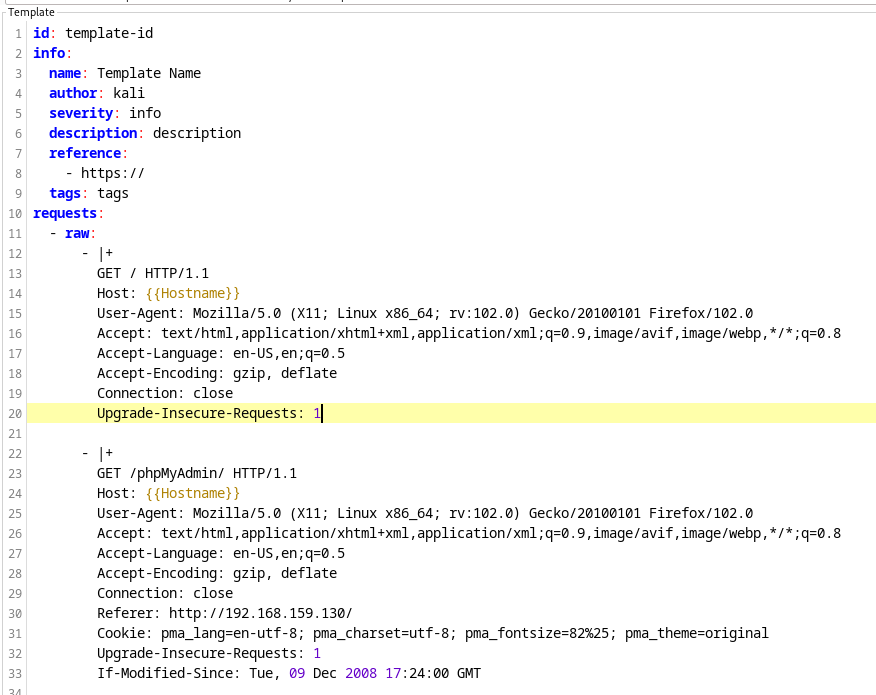
This is the template that the plugin has created thus far. It features author information, vulnerability severity, and both specified requests.
At the bottom of the template are the word-based matchers that were sent to match phpMyAdmin in the associated requests response data. Matchers also feature Boolean conditionals, so if the “matchers-condition” key is set to “and”, then both matchers would have to be present in a request for indicator alert to be raised instead of just one with the current “or” setting. According to the features specified in the plugin’s repository, the template matchers of capable of matching raw binary data or ascii-based text like in the example below.
Now that a template has been created in the default location of the “/tmp” folder (if running on Kali Linux), we can run it with the -t option and increased verbosity with the -v option.
Nuclei single template scan command:
nuclei -v -t <template_name> -u <target_url>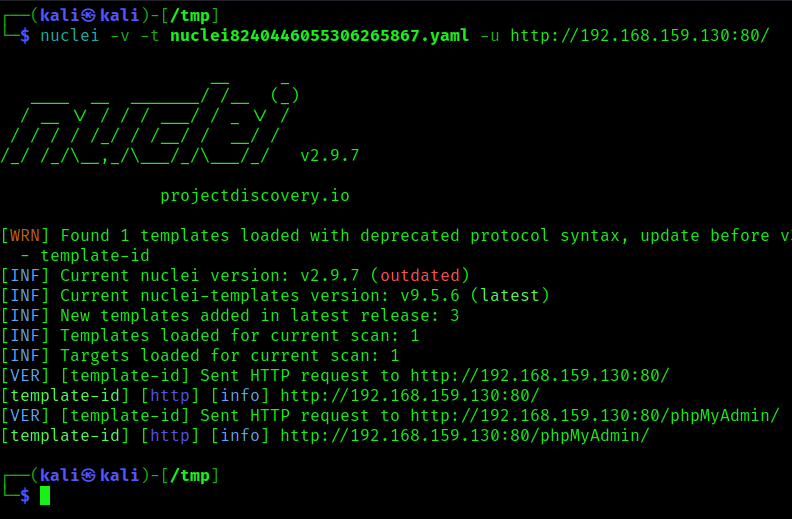
The resulting output shows that the generated template with default name of “[template-id]” matched on both targeted endpoints. Based on the output of the default nuclei scan that was initially run, there should only be one endpoint that had raised an indicator, meaning the current template is generating a false positive.
