When performing pentesting engagements there are times where validation of SSL/TLS ciphers, protocols, certificates, etc. is needed. One tool that our pentesting team tends to make use of is the testssl.sh command line tool that is freely available for anyone to download. In this article, we will go through the installation process and how to use the new toolset.
How To Install TestSSL.sh
Installation is pretty simple as there are a couple different options available. The first option is pulling directly from the testssl.sh website utilizing the following commands:
Latest stable code:
curl -L https://testssl.sh > testssl.nshLatest development code:
curl -L https://testssl.sh/dev/ > testssl.shThe second option is pulling the testssl.sh toolset from GitHub utilizing the following command:
git clone --depth 1 https://github.com/drwetter/testssl.sh.git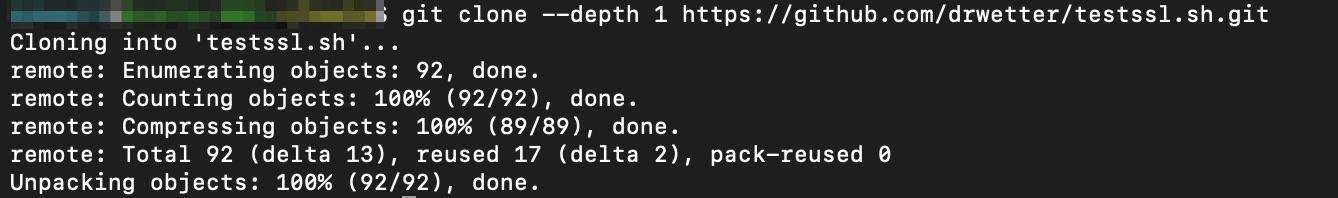
Pretty simple right? Now let’s get into using the toolset.
How Pentesters Use TestSSL.sh
This tool is one of the simplest pentesting tools to utilize and access valuable information. To start – change into the directory where the testssl.sh script is located. Let’s issue the following commands:
Standard HTTPS webserver:
./testssl.sh https://<IP or Hostname>Non-Standard SSL Ports:
./testssl.sh <IP or Hostname:PORT>Here is an example screenshot utilizing the toolset:
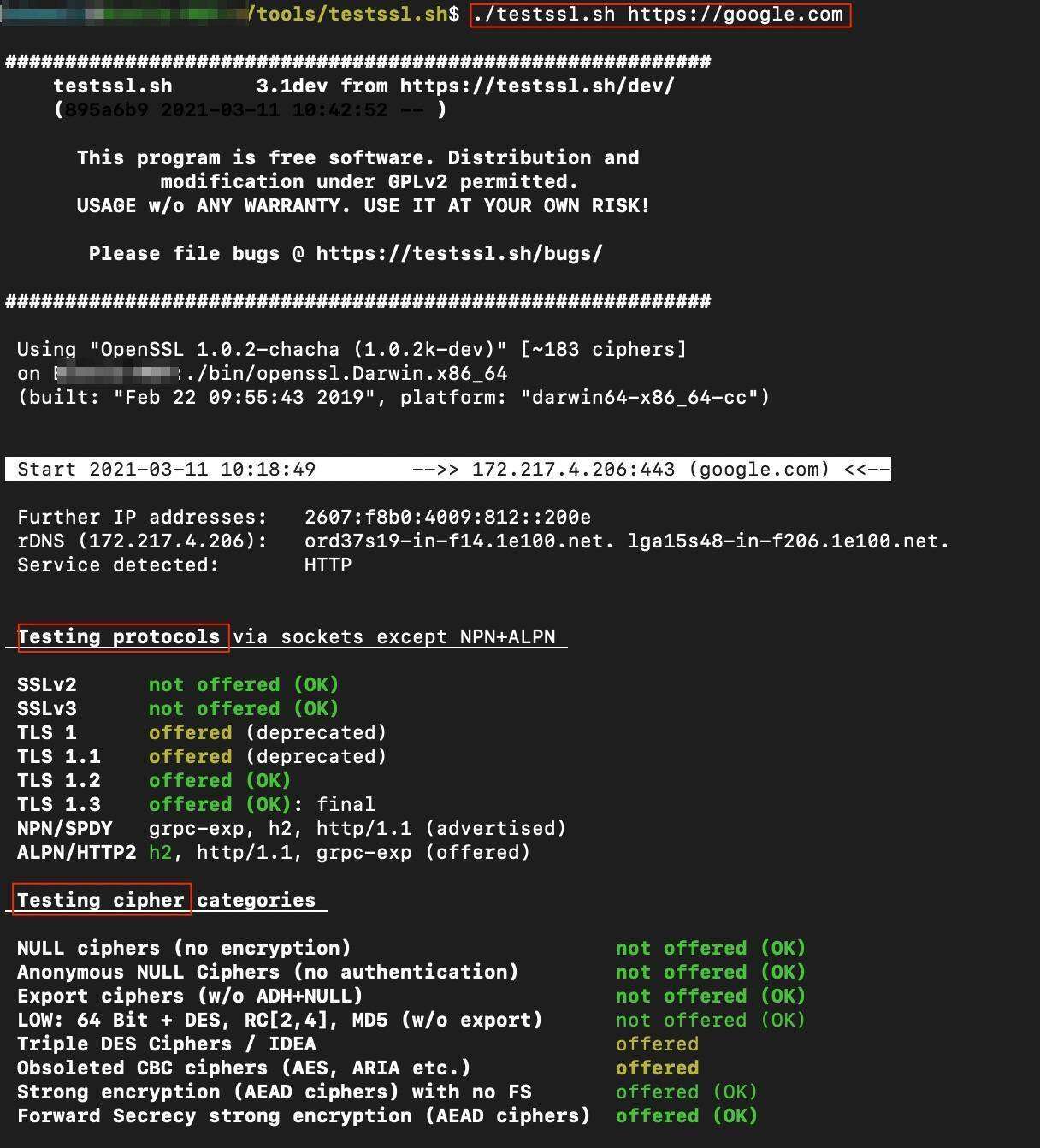
Scrolling down the output from testssl.sh – there is useful information in regards to ciphers supported, SSL certificate information, and protocols utilized.

TestSSL.sh Recap
Hopefully this blog post demonstrates how easy testssl.sh is to be installed and utilized for everyday testing. Any additional information on the toolset can be obtained from their website – https://testssl.sh/. In closing, there are many tools available that perform similar tests however we prefer this tool because it is easy to install, use, and provides clear output for reporting purposes.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...