By Reed Martin and Nicolas Cuendet, Dell Coud Client-Computing
As user-owned devices become increasingly powerful, IT managers are having to make tough decisions about granting network access to enhance worker flexibility. Recent headlines detailing high-profile data breaches have only increased the tension between users hoping to leverage the latest smartphones and tablets and the need to protect corporate data and networks from these relatively insecure endpoints. Whether or not permission is granted on a case by case or policy basis, it has become clear that relying on what was once considered “good enough” security is no longer an option. Certainly, mobile devices can pose a risk to corporate networks and data are not going away.
While IT managers might want to let top management access corporate email or applications from personally-owned tablets connecting via their WEP secured home networks, they probably don’t want to grant nearly frictionless access to every employee hoping to connect via airport wi-fi service or coffee shop router.
Active Directory, which may seem like the easiest solution, is limited since it can only be leveraged to grant or block network access with a handful of specific parameters.
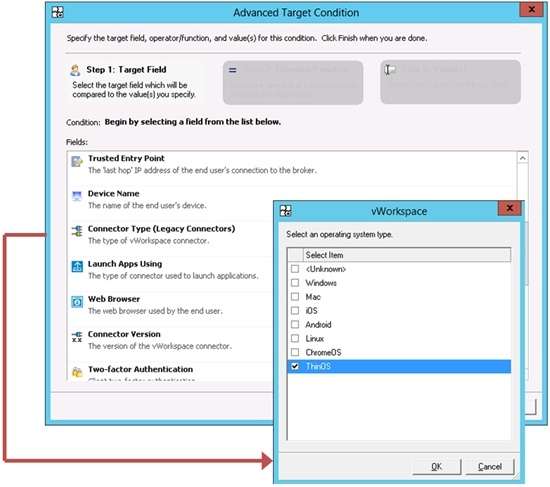
So what is the best way to protect enterprise networks and corporate data from vulnerable user devices in the short run? The Dell Cloud Client-Computing group proposes an effective and granular solution: the advanced targeting feature that comes with Dell Wyse vWorkspace, Dell’s simple, flexible and high-performance desktop virtualization software. These advanced targeting capabilities allow IT managers to set very specific user access parameters to virtual desktops and applications.
These parameters can be based on several fields that can be combined as needed to retain control of user access without having to deploy a costly third-party appliance. vWorkspace does not eliminate the need for Active Directory but works with the familiar functionality that Active Directory provides, to deliver a superior solution to your security-conscious IT department while enabling user flexibility and network access.
Based on variables such as user credentials, that user’s physical location, IP address, and time of access, vWorkspace allows authorized employees to enjoy secure, flexible access to the data and applications they need to maximize their productivity. vWorkspace also lets your IT managers combine relevant parameters and multiple layers of user classification to enforce policy-based permissions and context-aware access. The added benefit is that vWorkspace also allows you to define access to virtual desktops, applications, or individual resources such as printers, storage, drive maps, user subnets, or any other resource within a Windows environment.
For example, access can be granted based on user group and time of day combined with device name, the device’s operating system, and/or any relevant combination. Access and specified drive mapping can also be granted based on a user’s location to prevent users from logging in to certain applications or accessing sensitive data from outside the corporate network or outside an approved VPN.
Setting and Enforcing Flexible BYOD Policies
Deploying virtual desktops using vWorskpace allows your IT department to introduce and enforce new BYOD policies that protect your data by managing access without having to invest in a canopy of overlapping security measures. Specifically, with Advanced Targeting, IT managers can grant, deny or control access to specific virtual desktops, data sets or applications based on any or all the following criteria:
- User’s identity and domain
- User’s group, Organization Unit (OU)
- Device address: the IP address of the end user’s device
- Trusted entry point: the “last hop” IP address of the end user’s connection to the broker
- Device name: the name of the end user’s device
- The type or version of the vWorkspace connector used to connect
- The browser used by the end user
- Operating system of the end user’s device
- Client two-factor authentication
- Date / day of the week / time of the day
- The vWorkspace Web Access site name
These can be combined as a set of Boolean (AND/OR) rules. vWorkspace is one of the only connection brokers on the market which includes such a feature built into the software at no extra cost.
Using these highly-configurable settings in vWorkspace to leverage Advanced Targeting, you can now implement individual or overlapping automated policies that monitor and grant access to any area of the network. This capability protects your network based on parameters you decide, providing more granularity than the traditional user identity and grouping provided by AD.
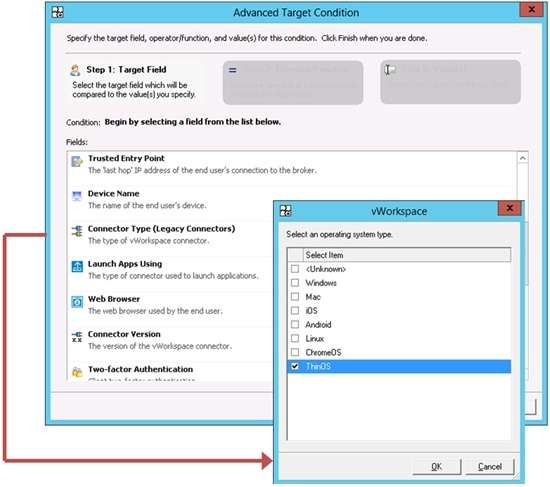
How Advanced Targeting Works
vWorkspace’s advanced targeting feature is based on identifying and approving each user’s source IP address. The IP subnet provides a trusted entry point and can be defined to enable remote logins from a remote gateway. This enables your IT department to approve access to applications and drive paths while limiting user access to others. Advanced Targeting can also allow your IT staff to block application access to anyone logging in from outside the network or limit access from users logging in from areas of the network that are not entirely secure. vWorkspace helps your IT team assign drive mapping and enforce specific policies related to resources that specific users are allowed to access.
Use Cases for Advanced Targeting
- Nurses’ stations with endpoints that require secure access related to U.S. Federal HIPAA regulations for handling patient data. Hospitals typically assign applications to physical locations such as a nurse’s station rather than assigning them to specific individuals.
- State and local police stations that are granted shared access to restricted access databases. Federal regulations limit the use of certain national criminal databases to approved individuals and only-accessed over specific, approved endpoints within secure areas of a law enforcement facility.
- Academic environments where students can access applications using an academic license that has specific limitations. For example, students may be able to access and use otherwise cost-prohibitive design applications as long as they are accessed from on-campus computer labs and not from dorm rooms.
- Management consultants may need access to standard business applications, the Internet, and some limited network access. Even so, IT departments of companies hiring consultants and granting them access to the network, may want to limit access to business accounting software or other sensitive applications.
Each of these discrete configuration choices are defined as “targets” or “target expressions” that can be combined to create specific even granular parameters for granting or restricting network or data access. vWorkspace can enable your IT department to set flexible and policy-based access parameters without having to touch user endpoints.
Conclusion
vWorkspace’s connection broker offers a unique form of multi-dimensional control called Advanced Targeting out of the box without the need for software scripting or specialized IT personnel. Whether your goal is to grant or limit access based on location, roll out a VDI production deployment, or launch a secure BYOD program, setting limits and establishing approved access is facilitated by vWorkspace. It also allows IT professionals to use software to enforce access policies in a world of increasingly individualized access that is constantly being upended by new devices and new demands for worker flexibility.
For more information, visit www.dell.com/wyse/vWorkspace or contact us.