To remove the false positive, I removed the first matcher of the link anchor tag that is on Metasploitable’s homepage. I also changed the value of the id in template file to phpMyAdmin-panel to help visualize the example template.
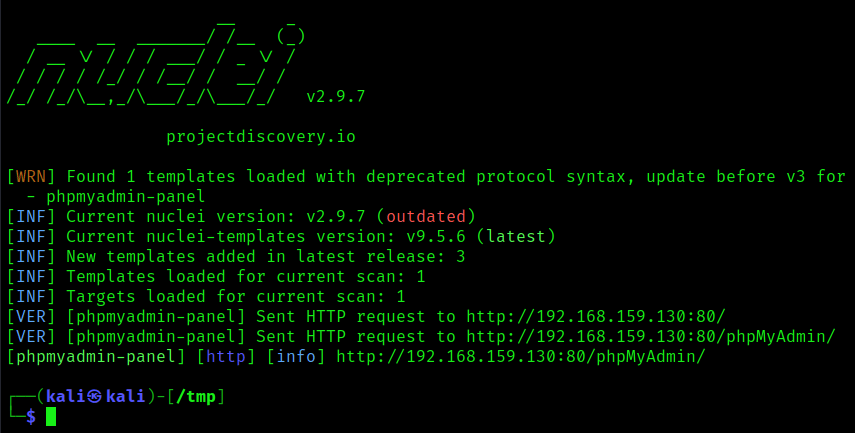
After running the scan again, it shows that multiple requests were sent but the correct /phpMyAdmin/ endpoint was the only one that indicated an alert. While this generated template is different from the one that is included by default, it was still effectively able to identify the same target alert.
The Nuclei template generator plugin also features support for CVE’s, actually attempting to look up the CVE information and automates populating it into the generated template. Back in Burp Suite, simply right click then -> Add -> Classification -> CVE which prompts for the CVE number to look up.
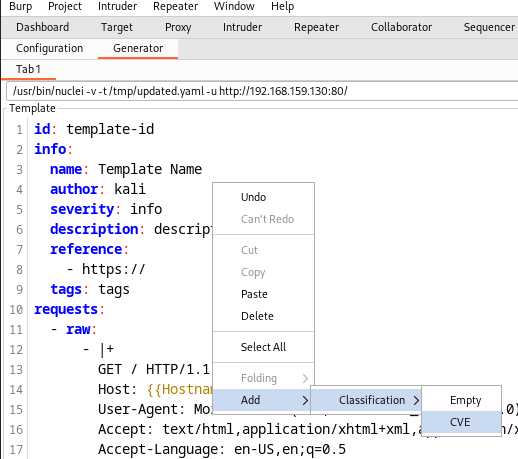
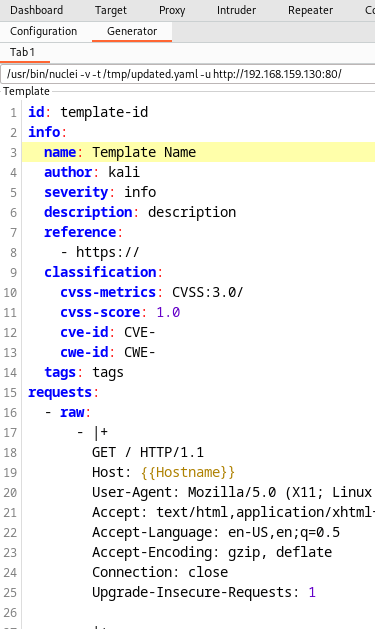
This example does not have an associated CVE so the lookup process of the bogus number I gave it failed, but still was able to generate an empty classification section in the template.
