I was recently combing through GitHub for a tool that I tend to use on mobile application penetration tests when I came across APKLeaks. I currently make use of Mobile Security Framework for discovering sensitive information within the APK files, but thought – why not try a new tool? ApkLeaks specifically scans APK files for URIs, endpoints, and secrets. Check out this accompanying video to this blog, APKLeaks Pentesting Video, for more information.
APKLeaks Installation
There are a few ways to complete the installation:
- PyPi
- pip3 install apkleaks
- Source
- git clone https://github.com/dwisiswant0/apkleakscd apkleaks/
- pip3 install -r requirments.txt
- Docker
- docker pull dwisiswant0/apkleaks:latest
I chose to do Step 1 with PyPi – a simple installation and it worked perfectly on the new Mac M1.
APKLeaks Usage
Running apkleaks from the terminal will bring up the basic help menu otherwise apkleaks -h will provide additional information on each of the flags allowed for execution.
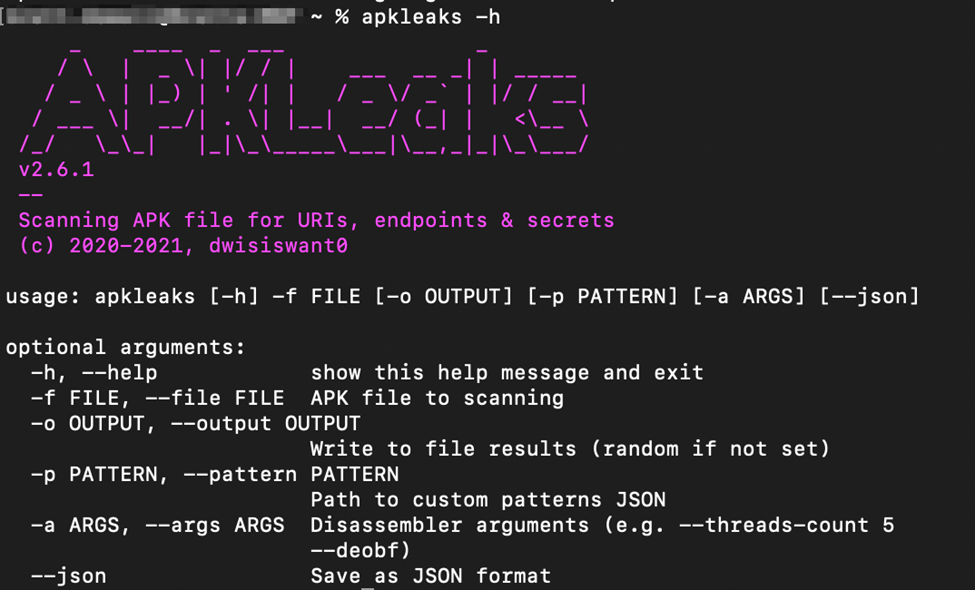
Now let’s move into some real examples – I went ahead and downloaded a couple of APK files from APKPure to test this tool against. To prevent any exposure of the application tested against – I also blurred the output of the tool, but you get the jist of it.

The above screenshot breaks down multiple categories the tool may discover items within the source code. I have noticed that quite a few of the items flagged have been false positives, however, the tool has a very high processing time that can provide additional items to review – it just makes sense to add this to my testing playbook when testing mobile applications.
MORE FROM OUR TECHNICAL BLOG
Cyber Advisors specializes in providing fully customizable cyber security solutions & services. Our knowledgeable, highly skilled, talented security experts are here to help design, deliver, implement, manage, monitor, put your defenses to the test, & strengthen your systems - so you don’t have to.
Read more from our technical experts...