Another great feature of the plugin is the direct template integration with Burp Suite’s Intruder. After a request is sent to the Intruder and a parameter is specified, simply right click and follow the extensions tabs like in previous steps to generate a template.
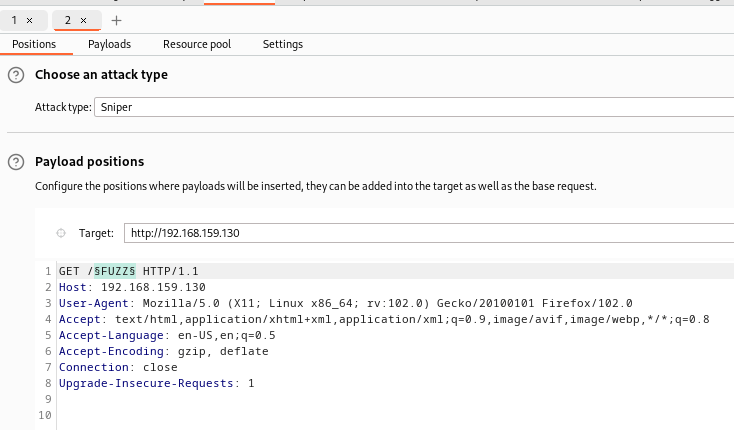
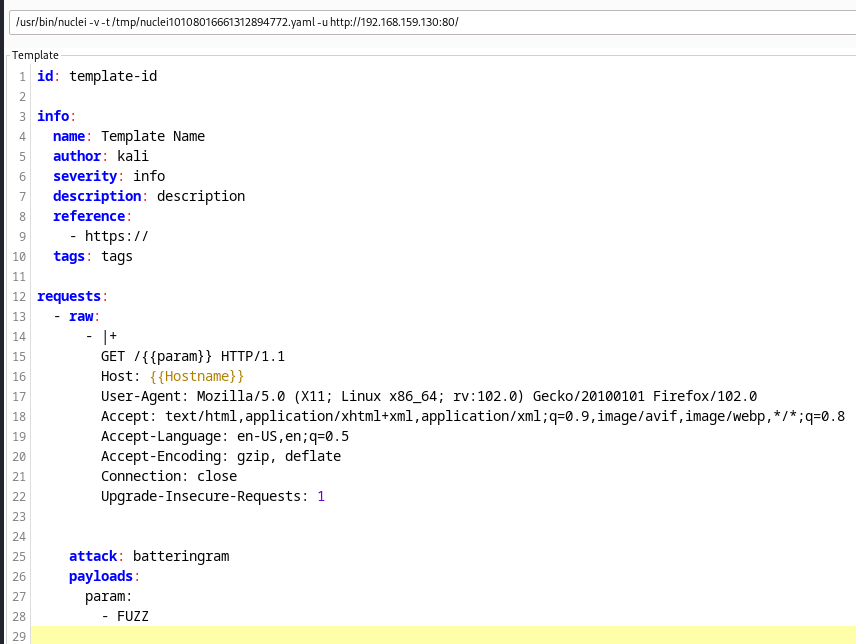
The result is a generated template featuring a battering ram attack and associated payloads. The plugin supports battering ram, cluster bomb, and pitch fork attack modes, so it will default to battering ram if sniper is set when the template is generated.
Nuclei Template Conclusion
Hopefully the information and steps provided in this guide will help your understanding of how the Nuclei template generator plugin works and why its integration with Burp Suite makes the process of template generation substantially more efficient during web app engagements. Request and response data is easily parsed from the application straight to the resulting template. The plugin also supports CVE template data and is integrated with the major Burp functionality like the Repeater, Intruder, etc. By generating additional templates and integrating them into the tools template repository, it extends the tools capabilities and allows the community to contribute to its power!
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...